If an advanced tech user finds themselves becoming suspicious when a partner knows too much about you, they may start looking for a secret surveillance software on their own devices. However, what they might not know is that, in some cases, the perpetrator is notified if their victim performs a device scan, or removes a stalkerware app when it is discovered. If this happens, it can lead to an escalation of the situation and further aggression. That’s why, Kaspersky provides users with different tools for checking their mobile device system, including tools that do not require installation or an on-system scan.
There are at least three tactics a user can try to detect stalkerware on their device. However in all cases, we recommend that those affected should start by reaching out to local support organizations to discuss ways of dealing with the situation. It is best to use a different device for this interaction and make sure the phone with suspected stalkerware is out of reach.
In the special Get Help — > Resources section on the Coalition Against Stalkerware website, you can find a list of organizations in many countries that offer help or can guide you towards the help you need.
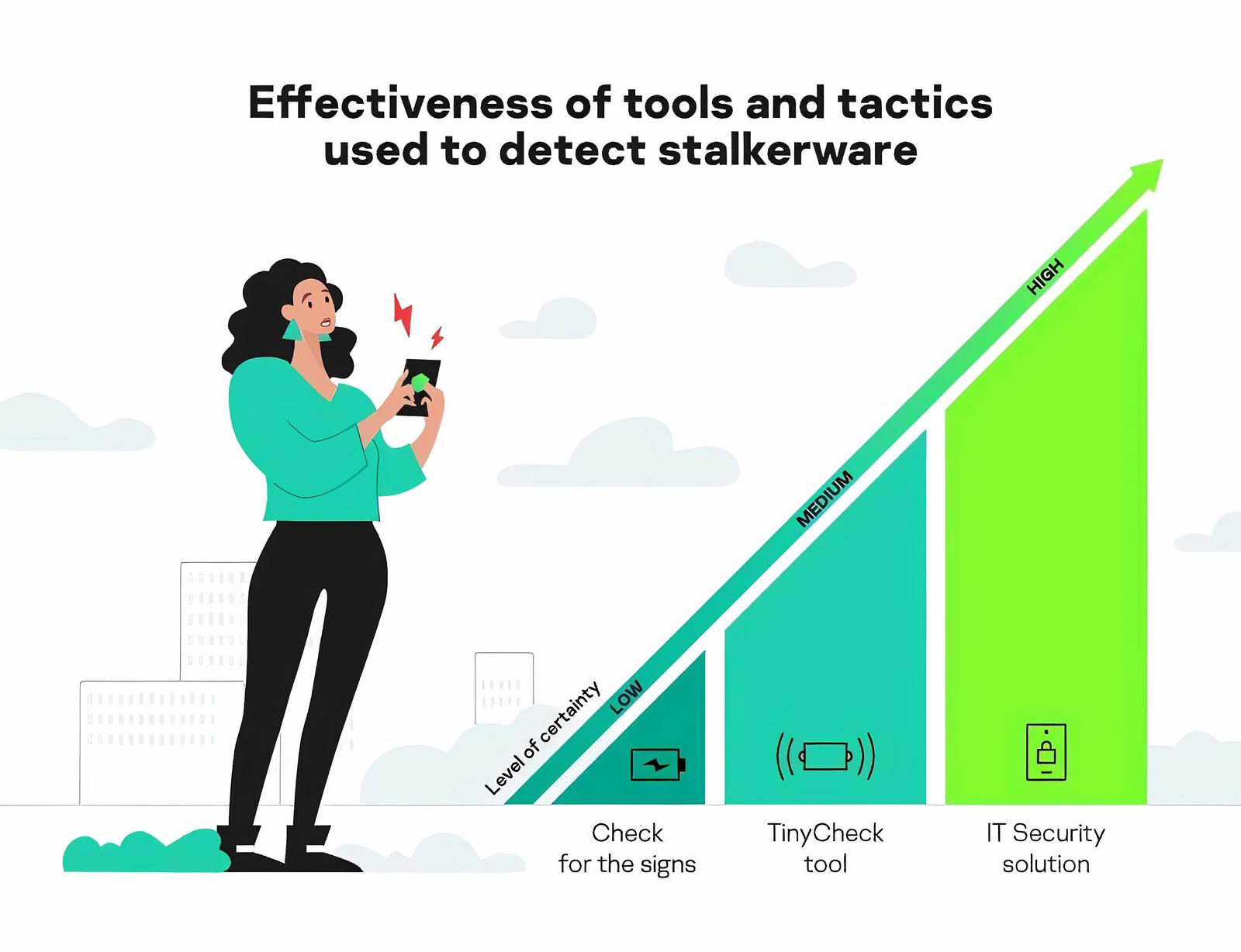
1. Check the signs of stalkerware being installed
Low level of certainty, no installation required
Keep an eye out for the following warning signals (bear in mind signs are not limited to just these): a fast-draining battery used up by unknown or suspicious apps; increased mobile data traffic; newly-installed applications with suspicious access to use and track your location, send or receive text messages, and other personal activities. If an app does not need location permission, you can simply revoke it on all modern versions of Android. Also check your “unknown sources” settings. If the allow unknown sources option is enabled on a device, it might be a sign that unwanted software were installed from a third party source. The following information shows how to perform such checks on an Android 8 device (later versions do not differ significantly) and an iOS device.
A longer list of signs can be found on the Coalition Against Stalkerware website.
In terms of efficiency, users should understand that discovering the above signs are just symptoms of possible stalkerware installation, not a true indication.
2. Use the TinyCheck tool
Medium level of certainty, no installation required
In November 2020, Kaspersky released a free anti-stalkerware tool called TinyCheck, developed by one of its researchers, Félix Aimé. The goal of TinyCheck is to help non-profit organizations support victims of domestic violence and protect their privacy. With this in mind, the tool was created with a unique feature: it is able to detect stalkerware and inform the affected user without making the perpetrator aware. No application has to be installed on the device itself to perform the check, and the results of the check are not displayed on or transmitted to the potentially infected device. In addition, TinyCheck allows you to check any device, regardless of whether it uses iOS, Android or any other OS. These two points address two major issues in the fight to protect users against stalkerware.
The tool has been developed to run on a Raspberry Pi. Using a regular Wi-Fi connection, TinyCheck quickly analyzes a mobile device’s outgoing traffic and identifies Indicators of Compromise (IOCs) such as interactions with known malicious sources, like stalkerware-related servers.
At the moment, the tool uses IOCs collected not only by Kaspersky researchers, but also (and mostly) from repositories maintained by a security researcher Etienne Maynier (also known as Tek) from a Echap, and by Cian Heasley. We hope that the community will follow that work by keeping IOCs up-to-date.
Having said that, one should understand the limitations of TinyCheck, and use the tool with the following warning in mind: IOCs do not provide a complete detection of all stalkerware apps.
Therefore a result detecting no stalkerware cannot exclude the possibility that stalkerware is installed but not detected by TinyCheck at this stage.
3. Using IT Sec solutions like (free app) Kaspersky for Android
High level of certainty, installation required
While security solutions can also check and alert you about stalkerware, they need to be installed on the device. Therefore, there is a risk that the perpetrator will also be alerted.
At the same time, the detection effectiveness of the IT Sec solution is at the top of the list. This is due to the synergy of various protection techniques used. Because stalkerware is always updating and upgrading, it is becoming more sophisticated at overcoming existing protection. It is therefore crucial to apply multiple protection layers of a varied nature.
Therefore, if there is no risk of escalation, we would recommend using IT Security solutions when you need the highest rates of stalkerware detection.