
How to Tweak Fraudsters’ Noses When Buying Second-Hand iPhones
Whether you’re buying or selling a secondhand Apple device, you can be fooled by criminals. We have gathered tips on how to minimize your chances of being taken by such frauds.
158 articles

Whether you’re buying or selling a secondhand Apple device, you can be fooled by criminals. We have gathered tips on how to minimize your chances of being taken by such frauds.

As is, a QR code can quickly take you to a site or another resource but not necessarily to the one you really want to visit. Thus Kaspersky Lab offers a free and safe QR scanner!

Are you getting enough sleep at night? If not, it might be because your sleep pattern is disrupted due to the display on your PC, TV, tablet, and smartphone.
We collected the 10 best tweets related to an IT security event in 2014.

We have seen a number of cases where a user has deleted our product for Android and ended up with a locked device. Here we discuss why this happens and what can be done about it.

Let’s take a moment to discuss the numerous troubles that our bright, technology-packed future could bring about.

By default, your iPhone’s OS is set to give you the best performance instead of the best battery life. But you can change that!

This is how a seemingly simple SIM card in your smartphone can contribute to the loss of money and personal data.

It’s not always easy to give general advice to Android users because the OS is so very diverse. But we have ten security tips that are relevant for almost any Android version.

Using an in-room tablet in a hotel is an easy way to share your precious private data with the whole world and make it public.
Hotels offer not just free WiFi but occasionally even free use of devices such as iPads these days. While it is really nice, a misconfigured device like this may store just a bit too much personal data, easily retrievable by the next visitor…

Hacking and espionage are hardly crimes for the secret service, but rather are a part of their everyday work. But imagine what could happen if their tools end up in wrong hands.

IT staff of various companies complain that employees are slow to report losing their mobile devices. Thanks to BYOD, the responsibility for those devices now appears to be shared.

A while ago we “celebrated” 10 years since the first smartphone malware emerged. While we made the first Symbian antivirus in 2004, it doesn’t mean that we had no mobile security products before that. It was hard to unearth and boot an antique handheld from early 2000s, and even harder to find, install and launch our old software. Yes, it’s long obsolete, but there’s a reason for all these efforts. Read about it in our new blog post.

When shopping, we sometimes get so carried away that we forget to keep track of our belongings. Pickpockets take advantage of our carelessness and steal items like our smartphones while

Today we cannot imagine life without a smartphone. It serves as a place to store not only music and videos, but also important notes and data. If a phone is

Protect your personal data on your mobile device with Kaspersky Internet Security for Android. If your device is lost you can wipe data to remain secure.

Reports emerged earlier this week that the Starbucks’ iOS mobile application could be exposing the personal information of any customers that downloaded it. To their immense credit – especially considering
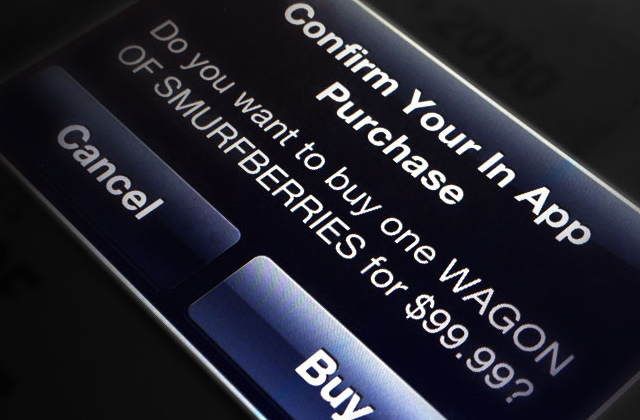
In-app purchases are the Holy Grail of revenue for app producers, especially those who make free gaming apps. The hook is that you love the game so much once you

The newly released Android 4.4 features a tasty new codename (KitKat), some design improvements, revamped Contacts and Hangouts apps, and, of course, several security-related changes. So, how much more secure