What is CozyDuke
CozyDuke - also known as CozyBear, CozyCar and Office Monkeys (among others), and whose activity appears to align with advanced persistent threat APT29 - is a threat actor which came to prominence in 2014 when it is believed to have staged a series of precise attacks on high profile targets including the US White House, Department of State and the Democratic National Committee.
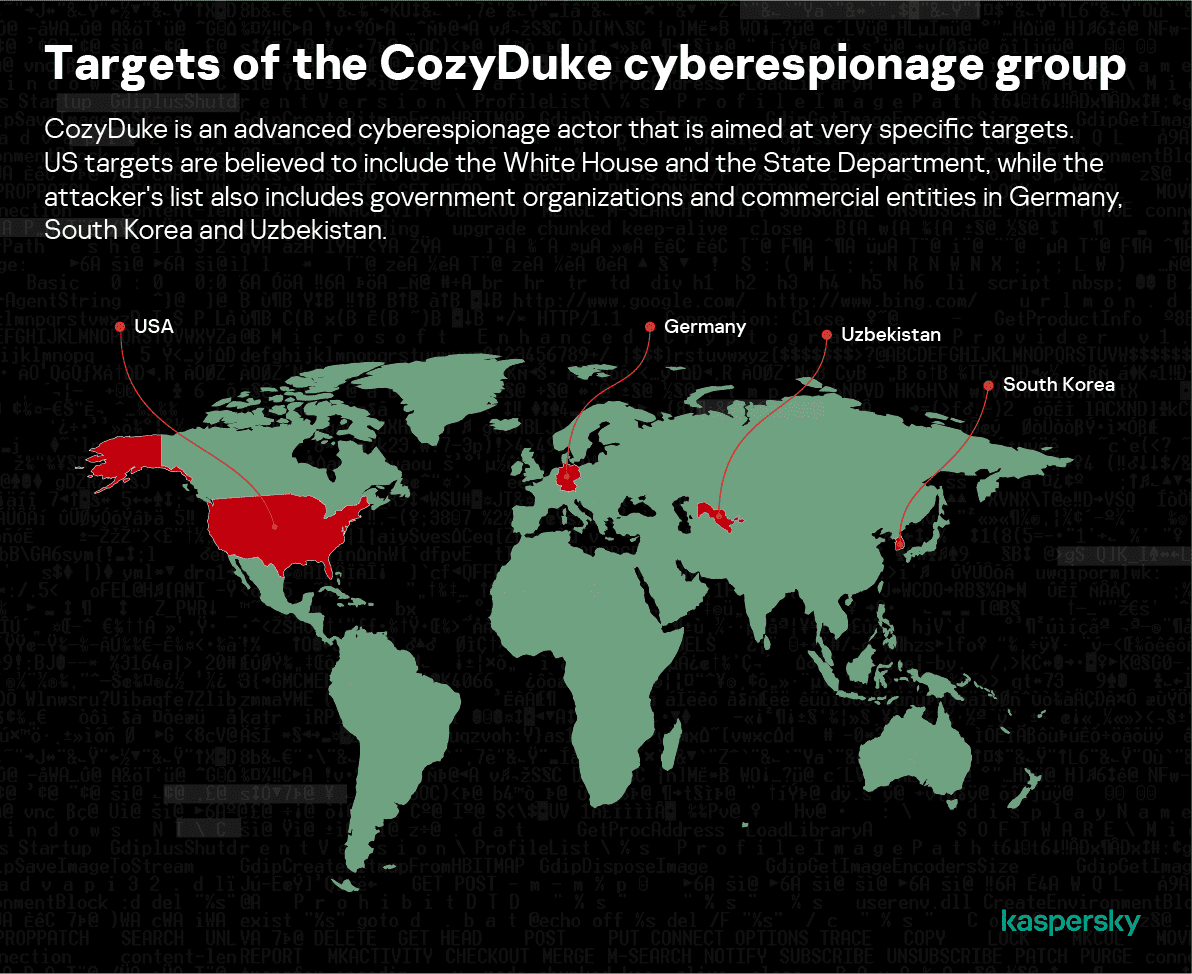
The actor hunts for confidential information stored in the networks of governmental organizations, political groups and think tanks, as well as various individuals involved in defense and geopolitical related research. Kaspersky’s Global Research and Analysis Team (GReAT) has observed signs of its attacks in several countries including Germany, South Korea and Uzbekistan, as well as the US. Among the group’s most interesting characteristics are:
- Its extremely sensitive, high profile victims and targets
- Its evolving crypto and anti-detection capabilities
- Strong functional and structural similarities linking its malware toolset to early MiniDuke and more recent CosmicDuke and OnionDuke components
A relative of MiniDuke?
