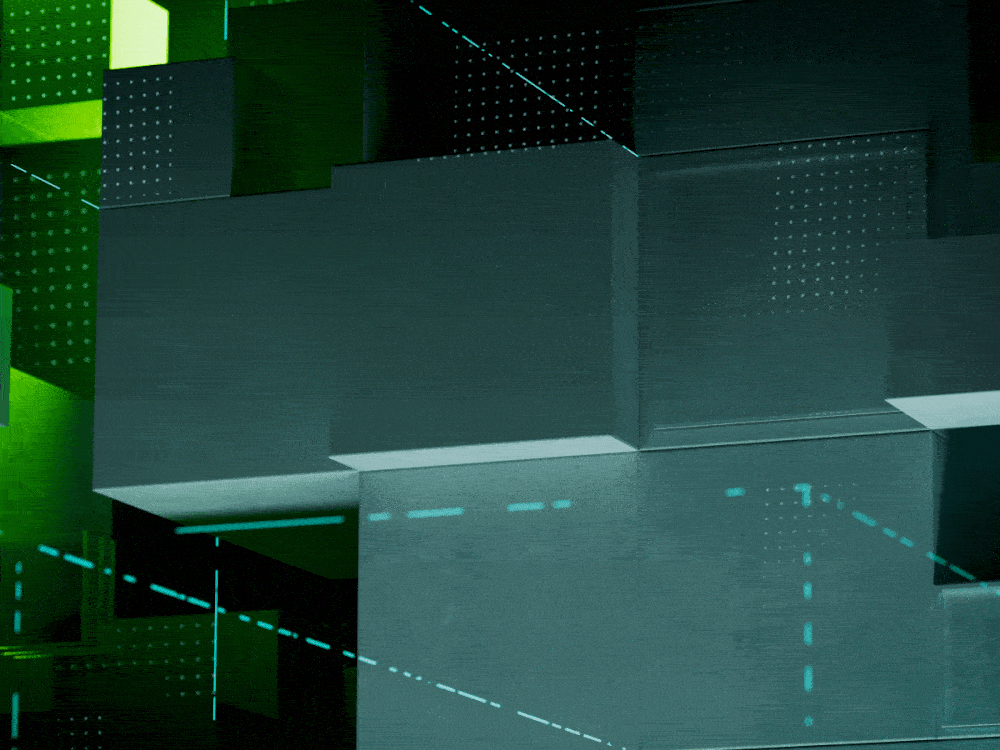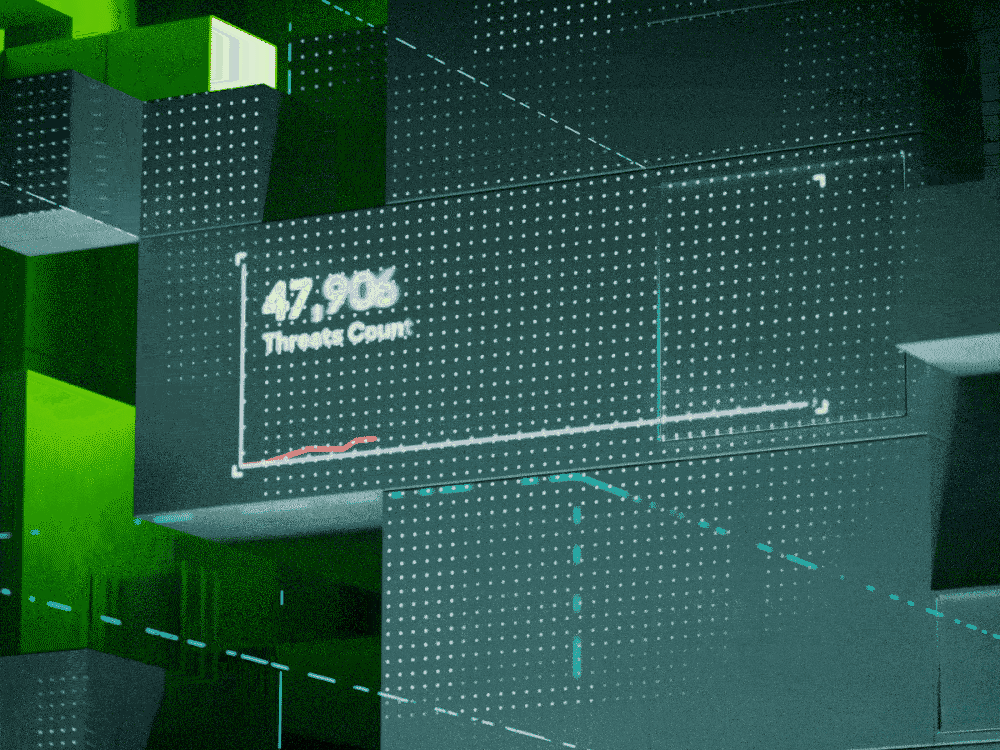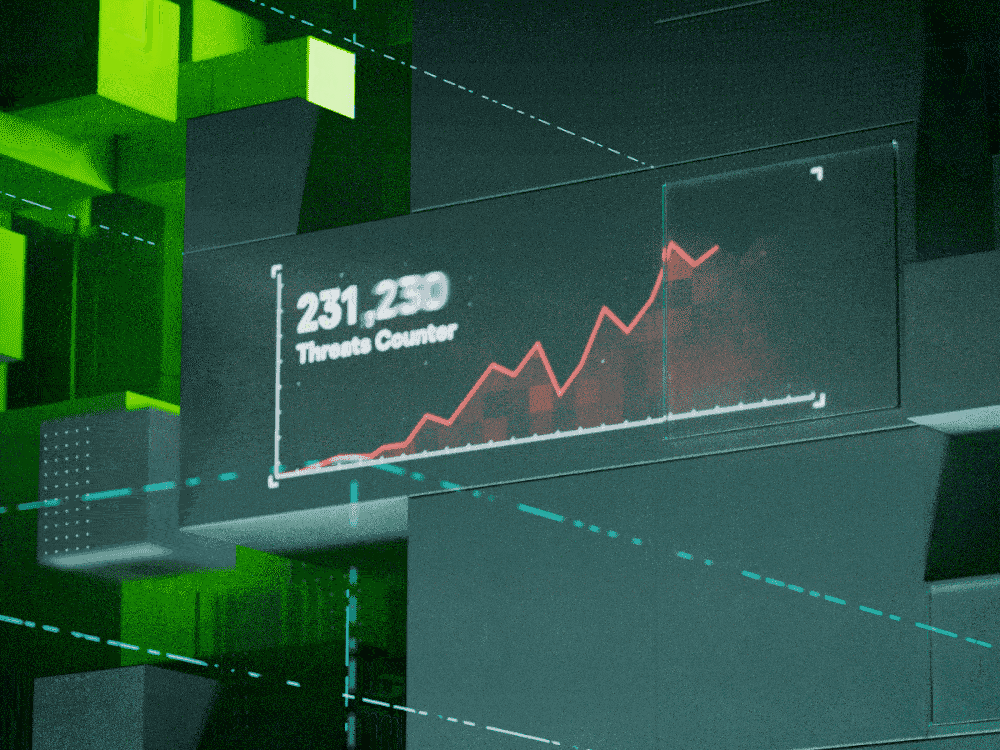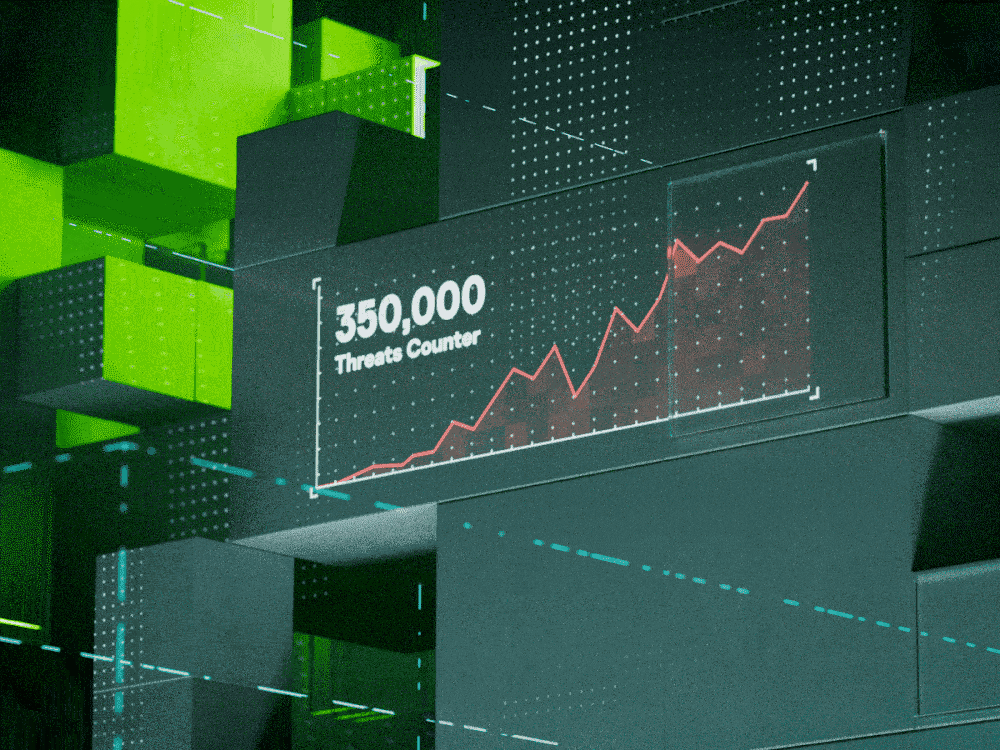
Cyberthreats and cybercriminals’ methods change all the time. Each year, we see things we’ve never seen before. Understanding what cyber researchers are finding can help your enterprise stay ahead of evolving cyberthreats, preventing costly data breaches and malicious damage.
Kaspersky has the biggest global network of cybersecurity research and analyst teams, collaborating closely with product research and development. With expert researchers distributed across the globe, we see can escalate and respond to local situations fast.
Here, we share some of our recent observations your business can act on today.
Our solution
Kaspersky Enterprise Cybersecurity
One cybersecurity partner for all your enterprise security needs.
1. Ransomware is stepping it up a notch

Fabio Assolini
