The desire to remain anonymous online is as old as the internet itself. In the past, users believed hiding behind a nickname meant they could badmouth their neighbors on local forums with impunity. Now, such trolls can be identified in seconds. Since those early days, technology has taken a quantum leap: distributed networks, anonymous browsers, and other privacy tools have emerged. One of these tools, which was heavily promoted a decade ago by former NSA contractor Edward Snowden, is the Tor Browser, where “TOR” is an acronym for “The Onion Router”.
But in today’s world, can Tor truly provide complete anonymity? And if it doesn’t, should we just forget all about anonymity and rely on a regular browser like Google Chrome?
How Tor users are deanonymized
If Tor is new to you, check out our vintage article from way back when. There, we answered some common questions: how the browser ensures anonymity, who needs it, and what people usually do on the dark web. In brief, Tor anonymizes user traffic through a distributed network of servers, called nodes. All network traffic is repeatedly encrypted as it passes through a number of nodes between two communicating computers. No single node knows both the origin and destination addresses of a data packet, nor can it access the packet’s content. OK, short digression over — now let’s turn to the real security threats facing anonymity enthusiasts.
In September, German intelligence services identified a Tor user. How did they do it? The key to their success was data obtained through what’s called “timing analysis”.
How does this analysis work? Law enforcement agencies monitor Tor exit nodes (the final nodes in the chains that send traffic to its destination). The more Tor nodes the authorities monitor, the greater the chance a user hiding their connection will use one of those monitored nodes. Then, by timing individual data packets and correlating this information with ISP data, law enforcement can trace anonymous connections back to the end Tor user — even though all Tor traffic is encrypted multiple times.
The operation described above, which led to the arrest of the administrator of a child sexual abuse platform, was possible partly because Germany hosts the highest number of Tor exit nodes — around 700. The Netherlands ranks second with about 400, and the US comes in third with around 350. Other countries have anywhere from a few to a few dozen. International cooperation among these top exit-node countries played a significant role in deanonymizing the child sexual abuse offender. Logically, the more nodes a country has, the more of them can be state-monitored, increasing the likelihood of catching criminals.
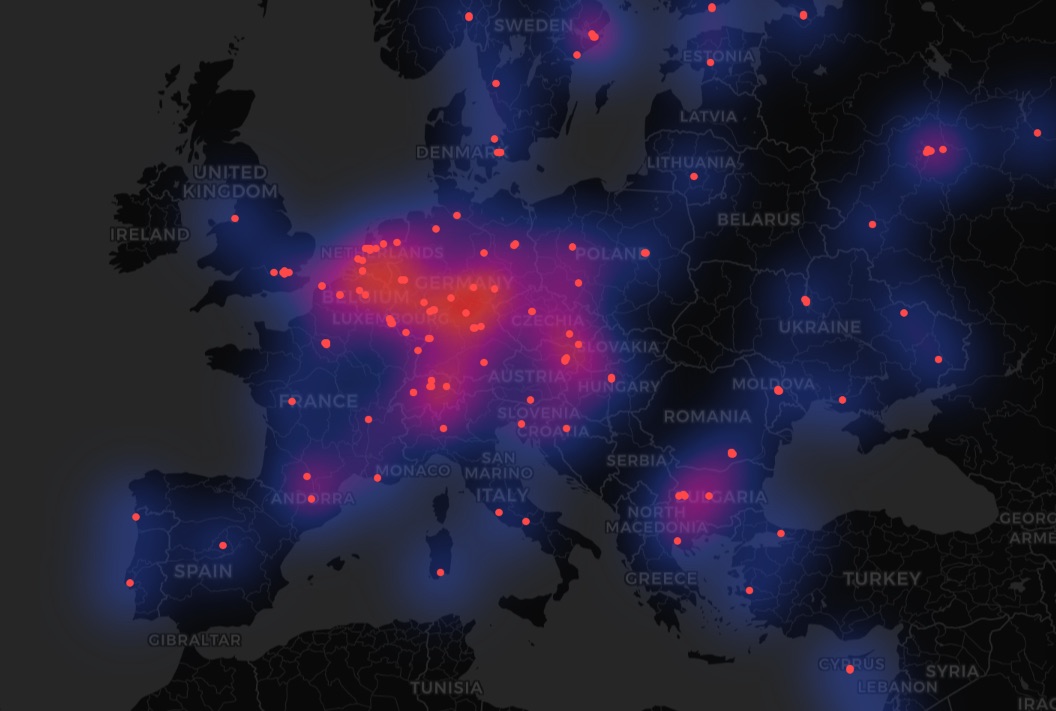
Germany and the Netherlands are among the leaders on the number of Tor exit nodes — not only in Europe but worldwide. Source
The Tor Project responded with a blog post discussing the safety of their browser. It concludes that it’s still safe: the de-anonymized individual was a criminal (why else would authorities be interested?), using an outdated version of Tor and the Ricochet messaging app. However, Tor noted it wasn’t given access to the case files, so their interpretation regarding the security of their own browser might not be definitive.
This kind of story isn’t new; the problem of timing attacks has long been known to the Tor Project, intelligence agencies, and researchers. So although the attack method is well-known, it remains possible, and most likely, more criminals will be identified through timing analysis in the future. However, this method isn’t the only one: in 2015, our experts conducted extensive research detailing other ways to attack Tor users. Even if some of these methods have become outdated in the forms presented in that study, the principles of these attacks remain unchanged.
“Generally it is impossible to have perfect anonymity, even with Tor”.
