If your website uses the script from Polyfill.io, we recommend removing it ASAP: the service is sending malicious code to your visitors. This article explains what Polyfill.io is for, why it’s become dangerous to use, and what you should do about it if you do use it.
What polyfills and Polyfill.io are
A polyfill is a piece of code that implements features otherwise unsupported by certain browser versions. This is typically JavaScript code that adds support for HTML5, CSS3, JavaScript API and other standards and technologies that spare web developers the headache of supporting exotic or outdated browsers. Polyfills saw their heyday in the 2010s as HTML5 and CSS3 gradually took over the Web.
Polyfill.io is a service that helps automatically deliver polyfills that a browser requires for displaying a particular website.
The service gained popularity both for its efficiency (only the polyfills you need are loaded) and for its regular updates to the technologies and standards used. Straightforward implementation was a factor as well: all the developer needed to start using Polyfill.io was to add a short string to the website code in order to enable the service’s script.
Polyfill.io was originally created by the Financial Times web development team. In February 2024, the service, along with the associated domain and GitHub account, was sold to the Chinese CDN provider Funnull. It wasn’t six months before trouble began.
Malicious code from cdn.polyfill.io
On June 25, 2024, researchers at Sansec discovered that cdn.polyfill.io had begun to deliver malicious code to users of websites that used Polyfill.io. The code used a typosquatted domain pretending to be Google Analytics — [code] www.googie-anaiytics.com[/code] — to redirect users to a Vietnamese sports betting site.