Fabio Assolini, Senior Security Researcher, Global Research and Analysis Team (GReAT,) Latin America, says:
“This year, ransomware is no less active. Cybercriminals keep threatening retailers and enterprises worldwide. Watching these tendencies gives us threat intelligence to fight cybercrime today and helps us prepare for what we may see in the months to come.
“Our research groups ransomware into three big trends: Ransomware that adapts to be able to infect different platforms, ransomware becoming more “industrialized” and cybercriminals taking sides in geopolitical conflicts. But despite its ever-increasing sophistication and targeting, there’s still much enterprises can do to stay safe.”
What to do: Find out about the five best steps your business can take to fight ransomware – from keeping software up to date, to ensuring your Security Operations team has access to the latest threat intelligence.
2. Advanced Persistent Threats are coming out of the woodwork
An Advanced Persistent Threat (APT) involves sneaky, sophisticated hacking techniques. It may hide malicious software in your system for a long time, stealing information or waiting for the moment to cause maximum damage. Kaspersky tracks more than 900 groups of APTs.

David Emm
David Emm, Principal Security Researcher, GReAT Global, says:
“We became aware of a firmware-level APT compromise through our firmware scanner logs. The attackers had modified a single component to intercept the machine’s boot sequence and introduce a sophisticated infection chain. The chain leaves no traces on the hard drive, as its components operate in memory only – a fileless attack with a small footprint.”
The researchers named the new ATP MoonBounce and have linked it to a known threat actor.
What to do: Arm employees with the knowledge they need to protect your organization. Get APT threat reports on SecureList.