This phrase opens the “Am I totally anonymous if I use Tor?” section of the Tor Browser support page. Here, the developers provide tips, but these tips can at best only increase the chances of remaining anonymous:
- Control what information you provide through web forms. Users are advised against logging in to personal accounts on social networks, as well as posting their real names, email addresses, phone numbers, and other similar information on forums.
- Don’t torrent over Tor. Torrent programs often bypass proxy settings and prefer direct connections, which can de-anonymize all traffic — including Tor.
- Don’t enable or install browser plugins. This advice also applies to regular browsers, as there are many dangerous extensions out there.
- Use HTTPS versions of websites. This recommendation, incidentally, applies to all internet users.
- Don’t open documents downloaded through Tor while online. Such documents, the Tor Project warns, may contain malicious exploits.
With all these recommendations, the Tor Project is essentially issuing a disclaimer: “Our browser is anonymous, but if you misuse it, you may still be exposed”. And this actually makes sense — your level of anonymity online depends primarily on your actions as a user — not solely on the technical capabilities of the browser or any other tool.
There is another interesting section on the Tor support page: “What attacks remain against onion routing?” It specifically mentions possible attacks using timing analysis with the note that “Tor does not defend against such a threat model”. However, in a post about the German user’s de-anonymization, the developers claim that an add-on called Vanguard, designed to protect against timing attacks, has been included in Tor Browser since 2018, and in Ricochet-Refresh since June 2022. This discrepancy suggests one of two things: either the Tor Project hasn’t updated its documentation, or it’s being somewhat disingenuous. Both are problematic because they can mislead users.
So what about anonymity?
It’s important to remember that Tor Browser can’t guarantee 100% anonymity. At the same time, switching to other tools built on a similar distributed node network structure is pointless, as they are equally vulnerable to timing attacks.
If you’re a law-abiding individual using anonymous browsing simply to avoid intrusive contextual ads, secretly shop for gifts for loved ones, and for other similarly harmless purposes, the private browsing mode in any regular browser will probably suffice. This mode, of course, doesn’t offer the same level of anonymity as Tor and its counterparts, but it can make surfing the net a bit more… well, private. Just make sure you fully understand how this mode works in different browsers, and what it can and can’t protect you from.
In addition, all of our home security solutions include Private Browsing. By default, this feature detects attempts to collect data and logs them in a report but doesn’t block them. To block data collection, you need to either enable Block data collection in the Kaspersky app or activate the Kaspersky Protection plugin directly in the browser.
Besides this, our protection can also block ads, prevent the hidden installation of unwanted apps, detect and remove stalkerware and adware, and remove traces of your activity in the operating system. Meanwhile, the special component Safe Money provides maximum protection for all financial operations by conducting them in a protected browser in an isolated environment and preventing other apps from gaining unauthorized access to the clipboard or taking screenshots.
Double VPN
You can also stay anonymous on the internet using Kaspersky VPN Secure Connection that support Double VPN (also known as multi-hop). As the name suggests, this technology allows you to create a chain of two VPN servers in different parts of the world: your traffic first passes through an intermediary server, and then through another. Double VPN in Kaspersky VPN Secure Connection uses nested encryption — the encrypted tunnel between the client and the destination server runs inside a second encrypted tunnel between the client and the intermediary server. Encryption in both cases is only performed on the client side, and data is not decrypted on the intermediary server. This provides an additional layer of security and anonymity.
Double VPN is available to users of Windows and Mac versions of Kaspersky VPN Secure Connection. Before enabling Double VPN, make sure that the Catapult Hydra protocol is selected in the application settings: Main → Settings (gear icon) → Protocol → Select automatically, or Catapult Hydra.
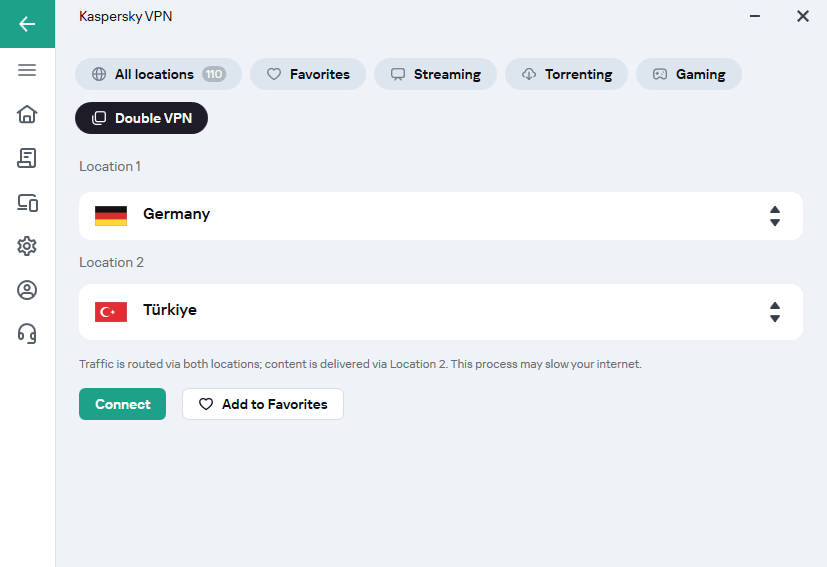
After that, you can enable Double VPN:
- Open the main application window.
- Click the Location drop-down to open the list of locations of VPN servers.
- Click the Double VPN
- Select two locations and click Connect.
You can add your Double VPN server pair to Favorites by clicking the Add to Favorites button.
Congratulations! Now your traffic is encrypted more securely than usual — but remember that these traffic encryption methods are not intended for illegal activities. Double VPN will help you conceal personal information from data-gathering sites, avoid undesirable ads, and access resources unavailable in your current location.
 tor
tor

 Tips
Tips