How can information be transferred from a computer that’s connected neither to the internet nor a local network? For many years now, Israeli researcher Mordechai Guri has been on a mission to uncover the exotic methods with which attackers could do precisely that to steal data. And we’ve always been there to cover his research. Recently, Guri published two new scientific papers within four days of each other. In the first, he demonstrates how to turn a computer into a radio transmitter by manipulating data loading into RAM; in the second — how to use an ordinary computer monitor as an “acoustic spy”.
Hypothetical situation
Guri’s papers all tackle the same scenario:
- A computer stores or processes highly classified data.
- To ensure the security of this data, the system is isolated from the network, and even located in a separate room with restricted access.
- The hypothetical attacker knows how to install data-snatching malware on the computer, and now needs to exfiltrate this data.
The task of infecting an isolated computer is tricky — but by no means impossible. One way is to take advantage of a careless operator who inadvertently plugs an infected flash drive into the “secret” computer (a depressingly realistic scenario). Another, theoretically possible, way is to plant malware in the system in advance: at the factory or during delivery to the customer. The simplest way is to bribe a company employee. However, to exfiltrate the data, the cybervillains need deploy side-channel attacks.
RAMBO
In the first paper, Guri describes a way to turn ordinary memory modules into a radio transmitter — a so-called RAMBO attack. It’s no secret that all electronic systems make “noise” in one way or another during operation; that is, they emit spurious signals. Random access memory (RAM) is no exception: changing the voltage supplied to RAM modules to update data generates radio waves. In the case of a RAMBO attack, it’s malware that initiates a data write to RAM. What matters is not the kind of data but the intensity of the operation. By accessing the modules in bursts alternated with pauses, and catching radio emissions at a certain frequency, it’s possible to create a channel for covert data transmission.
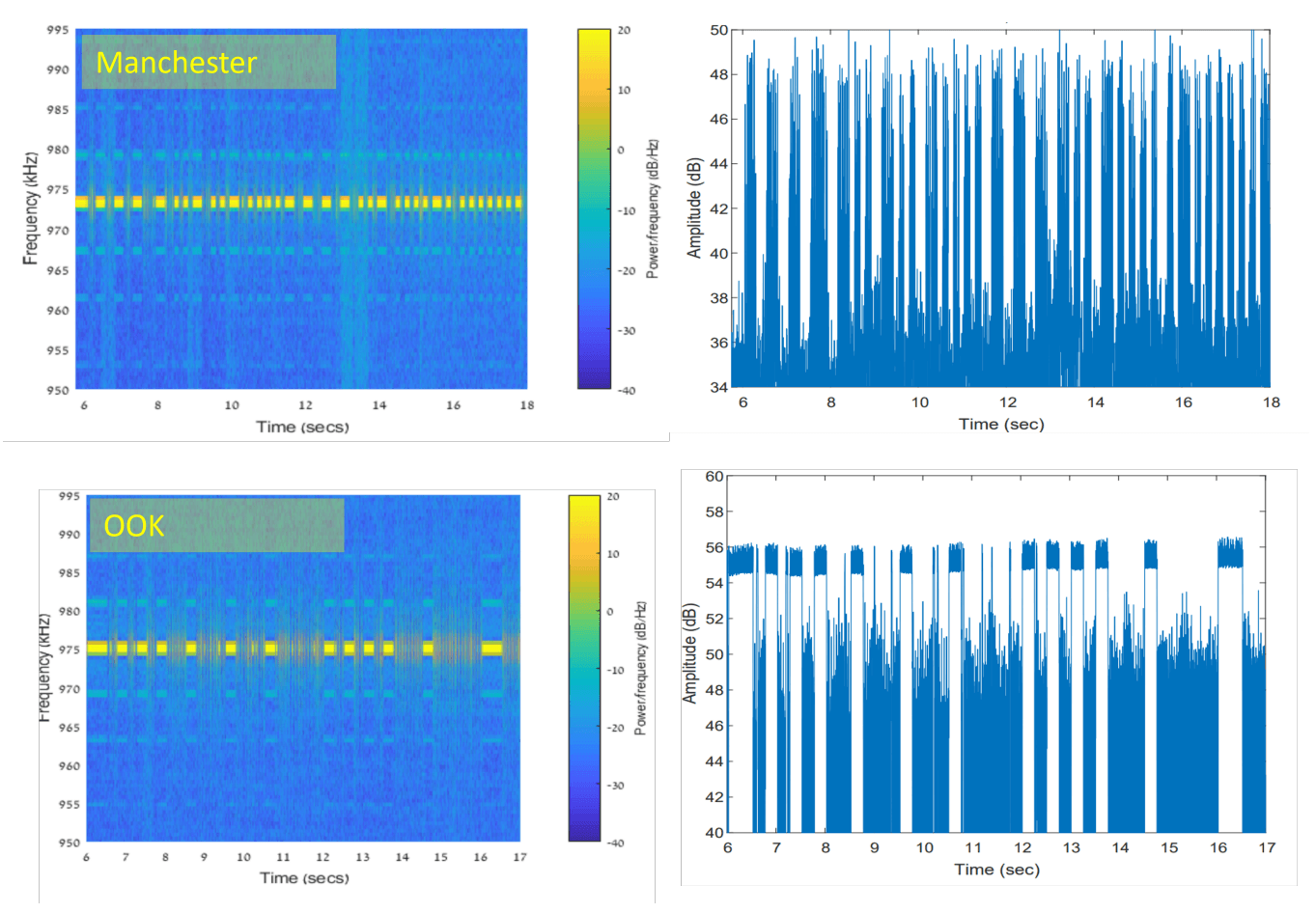
Spectrogram of radio emission from RAM. Source
The image above shows what it looks like. Accessing memory generates radiation at a frequency of about 975 kilohertz. The moments when data is written to memory and the “silent” periods are clearly distinguishable. The result is something like Morse code — only slightly more complicated: the data here is encoded using two different methods. The bottom graph uses a simple amplitude modulation, and the top one uses a slightly more complex Manchester code. The latter has some advantages when it comes to decrypting the data later on.