3. Apps can make Internet of Things devices even more vulnerable
The Internet of Things (IoT) is a fast-growing ecosystem – forecasts predict we’ll use more than 75 billion IoT devices by 2025. Among these, companion apps for internet-connected cars have attracted special attention. In early 2022, a 19-year-old hacker shared how he had accessed and controlled more than a dozen Tesla cars through their apps.
The vulnerability of IoT devices, increasingly part of manufacturing and industry processes, has long been known. Our interest in transparency recently spurred Kaspersky analysts to look at car-controlling apps, finding their security and openness often lacking.

Dan Demeter
What to do: Dan Demeter, Senior Security Researcher, GReAT Europe, Middle East and Africa says:
“For an ongoing well-established security perimeter, we recommend periodic checks and updates for all applications used withing the perimeter, whether it’s a consumer or a business environment. Remove any obsolete or not used apps from these environments as soon as possible.”
Demeter also highlights better practice among some vehicle companion apps. “Some use specially designed solutions from automakers, which, for example, make it impossible to unlock the doors remotely. With access to the vehicle’s data through the manufacturer’s website, there’s no need to give credentials to an app, and users can revoke access any time.”
4. Geopolitical tensions are raising denial-of-service risk
Distributed Denial of Service (DDoS) attacks are cybercriminals’ go-to targeted attack. They overwhelm a server, service or network with a flood of traffic, so you can’t give your customers reliable online service.
The Russia-Ukraine conflict has triggered a spate of DDoS attacks in both countries, targeting critical infrastructure, media and state-run services. Hacktivist groups have instigated some of these attacks, distributing apps, software and even games which can teach cybercrime skills to those with other aims, like extortion. Kaspersky researchers have noted a sharp rise in DDoS attacks across the board.
What to do: Researchers advise businesses and nation states to prepare for DDoS attacks before they happen, through investing in suitable security controls and preparing defensive strategies with national internet service providers (ISPs.)

Maher Yamout
Maher Yamout, Senior Security Researcher, GReAT Middle East, Turkey and Africa, says:
“Deploy cyber defenses in advance. When an attack comes, it’s too late. You never know when an emergency will happen, so today’s the day to take care of your anti-DDoS protection.”
Threat intelligence also plays an important role in preventing DDoS attacks. Kaspersky is the only global threat intelligence provider with a major presence and expertise in Russia, where most advanced persistent threats and attacks originate. Security teams should subscribe to Kaspersky SecureList to stay up-to-date.
5. Malware keeps upping the ante
Malware is common and costly. Over the past year, Kaspersky software prevented at least one malware attack on 20 percent of our users. Recently we’ve seen plenty of new and rehashed techniques aimed at disguising malware or letting it do more damage.

Dr Amin Hasbini
Dr Amin Hasbini, Unit Head of GReAT Middle East, Turkey and Africa, says:
“Since its discovery in 2014, we’ve seen the malware Emotet – originally designed to steal banking credentials – in many other forms, like as a delivery system for other malware and and botnet executable, using small employee mistakes to create big incidents. It mostly spreads nowadays through malicious email spam.”
What to do: Malware attacks often start with an employee making a small error of judgment, like clicking a link in a dodgy email, so one of the best ways to stay safe is to thoroughly educate all your staff in cybersecurity. Kaspersky research in partnership with Longitude, a Financial Times company, found leaders whose cybersecurity training programs can keep pace with the threat landscape say their companies are better prepared for a cyberattack.
Immersive cybersecurity training is a powerful way to engage your workforce with learning in an age when there is much competition for their attention.
Advanced cyberthreats are common. They have a big impact on business reputation and bottom line. When business leaders take cybersecurity action, they avoid spending more time later mopping up a cyberattack’s damage.
When choosing your cybersecurity vendor, look for those that participate in third-party tests and reviews, win awards and achieve top scores in independent tests. What’s clear is that advanced threats are ever-changing, so having the most up-to-date threat intelligence will always be crucial for your business.