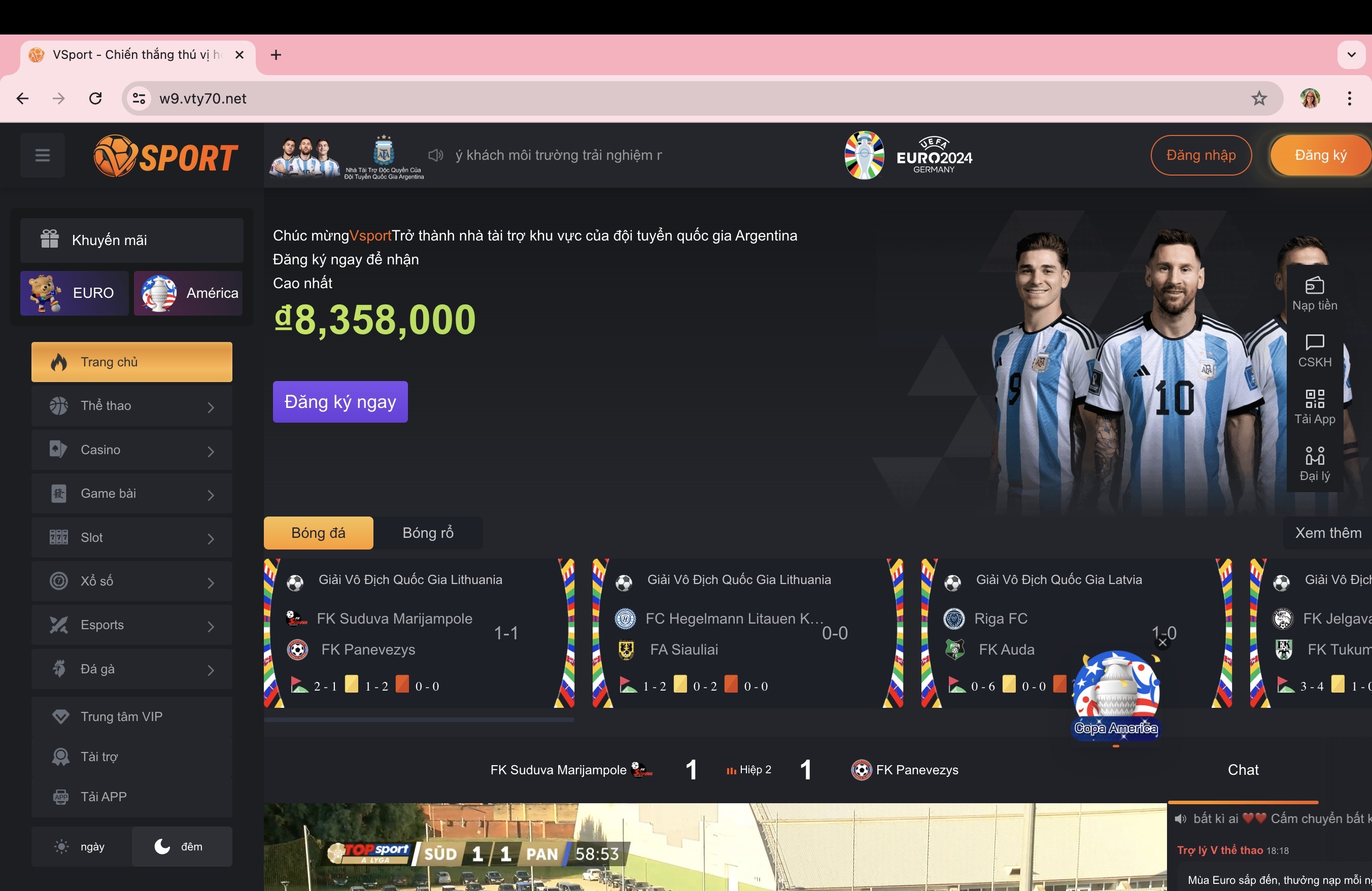
The malicious code redirected the users of compromised sites to a sports betting site written in Vietnamese
According to the researchers, this wasn’t the first time that Polyfill.io had been caught spreading malicious code. Those who had noticed the dangerous behavior earlier tried complaining (archived link) in GitHub comments, but the new owners of Polyfill.io quickly removed all the criticisms (here’s another example from the Internet Archive).
The potentially harmful script is allegedly present on more than 100,000 websites — some of them rather big ones.
Google Ads: one more reason to remove Polyfill.io
In case visitors getting a malicious script doesn’t sound too worrying, Google Ads is giving website operators a further valid reason to hurry up and get the problem fixed.
Google’s advertising service has suspended the display of ads linking to websites that spread malicious scripts from several services. Besides Polyfill.io, the list includes Bootcss.com, Bootcdn.net and Staticfile.org.
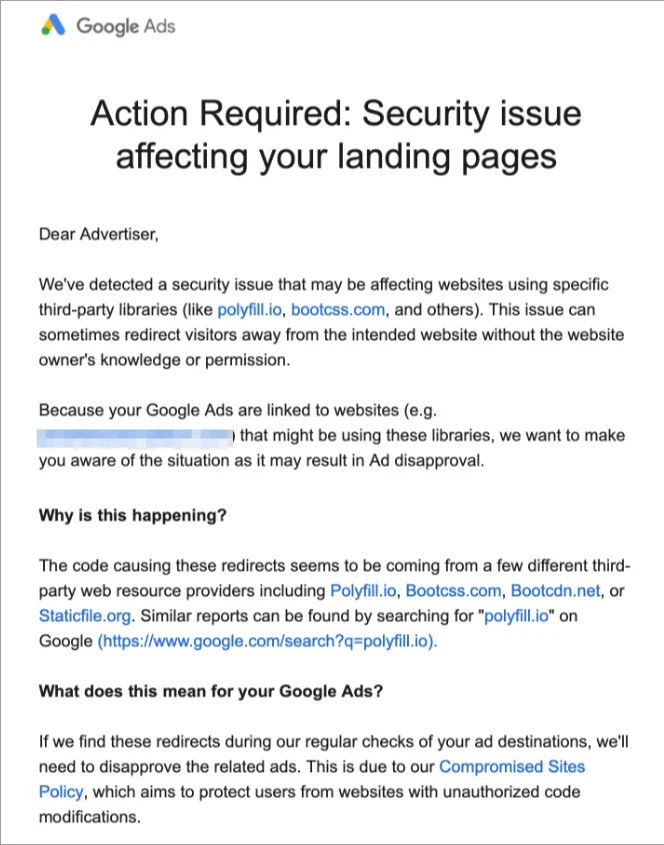
A Google Ads suspension warning due to the website using a malicious script downloaded from Polyfill.io, Bootcss.com, Bootcdn.net or Staticfile.org. Source
You’d be wise to stop using the aforementioned services on your website, or else you risk losing traffic due to users being led away by the malicious scripts and because of Google Ads no longer promoting you.
Protecting against the Polyfill.io attack
Here are a few steps to take about the attack:
- Remove the Polyfill.io script from your website as soon as you can — along with ones from Bootcss.com, Bootcdn.net and Staticfile.org.
