The trend of using spearphishing techniques in mass emails continues to gain momentum. We recently came across a sample email in which attackers used a whole box of relatively sophisticated spearphishing tricks. Now, one might think that use of such tactics for a “mere” mass phishing attack would be somewhat OTT in terms of effort on the attackers’ side; not so – it transpired in this case: the attackers still gave it a shot (though detailed analysis reveals the attack was doomed from the start). In any case, it presented us with an excellent opportunity to take a dive into the techniques employed by phishers.
Email mimicking update of corporate guidelines
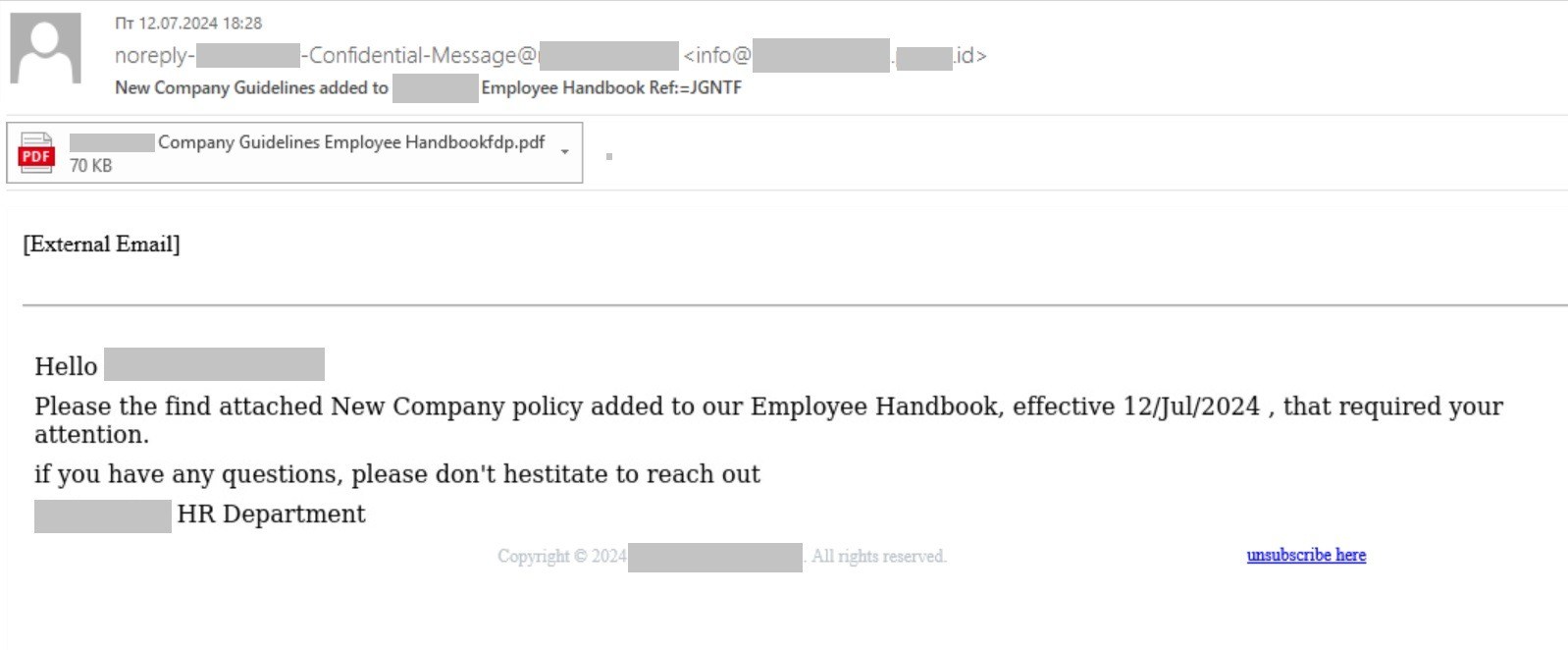
Almost everything about the email is spot on. It’s addressed to a specific individual within a specific organization, and uses ghost spoofing for the sender’s name — that is, the “From” field displays a forgery of the legitimate address of the target company (which, of course, has no relation to the address in the “Reply To” field).
The email is sent through the infrastructure of a reputable marketing company, raising no red flags with email filters. What’s more, the name of this company and the top-level domain hosting its website are deliberately chosen to lull the recipient’s vigilance — the website’s based in Indonesia, and the victim may well perceive the “.id” domain as an abbreviation for “identifier” rather than a country code. Alongside the spoofed address in the “From” field, it looks convincing enough:
But that’s not all. In the email body there’s practically zero text — only a copyright line and an unsubscribe link (both of which, as it happens, are inserted by the mail engine of the legitimate company used to send the message). Everything else, including the recipient’s name, is an image. This is to prevent anti-phishing mechanisms from applying text-based filtering rules.
