2013 will be remembered by both security professionals and everyday people for the number of events that took place in information security. Various incidences, from Edward Snowden’s revelations to the emergence of smartphone botnets and the Cryptolocker ransomware, have impacted the daily routines of people and organizations. Kaspersky Lab experts traditionally present the Key 2013 Threat List in a report published on SecureList. Here are the key findings from it: we present ten key security phenomena of 2013, which will further influence our lives throughout 2014.
1. The Internet under surveillance
The revealing publications in The Guardian and The New York Times, based on classified documents provided by Edward Snowden, have greatly impacted the Internet (and will continue doing so in the future). A former NSA contactor supplied the newspapers with a large volume of information revealing the United States Secret Service’s surveillance practices on the Internet. Such actions were not for monitoring individuals as targeted acts of surveillance, but were done for global information harvesting and collecting data on, basically, everyone. Moreover, while the bigger part of the documents describes American activities (for obvious reasons), the evidence showed that similar activities were carried out by other countries’ Secret Services. Aware of the news, major cloud service providers hastily initiated cryptographic protection of their cloud data, including intranet data links. Government organizations, in turn, implemented additional protective measures. According to Aleks Gostev, the chief security expert at Kaspersky Lab, the events might lead to the fragmentation of the Internet, and later to its division into nation-specific segments protected by “great firewalls” like the one in China. Meanwhile those who prefer confidentiality, including enterprises and individuals operating illegal businesses, are actively seeking refuge in the “darknet” – a highly anonymized sub-network using Tor and I2P protocols.
2. On-demand targeted attacks