The key question in any such study is always the same: how effective is the method? Guri managed to achieve reliable data transmission at speeds of up to 1000 bits per second (bps). By the standards of modern data communication, that’s snail-like; however, it’s perfectly sufficient to, say, transmit keystrokes to the attacker in real time. More importantly, this exfiltration method works at a distance of up to seven meters.
We’ve already covered a similar method designed by the same researcher, which also relies on spurious radiation from RAM modules. But in that case, Guri used a different data-transfer frequency — 2.4 gigahertz (GHz) — and the speed was 10 times slower: no more than 100bps. The new method is more effective, although the previous one has a key advantage: wireless data networks operate at 2.4 GHz, and many household devices also use this frequency band. This potentially allows attackers to hide their spying activities in radio noise.
PIXHELL
Guri’s second paper proposes a wholly different method of data exfiltration — though it’s based on the same core principles. Besides spurious radio emissions, electronic components can also emit sound. The PIXHELL attack method relies on barely audible noise produced by the electronic components found in a typical computer monitor. This acoustic noise is caused by a change in the voltage supplied to, say, capacitors in an electrical circuit.
One strategy for manipulating this noise is to output a sequence of black-and-white rows to the screen; something like this:

Bitmap patterns output to the monitor for covert data transmission. Source
Each of the on-screen patterns causes the monitor’s electronic components to sound at a certain frequency. What Guri did in essence was to turn the display into a very quiet, very low-quality loudspeaker. The downside of this method is that its results vary depending on the model of the display: each has its own particular electronic circuitry, and so the intensity of spurious acoustic noise varies:
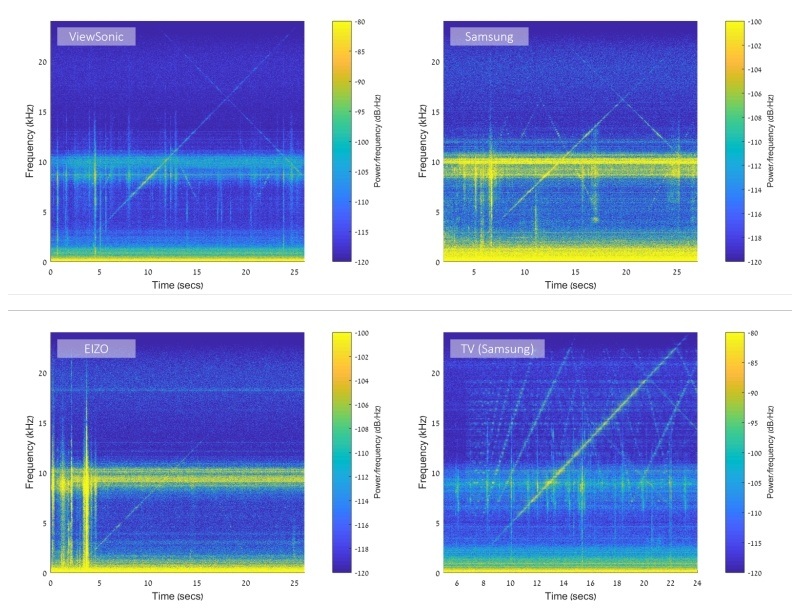
Amplitude of acoustic signals emitted by the monitor, against the background of other noise. Source
Looking at the spectrograms of the acoustic signals from four different monitors, we’re interested in the sloping lines, which represent noise with variable frequency. Everything else is other noise from the display, which is sure to drown out the “useful” data. We can conclude that the Samsung monitor and TV noise is louder than the other two devices. What remains is choosing the most suitable frequency and transmitting data on it using one of the available encoding methods.
What’s interesting about this method is that a regular smartphone can serve as a receiver. Unlike the previous study, there’s no need for an expensive (and possibly suspicious) radio receiver. But there’s also a downside: the scheme works reliably at a distance of no more than two meters from the display. Moreover, the phone should be held directly next to the monitor, or, at the very least, be lying nearby on the table. The speed of a theft would also be horribly slow — no more than 20bps.
Besides, the operator would surely be puzzled by their screen displaying black-and-white ripples. Guri’s paper thus considers a situation where data exfiltration occurs at night: the computer (and monitor) are working, but there’s no one in the room. However, covert transmission in the presence of humans (who may spot an anomaly) is acknowledged as doable — by reducing the brightness of the display or subtly superimposing the patterns onto another image.
Countering RAMBO and PIXHELL attacks
Guri proposes countermeasures for designers of maximum-security systems. In the case of RAMBO, spurious radio emissions should be isolated against interception — for which he suggests using a computer case capable of shielding all radio waves. For processing sensitive data, shielding the entire room is also an option.
The PIXHELL attack seems less reliable, but it’s also hard to defend against — except by filling the room with random noise. As ever, it’s vital to stop unwanted software from running. One major takeaway from Mordechai Guri’s numerous works is that finding malware on a machine is a lot easier than guarding against all possible methods of side-channel data exfiltration.
 side-channel attack
side-channel attack
