
False Perceptions of IT Security: Predicting the Future!
We tend to think that protecting ourselves against future threats is most important. But, perhaps we need to take a step back and solve some of the major problems that we already know about.
435 articles

We tend to think that protecting ourselves against future threats is most important. But, perhaps we need to take a step back and solve some of the major problems that we already know about.

There are some good reasons to spend years researching high-profile cyberthreats. But we do our best to protect our customers from the latest threats even before the investigation has concluded. Here’s how.

1 in 8 people don’t believe that cyberthreats are real. The threat may go away if you turn your back to it in a dream, but that won’t work in reality.

Apple malware targets iOS by infecting OS X machines and then swapping legitimate apps for malicious ones as soon as an iOS device connects via USB.

A critical civilian system goes down – it’s a scenario that evokes some apocalyptic pictures of destruction and mayhem; remember, for instance, “Die Hard 4.0”? Actually this could happen with any corporate infrastructure, since all of them have certain critical systems of their own.

Can a business be “partially” prepared to ward off cyberthreats? That’s up for debate, but it seems there is little difference between “partial protection” and no protection at all.

Kaspersky Lab’s recent survey surprisingly found that e-commerce, online retailers and financial service providers are not just the biggest sources of stolen financial data, but also feel just a bit too lax about security. However, this has some severe implications.

Brian Donohue and Chris Brook recap the month’s security headlines from its beginnings at Black Hat and DEFCON, to a bizarre PlayStation Network outage.

Kaspersky Lab released results of a 10-months long analysis of Epic Turla APT campaign, which is still active. One of the most sophisticated cyber-espionage campaigns, it attacked victims in 45 countries.

Kaspersky Lab has just released a new report on the evolution of threats in Q2. Banking Trojans grow in numbers (and the level of danger they pose), while Russia remains the most malware-attacked country.

A visual representation of a problem appears just a bit more meaningful, and at the same time more comprehensible, than large sheets of texts. Here is a big (or not so big) picture of threats to medium-sized businesses.

DoS/DDoS attacks is another popular, but somewhat under explained, term in cybersecurity. Explaining it in detail would take a monograph, so we’ll just hit the high points.

The first quarter of 2014 has passed, so Kaspersky Lab’s researchers have released their quarterly report on IT threat evolution for the first three months of 2014. It’s quite an

The concept of mobile malware working in bond with computer Trojans to steal money via online banking is not new, however Kaspersky Lab Q1 report indicates that it quickly gaining “market share”.

The Heartbleed bug was huge news last week and still is. As a hobbyist programmer, I am saddened that attention to the art of software-making was brought on as a
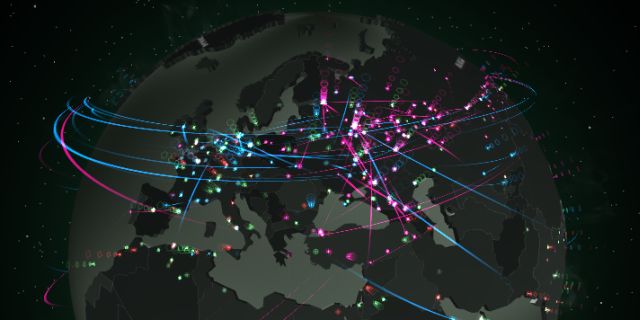
Kaspersky Lab presents its new interactive Cyberthreats Realtime Map. Living up to its name, this visual tool allows users to see what is going on in cybersecurity around the world

You have a particularly high chance of encountering fake news on April Fool’s Day. In addition to joking headlines of mainstream media outlets, you can encounter a link to dedicated

Apple in Disgrace In late February, researchers detected a couple of major problems with the operating systems Apple iOS and Mac OS X. The iOS version 7.06 update restored some

Malware inflicts damage to your system, yet is ephemeral and rarely visible to the naked eye, especially in digital domains beyond your own PC. But nevertheless, you have an opportunity

With each passing year, the mobile malware landscape continues to evolve. It’s now driven by groups of criminals working to carry out large scale attacks and earn substantial profits. There