What’s the No. 1 most unpleasant pain in the xxx thorn in the side of the modern-day cyber-world in terms of damage, evil sophistication, and headline-grabbing the world over? Can you guess?…
Ah, the title of this post may have given it away, but yes, of course, it’s ransomware (aka cryptomalware, but I’ll stick with the simpler, less tongue-twisting, and professional term ‘ransomware’).
So: ransomware. Bad. How bad?…
Well, it’s actually so bad, and has been so consistently bad for years, so deeply embedded in all things digital, and has so overwhelmed so many large organizations (even indirectly being followed by human deaths), which (large organizations) have forked out so much money to pay ransoms for, that the world’s news media has become almost indifferent to it. It’s stopped being headline news, having been transformed into an every-day casual event. And that’s what’s most worrying of all: it means the cyber-scumbags (apologies for such a strong language, but it’s really the best way to describe these folks) are winning; cyber-extortion is becoming a seemingly inevitable reality of today’s digital world and it seems there’s nothing can be done about it.
And they’re winning for three reasons:
Third (I’ll start at the end): the ‘big boys’ are still playing their schoolyard geopolitical games, which blocks national cyber-polices exchanging operational information for coordinated searching, catching, arresting and charging of ransomware operators.
Second: users aren’t prepared – resilient – enough to respond to such attacks.
And first (most important): not all washing powders are the same anti-ransomware technologies are equally effective – by a long way.
Often, ‘on the tin’, anti-ransomware technologies featured in cybersecurity solutions are claimed to be effective. But in practice they don’t quite do exactly what it says on the tin, or – if they do, consistently. And what does this mean? That users are scandalously unprotected against very professional, technically sophisticated ransomware attacks.
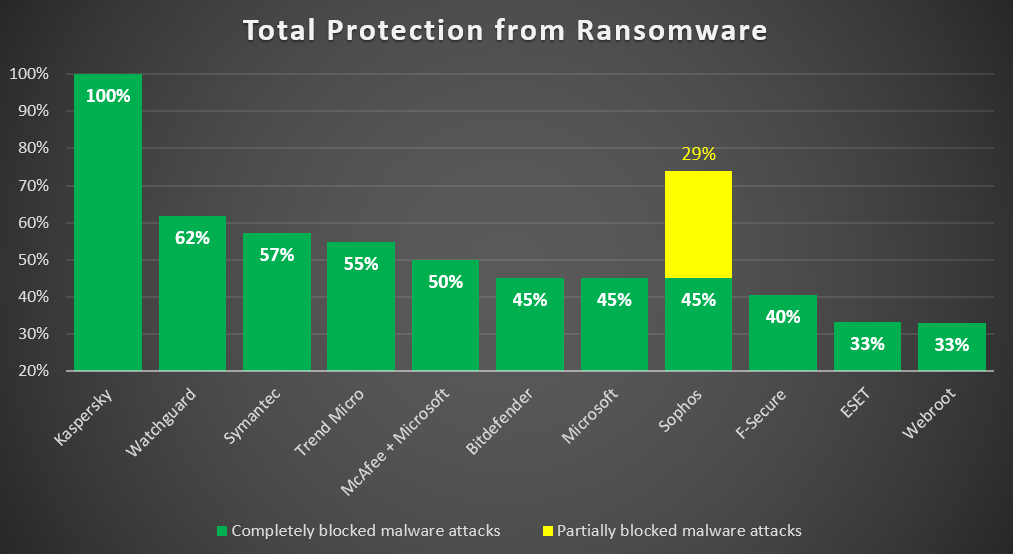
But don’t just take my word for it. Check what the trusted German testing institute – AV-TEST – say. They’ve just published complex research on the ability of cybersecurity products to tackle ransomware. They paid no attention whatsover to marketing claims (à la ‘this deodorant is guaranteed to last for 48 hours’), and didn’t just use widely-know in-the-wild ransomware samples. They besieged several of the top cybersecurity solutions in real ‘battlefield’ conditions, firing at them all sorts of live-ammunition ransomware artillery that’s actually out there today. As mentioned, no in-the-wild samples, but those technically capable of weaponizing a ransomware attack. And what did they find? On the whole – something thoroughly shocking and scary:
Now, simply checking fresh samples of, say, 20 regular ransomware families known to every security vendor (in other words, samples already in the cybersecurity vendors’ databases) – almost all cyber-protection copes well with this.
However, the research objective was to see what happens when things are made tougher – to test as close to real life conditions as possible. How do the products react to new attack methods of ransomware malware? What happens if it covertly penetrates a corporate network and starts causing havoc? How well do the products prevent network attacks where user files in shared folders are encrypted remotely – including network attacks that use ransomware samples that were successfully detected and blocked in the basic initial scenario?
Just three (3!) tested products out of 11 managed to deal with such kinds of new, tricky ransomware attacks. And among them, only our Kaspersky Endpoint Security Cloud protected user data with a 100% result. Note that attacks aimed at stealing user data are still among the most widespread – posing a serious threat to organizations whose project documentation, customer information, backups and other data are stored in networked locations.
But that’s not all! Are you sitting down?…
Most of the tested security solutions not only failed to detect attacks and protect user files, but also managed to delete the text messages from the cyber-extortionists containing the ransom demands! But those messages can contain the technical information for recovering the encrypted files! This information is what is used by cybersecurity experts in their attempts to help the victim: to identify the malware, find a vulnerability in the encryption algorithm, and either develop a decryptor for retrieving valuable data or suggest resorting to an existing decryptor from independent open sources (for example, No More Ransom).
Not fallen off your chair yet? Good. Then we’ll add some more findings that may amaze you…
AV-TEST also checked how well the security solutions do examining ‘entrails’ of ransomware still poorly used in-the-wild ransomware or even APTs, but which pose a threat to society as they may start being used soon. For example: abuse of legitimate Windows services, encryption via hard and symbolic links, delayed packet encryption, or encryption via memory-mapped files. Fourteen different techniques in total. And what do you think was found in the testing? Again, it was only our Kaspersky Endpoint Security Cloud that demonstrated a 100% result: every single user file was protected and all the threats were eliminated from the targeted system!
Oh, and one last thing: only two products were able to roll back changes made to user data after a remote ransomware attack. Needless to say – our product was one of them.
In general, while up in the higher-echelons of world power they’re still squabbling over whose economic-geopolitical model is best, and which products to allow or ban due to their origin and ‘national interests’ – regardless of their actual quality and usefulness for real users – fortunately, users can continue to decide for themselves by choosing the best solution. ‘Best’ as in: the most effective, efficient, reliable and fast, and with a no-compromise approach to stopping attacks of any kind and no matter where from.
So there you have it. A short piece to show you that it’s not only the devil that can hide in the details, but also… a heavenly savior – in this case anti-ransomware tech that… actually works).
You can find more details on the results of the testing in this post.
May the Ransomware Protection Force be with you!
 Ransomware
Ransomware

 Tips
Tips