
All apps on Google Play are safe: Fact or fiction?
There’s no malware in the official Android store, right? We get to the bottom of this claim.
423 articles

There’s no malware in the official Android store, right? We get to the bottom of this claim.

Eugene Kaspersky explains how Kaspersky Sandbox uses virtual machines to thoroughly examine malware’s behavior.

Jeff and Dave discuss more cameras in Kings Cross, Twitter accidentally using personal data for ads without permission, Microsoft listening in on Skype, and more.

Jeff and Dave discuss Five Eyes looking to weaken encryption, possible social media changes, Amazon Rings used for surveillance, and more.

Jeff and Dave discuss the $5 billion fine for Facebook, Google Home listening ,and more.

Dave and Jeff discuss a Florida town that paid to restore data following a ransomware attack, Instagram improving account restoration, and more.

In this post we explain why digital clutter can cost you your job.

This episode brings you stories of Amazon Alexa, a UK government BCC error, and so-called smart-car apps with hard-coded passwords.

Does saying “hyphen” five times to your iPhone really crash it — or is that just another myth?

Things you should know about your home Internet connection: How to be sure it is safe and waste no time calling tech support.

Jeff and David take a look at a recalled smart watch in the EU, faulty webcam covers from the NSA, changes in iOS, and more.

Employees going away for the winter break? We explain what to do to keep trips from turning into corporate data leaks.

We love to spend money, but we worry about losing it and struggle to protect it. Read this report to learn how people think about the money they spend online.

Our study revealed that small businesses are at risk because of their reliance on staff who are inexperienced at cybersecurity.

Freelancers are beloved targets for cybercriminals, who use phishing and malware to steal credentials and money. Here’s how to avoid their traps and stay safe.

Android lets you configure app permissions to protect your data and restrict access to dangerous functions. We explain how to do it and why.

We explain what a guest Wi-Fi network is, how to set one up, and what video game consoles and other IoT devices have to do with it.

People worry about technologies stealing their jobs. Young people are less concerned; many of them are sure that completely new professions will emerge instead.
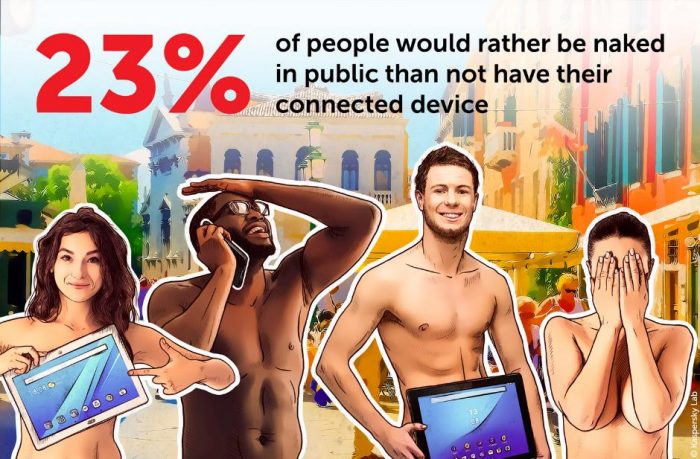
A lack of connectivity can now actually seem worse than many other unpleasant situations.