With access to corporate e-mail, cybercriminals can perform business e-mail compromise–type attacks. That’s why we see so many phishing letters directing corporate users to sign in to websites fashioned like the MS Office login page. And that means it’s very important to know what to pay attention to if a link redirects to a page like that.
Cybercriminals stealing credentials for Microsoft Office accounts is nothing new. However, the methods attackers use keep getting more advanced. Today, we’re using a real-world case — a letter we actually received — to demonstrate best practices and to outline some of the new tricks.
New phishing trick: HTML attachment
A phishing letter normally contains a hyperlink to a fake website. As we say regularly, hyperlinks need careful examination both for general appearance and for the actual Web addresses they lead to (hovering over the URL reveals the target address in most mail clients and Web interfaces). Sure enough, once enough people had absorbed that simple precaution, phishers began replacing links with attached HTML files, the sole purpose of which is to automate redirection.
Clicking on the HTML attachment opens it in a browser. As far as the phishing aspect, the file has just one line of code (javascript: window.location.href) with the phishing website address as a variable. It forces the browser to open the website in the same window.
What to look for in a phishing letter
New tactics aside, phishing is phishing, so begin with the letter itself. Here is the actual letter we received. In this case, it’s a fake incoming voice message notification:
Before clicking on the attachment, we have a few questions to contemplate:
- Do you know the sender? Is it likely the sender would leave you a voice message at work?
- Is it common practice at your company to send voice messages by e-mail? Not that it is used much nowadays, but Microsoft 365 hasn’t supported voice mail since January 2020.
- Do you have a clear idea what app sent the notification? MS Recorder is not part of the Office package — and anyway, Microsofts default sound recording app, which could in theory send voice messages, is called Voice Recorder, not MS Recorder.
- Does the attachment look like an audio file? Voice Recorder can share voice recordings, but it sends them as .m3a files. Even if the recording comes from a tool unknown to you and is itself stored on a server, there should be a link to it, not an attachment.
In summary: We have a letter from an unknown sender delivering an alleged voice message (a feature we never use) recorded using an unknown program, sent in as an attached Web page. Worth trying to open? Certainly not.
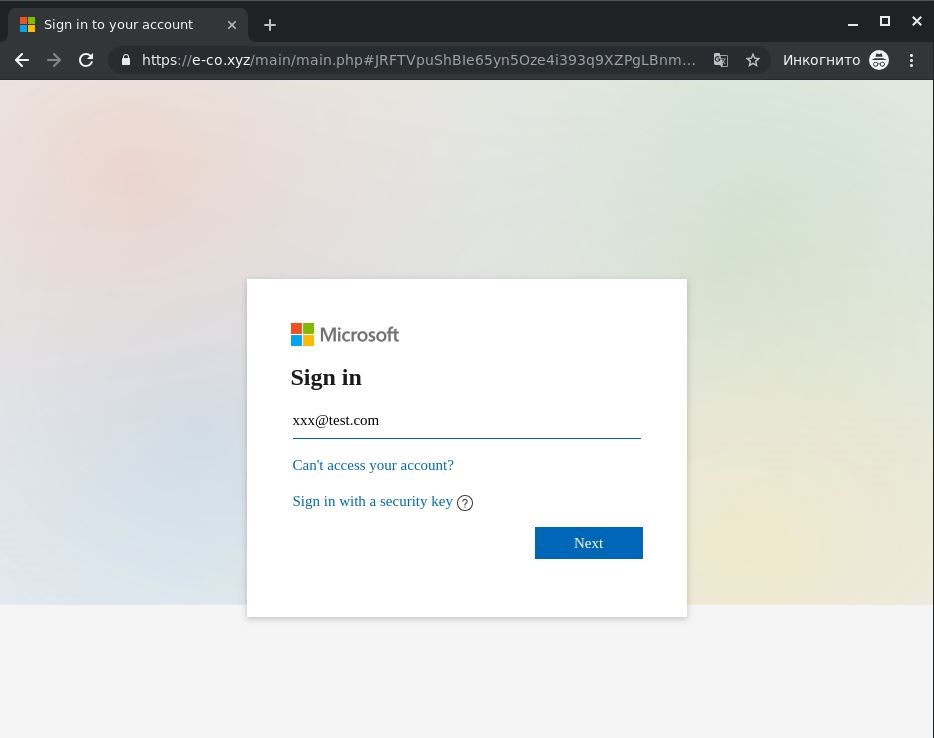
How to recognize a phishing page
Suppose you did click on that attachment and landed on a phishing page. How can you tell it’s not a legitimate site?
Here is what to look at:
- Does the address bar content look like a Microsoft address?
- Do the links “Can’t access your account?” and “Sign in with a security key” direct you where they should? Even on a phishing page, they may well lead to real Microsoft pages, although in our case, they were inactive, a clear sign of fraud.
- Does the window look right? Microsoft normally has no problems with details such as background image scale. Glitches can happen to anyone, of course, but anomalies should raise a flag.
In any case, if you have any doubt, look up https://login.microsoftonline.com/ to see what Microsoft’s actual sign-in page looks like.
How to avoid getting hooked
To avoid giving up your Office account passwords to unknown attackers:
- Pay attention. Use our questions to avoid the simplest forms of phishing. To learn more tricks, try our modern cyberthreat awareness training courses;
- Protect employees’ mailboxes with Office 365 protection to expose phishing attempts with hyperlinks or with attached HTML files, and endpoint protection to prevent the opening of phishing sites.
 phishing
phishing


 Tips
Tips