We constantly reiterate that a multilayered approach is the key foundation for our concept of “True Cybersecurity,” which is able to efficiently defend against next-generation threats. However, what exactly does multilayered mean, and how is it deployed in Kaspersky Lab products?
Actually, we take a multilayered approach in each aspect of all of our products. Let’s see this exemplified by our Kaspersky Endpoint Security for Business. From one end, it uses various technologies to minimize threats: Endpoint hardening, Reputation services, Automatic Exploit Prevention, and more. These function as endpoint protection layers and neutralize the majority of threats even before they hit the antivirus. That’s how we find a perfect balance between performance and efficient protection.
From the other end, if a suspicious file makes it through the initial filtering layers and ends up on a protected endpoint, it’s time for file antivirus — which is also multilayered — to act.
The image above shows how threats are blocked with various layers of the file antivirus.
The first layer constitutes a reliable and ultra-fast technology that detects malware by masks and hashes.
The second layer uses emulation: It runs suspicious code in an isolated environment. Both binaries and scripts are emulated, which is critical for protection against web threats.
The third layer is a classic detection routine. It’s a tool that allows Kaspersky Lab experts to write a code and deliver it directly to the user in databases. This technology is truly irreplaceable; it complements the solution with decryptors for ransomware and unpackers for legitimate packers.
The fourth layer assumes the use of machine-learning models on the client’s end. The models’ high generalization ability helps to prevent the loss of quality in detecting unknown threats, even if an update of databases was not available for more than two months.
The fifth layer is cloud detection using big data: It leverages threat analytics from all endpoints in Kaspersky Security Network, which, in turn, enables unprecedented reaction to new threats and minimizing false positives.
The sixth layer is heuristics based on execution logs. There is no more fail-safe way to catch a criminal than catching him in the act. Instant backup of data impacted by a suspicious process and automated roll-back neutralize malware the moment it’s detected.
The seventh layer involves gathering real-time behavioral insights on files to create deep learning models. The model is capable of detecting a file’s malicious nature while analyzing a minimal amount of instructions. This helps to minimize threat persistence, and machine learning provides high detection rates even when model update is unavailable for a long time.
As you can see, using machine learning on various layers of a file antivirus’ subsystem is, in its very essence, a proof of our multilayer approach, which we internally call ML2, or Multi-Layered Machine Learning.
We use the same Next Gen approach when making other security solutions as well.
 True Cybersecurity
True Cybersecurity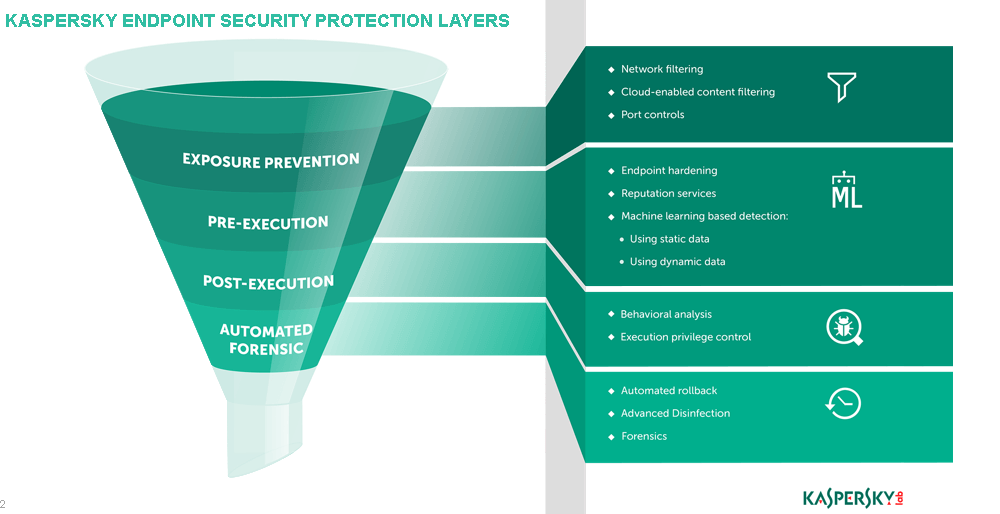


 Tips
Tips