
Kaspersky Cyber Security Summit: How to adapt to inevitable?
Mid-April in Singapore was pretty hot not only because of tropical climate, but also because of INTERPOL World – a huge conference/exhibition organized by INTERPOL to give security product vendors
 INTERPOL World
INTERPOL World
 APT
APT





 Education
Education
 mobile devices
mobile devices

 cyberattacks
cyberattacks

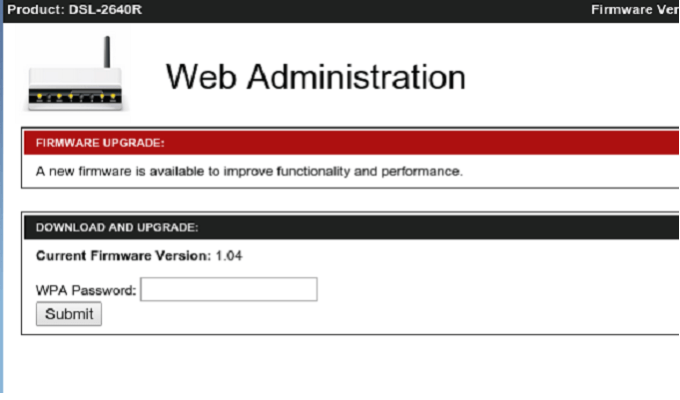




 awards
awards

 business security
business security