While the majority of infamous targeted attacks of the past were likely performed by government agencies and bureaus, hired hackers executed some attacks in 2013. Among those is the IceFog targeted attack, detected by Kaspersky Lab. It mostly targets Mac users. An industrial intelligence act performed through data theft from corporate PCs might help some companies gain a considerable competitive advantage; needless to say, it is easy to pass it off as a government-sponsored global surveillance initiative acting in the nation’s best interests. “To get it rolling, the corporate entities have to hire cyber-contractors, which can be defined as organized groups of proficient hackers providing commercial intelligence services to companies. Those are likely to be self-named as cyber-detectives,” Gostev says.
Targeted attacks have visible influence on the present business environment. The survey, recently conducted by B2B International and commissioned by Kaspersky Lab, showed that 9% of companies have been victims of targeted attacks.
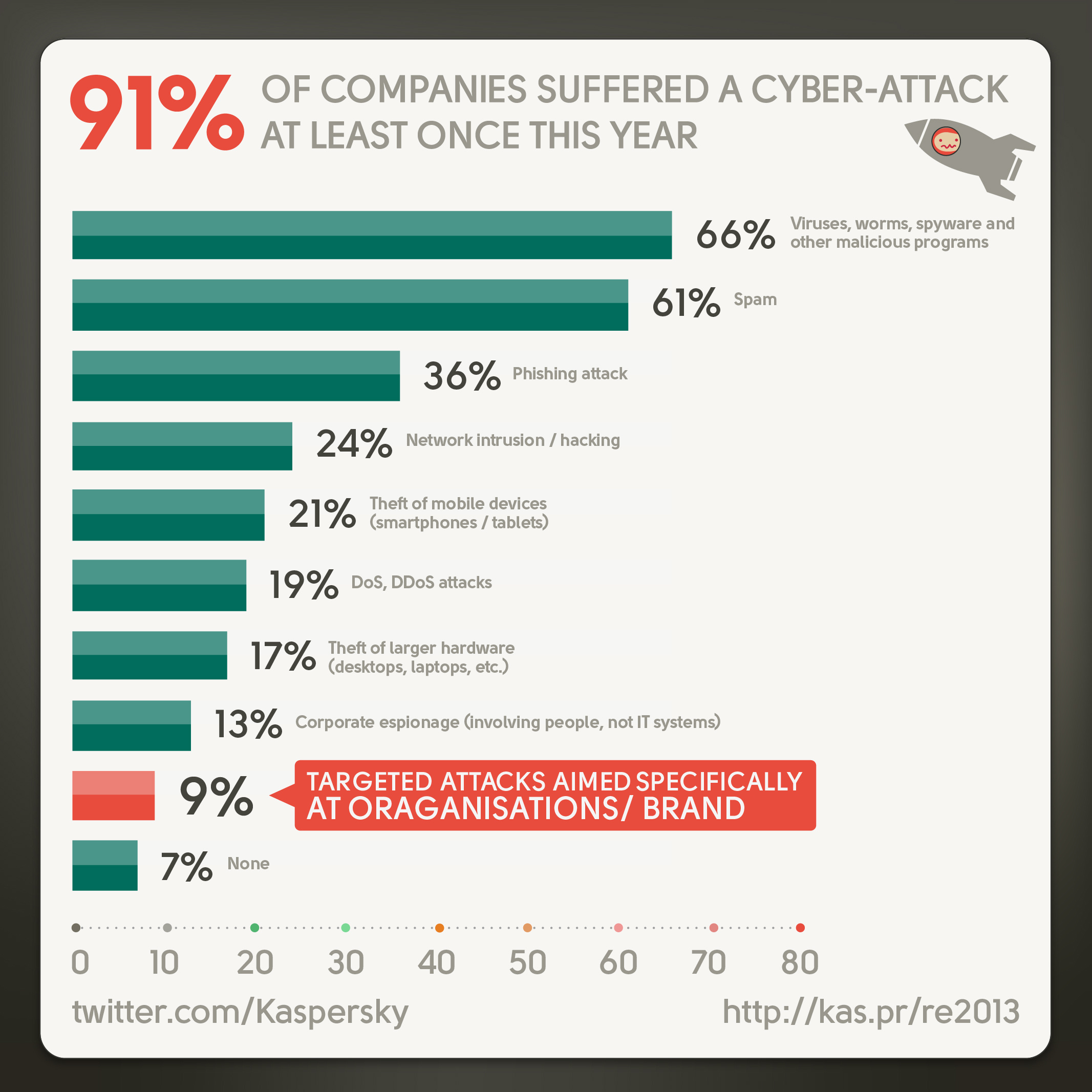
Quite importantly, information theft is not the only scenario for the attack. The competition could use such tricks as DoS and DDoS attacks, data wipe-out or deliberate damage to PCs, as well as actual money theft and reputational damage. These findings by Vitaly Kamlyuk and Sergey Lozhkin are cited in their report on corporate threats.
3. Mobile botnets
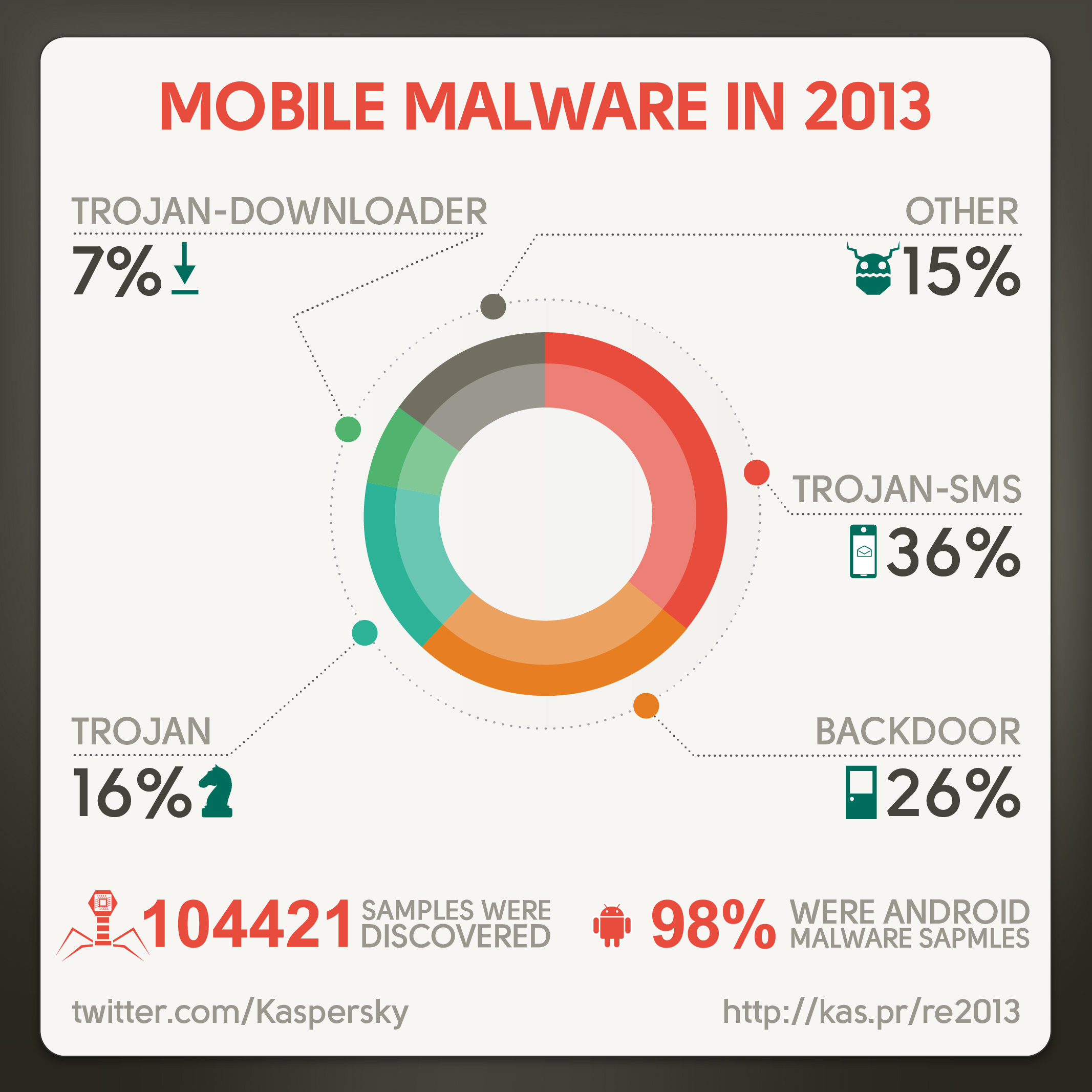
Fast-paced evolution of mobile threats is a visible trend: culprits are actively exploring the new market, which offers a huge pool of potential victims and simple mechanics of getting financial benefits. This year, our database of malware applications grew some 104421 entries, whereas the total number of such applications in the previous year was around 44000. The majority of such threats are designed for Android – they occupy over 98% of the total mobile malware domain.
Among others, mobile botnets, remotely managed networks of affected smartphones, have been getting more and more widespread. About 60% of the detected programs include fragments of a botnet construction. The most notorious botnets include MTK and Opfake. The botnets are used for a variety of purposes: from spam to distribution of other malware. New for 2013, such botnets are available for lease.
4. Growing complexity of mobile threats
Besides growing in quantity, mobile threats are becoming more complex: hackers port common threats for Windows onto mobile platforms. As of today, the most complex Android Trojan is Obad, which exploits three vulnerabilities preventing fast-track deletion and analysis using backdoor, botnet and SMS Trojan capabilities. In the upcoming year, we will face even more complex Android malware and the emergence of new ‘business models’ such as blockers.