- Consider dropping polyfills altogether. The Polyfill.io developer, which recommends doing just that, says that polyfills are no longer relevant.
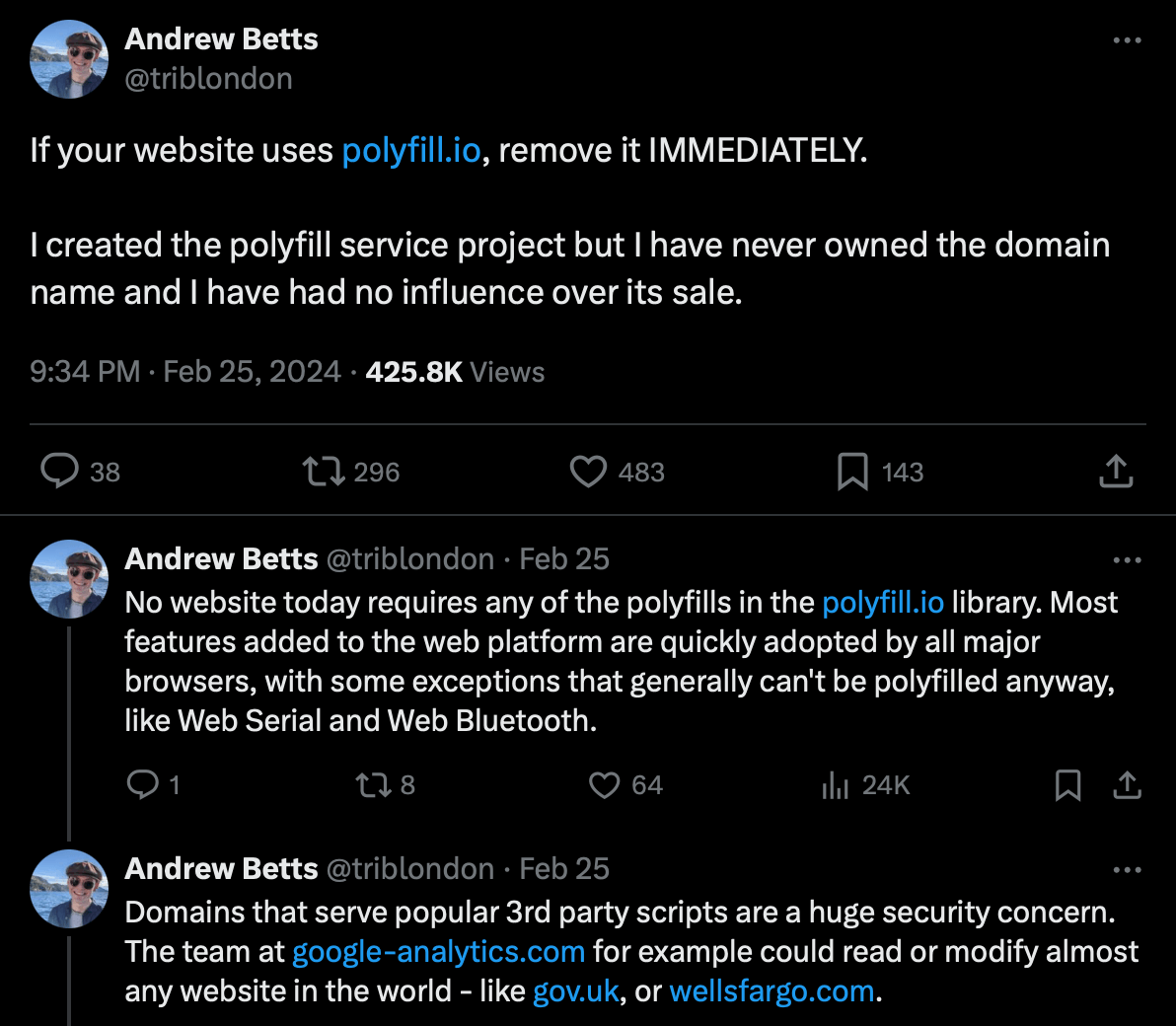
The Polyfill.io developer recommends removing Polyfill.io and dropping polyfills altogether as these are no longer relevant. Source
- If you can’t follow that advice for some reason, use the alternatives by Cloudflare or Fastly.
- All in all, try cutting down on the number of external scripts your website uses. Each of those is a potential vulnerability.
 supply-chain attack
supply-chain attack