In early 2013, GReAT observed several incidents that were so unusual they suggested the existence of a new, previously unknown threat actor. What the team uncovered was that the former MiniDuke attackers were still active, and using extremely effective social engineering techniques involving sending malicious PDF documents to compromise their victims.
The PDFs used highly relevant, well-crafted content that fabricated human rights seminar information and Ukraine’s foreign policy and NATO membership plans, and were rigged with exploits attacking Adobe Reader versions 9, 10 and 11, bypassing its sandbox.
Once a system was exploited a unique downloader was dropped onto the victim’s disk, containing a customized micro backdoor written in Assembler.
If the target system met predefined requirements, the malware used Twitter to look for specific tweets from pre-made accounts created by MiniDuke’s command and control (C2) operators, with specific tags labeling encrypted URLs for backdoors. The URLs provided access to the C2s, along with commands and encrypted transfers of additional backdoors onto the system via GIF files.
A month later, GReAT discovered two more previously unknown infection mechanisms for MiniDuke, which relied on Java and Internet Explorer vulnerabilities to infect the victim’s PC.
After Kaspersky’s reports of these attacks, the rest of 2013 saw reduced intensity of the campaign. But then, following an upsurge in attacks in the second half of 2014, GReAT characterized MiniDuke, CosmicDuke and the actor’s Nemesis Gemina project - targeting government, diplomatic, energy, military and telecom operators - as ‘one of the world’s most unusual APT operations’ due to:
- Its use of a customized backdoor written in Assembler using ‘old school’ virus writing techniques and habits
- A unique C2 mechanism that uses multiple redundancy paths, including Twitter accounts
- Stealthy transfer of updates as executables hidden inside GIF files (a form of steganography)
How CozyDuke attacks
The CozyDuke malware utilizes a backdoor and dropper, and exfiltrates data to a C2 server. CozyDuke droppers and spyware components often maintain fairly common characteristics, but the files’ functionality is slightly modified depending on the actor’s needs.
In 2015 GReAT reported that CozyDuke often spear phishes targets with emails containing a link to a hacked website. Sometimes this was a high profile, legitimate site such as ‘diplomacy.pl’ hosting a ZIP archive. The archive contained a RAR SFX which installed the malware and showed an empty PDF decoy.
In other highly successful runs, the actor sent out phony Flash videos directly as email attachments. A clever example was ‘Office Monkeys LOL Video.zip’. The executable within this not only played a very funny video, but dropped and ran another CozyDuke executable. The videos were quickly passed around offices while users’ systems were silently infected in the background, and many of the APT’s components were signed with phony Intel and AMD digital certificates.
The file collected system information, and then invoked a WMI instance in the rootsecuritycenter namespace to identify security products installed on the system before dropping more data collection malware. The code hunted for several security products to evade – including Kaspersky.
Also in 2015, GReAT identified the Minidionis threat (known by Kaspersky as CloudLook) to be another backdoor from the same APT actor – this time using a cloud drive capability to store and download malware onto infected systems using a multi-dropper scheme.
To get in, the attacker used spear phishing emails with a self-extracting archive attachment pretending to be a voicemail. When the victim opened an archive, a second stage dropper executed and a WAV file played like a real voicemail. In its spear phish, CloudLook also used a self-extracting archive containing a PDF file that lured its victims with information regarding world terrorism.
New Dukes
In November 2016, Volexity documented new Dukes-related activity involving spear phishing with links to a ZIP archive containing a malicious LNK file, which would run PowerShell commands to install a new custom backdoor called PowerDuke. Although this wave did not use any zero day exploits, it relied on steganography and NTFS alternate data streams to complicate detection. According to Kaspersky telemetry, targeted organizations included think tanks and individuals working in various areas related to security and geopolitics.
Another wave of suspected Dukes attacks was identified in November 2018 by FireEye, this time again relying on Windows LNK files and deploying Cobalt Strike. Attribution to the Dukes was made partly on the LNK file structure and other TTPs, including the targets of the attack. According to Kaspersky telemetry, targeted organizations included political bodies in Europe.
In October 2019, ESET published “Operation Ghost” detailing a set of new trojans used by the Dukes, including PolyglotDuke, RegDuke and FatDuke. Created between 2017 and 2019, these fill a gap in the Dukes’ activity, proving a continued, under the radar presence.
Further details
- APT29: MITRE description
- The CozyDuke APT: GREaT report
- Minidionis – one more APT with a usage of cloud drives
- Miniduke is back: Nemesis Gemina and the Botgen Studio
- The MiniDuke Mystery: PDF 0-day Government Spy Assembler 0x29A Micro Backdoor
- Miniduke: Web Based Infection Vector
More details about CozyDuke are available to customers of Kaspersky Intelligence Reporting. For more information, contact: intelreports@kaspersky.com