5. Cyber-blackmailing
Hackers receive collateral financial benefits from each attack or intrusion; however, they do not have many good means of getting the money from a PC user directly. One way would be money theft from a credit card or Internet bank; the other is ransomware. The latter became more widespread in 2013 along with the emergence of Cryptolocker. The key differentiator of Cryptolocker from many kinds of SMS blockers is the fact that it actually encrypts your computer by means of asymmetric cryptography with a strong key, unique for every computer. The user is able to de-cypher the files only on receiving the key from the delinquents, who ask up to $3000 for it. Notably, one of the main means to pay the ransom is BitCoin.
6. Crypto-currencies
The BitCoin concept was introduced back in 2009, but by 2013 the crypto-currency has gained momentum and grown significantly in terms of “exchange rate.” Whereas a BitCoin was worth $13 in early 2013, by April it grew to $260, and, after a profound bust, its rate skyrocketed to reach a $1000 milestone. BitCoin is valued as a highly decentralized payment system and the anonymity of participants. No wonder it is extremely popular among cyber-criminals and is involved in many notorious incidents, from security breaches in BitCoin payment services to actual acts of theft from users.

7. Attacks targeting online banking services
The key threats applied to users’ bank account in recent years were mostly targeted at snatching SMS confirmations; in other words, mobile Trojans and PC Trojans were acting together. In 2013, the malware mobile applications capable of attacking banking services without involving ‘big brother’ became more widespread. Their schemes are numerous: credit card credentials theft, unauthorized money transfers from credit cards tied to mobile devices, and many others. The Trojans are also capable of checking the balance of the affected account to achieve higher cost-efficiency.
8. A stunning number of security incidents
If you think you did not encounter a single cyber-attack in 2013, you, most likely, have not noticed it because of antivirus protection. The stats confirm that the chances of avoiding this misfortune are low, with over 5 billion cyber-attacks registered throughout the year. 315,000 were the daily average for Kaspersky Lab in 2013 of new malware samples.
9. The dangerous Web
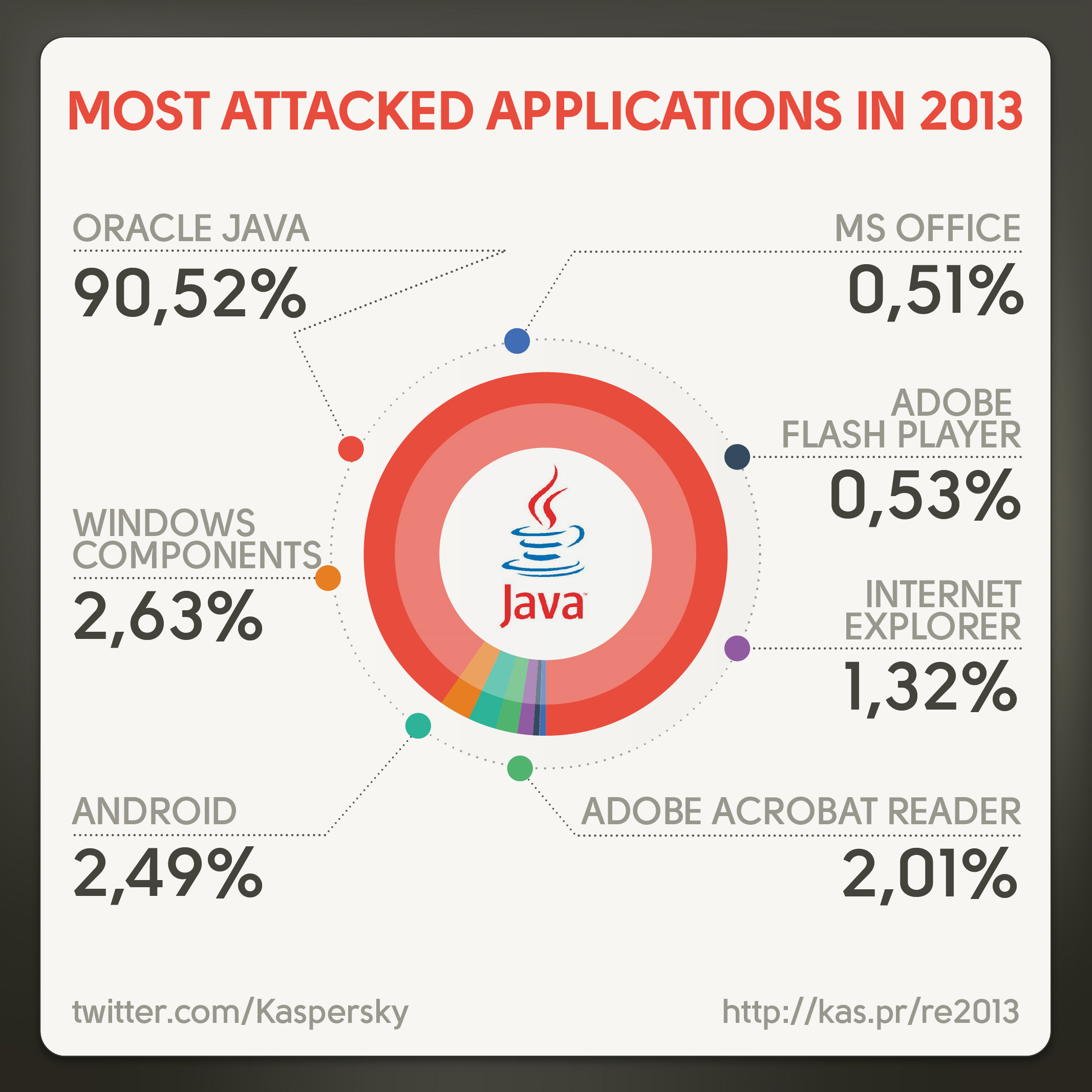
USA and Russia are the undisputed leaders among countries who host malware servers: 25.5% and 19.4%, respectively. Germany and the Netherlands account for 12% each, with other countries following with 3.5% and lower. Vietnam is now ranked among the world’s top 10, whereas China moved from 8th to 21st position in the ranking as a result of more stringent domain registration and hosting criteria imposed by the Chinese government, according to Christian Funk and Maria Garnaeva of Kaspersky Lab. Citizens of Russia, Austria and Germany, as well as some CIS and Asian countries are exposed to an increased risk of being affected by attacks. Czech Republic, Slovakia and Singapore enjoy the lowest risk rate. The methods most widely used by the attackers include social engineering techniques and exploits to Java vulnerabilities. Java accounts for over 90% of all actively exploited vulnerabilities.
10. The weakest link?
The ever-changing cyber security world has one constant, people. They are prone to get hoodwinked by social engineering tricks (in the case of targeted attacks, this approach is most likely to succeed), use untrustworthy application stores on their mobile devices, not pay attention to the address bar and input their credit card credentials on a phishing website, and, of course, use passwords like ‘12345’ to access their online accounts. Only long-term educational initiatives designed for users are able to make this connected world a safer place.
 analysis
analysis

 Tips
Tips