An attached PDF file is used instead of a direct phishing link for the same reason. Websites can easily be blacklisted and blocked at the mail-server level. A PDF file, on the other hand, appears as a completely legitimate attachment.
PDF attachment
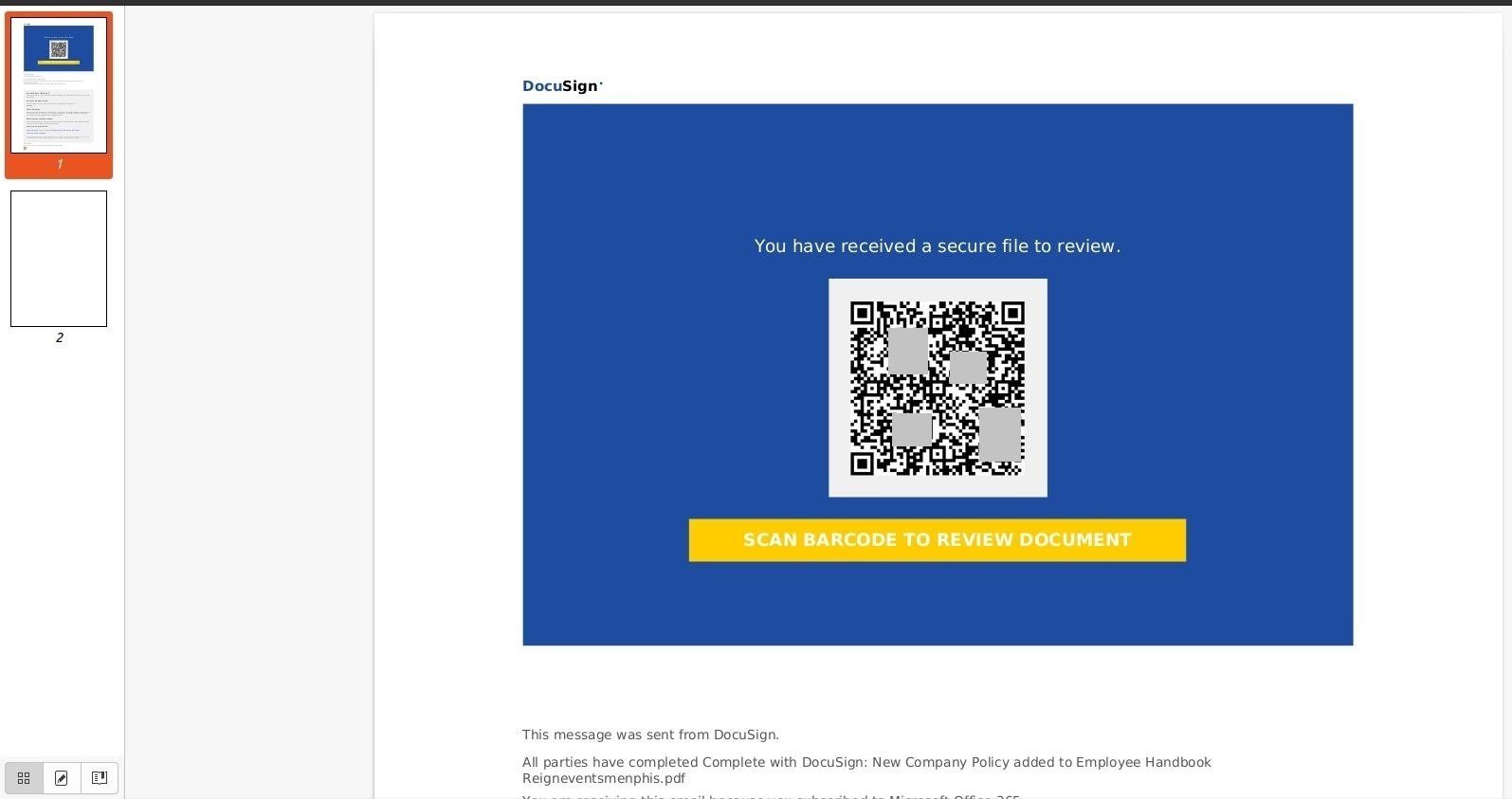
In actual fact, attackers have long been concealing links in PDF files. Thus, in theory, security software should be able to analyze a PDF — including any text and links within. But the creators of this phishing campaign were wise to that as well. Their PDF technically has no text or links in it whatsoever. Instead, it presents another image featuring a QR code and embedded accompanying text.
In addition, the PDF mimics the interface of DocuSign, a well-known service used for electronic document management. DocuSign does indeed allow you to send documents for signing, and to track their status. But, of course, it has nothing to do with PDF files housing a QR code.
At this point, it becomes painfully obvious that the attackers overcooked the attack. The victim receives what seems to be confidential corporate guidelines by email, but to read them they need to scan a QR code with a mobile phone… — not exactly realistic. Most employees won’t bother — especially if they use their own (non-corporate) phone.
Epic fail: the phishing website
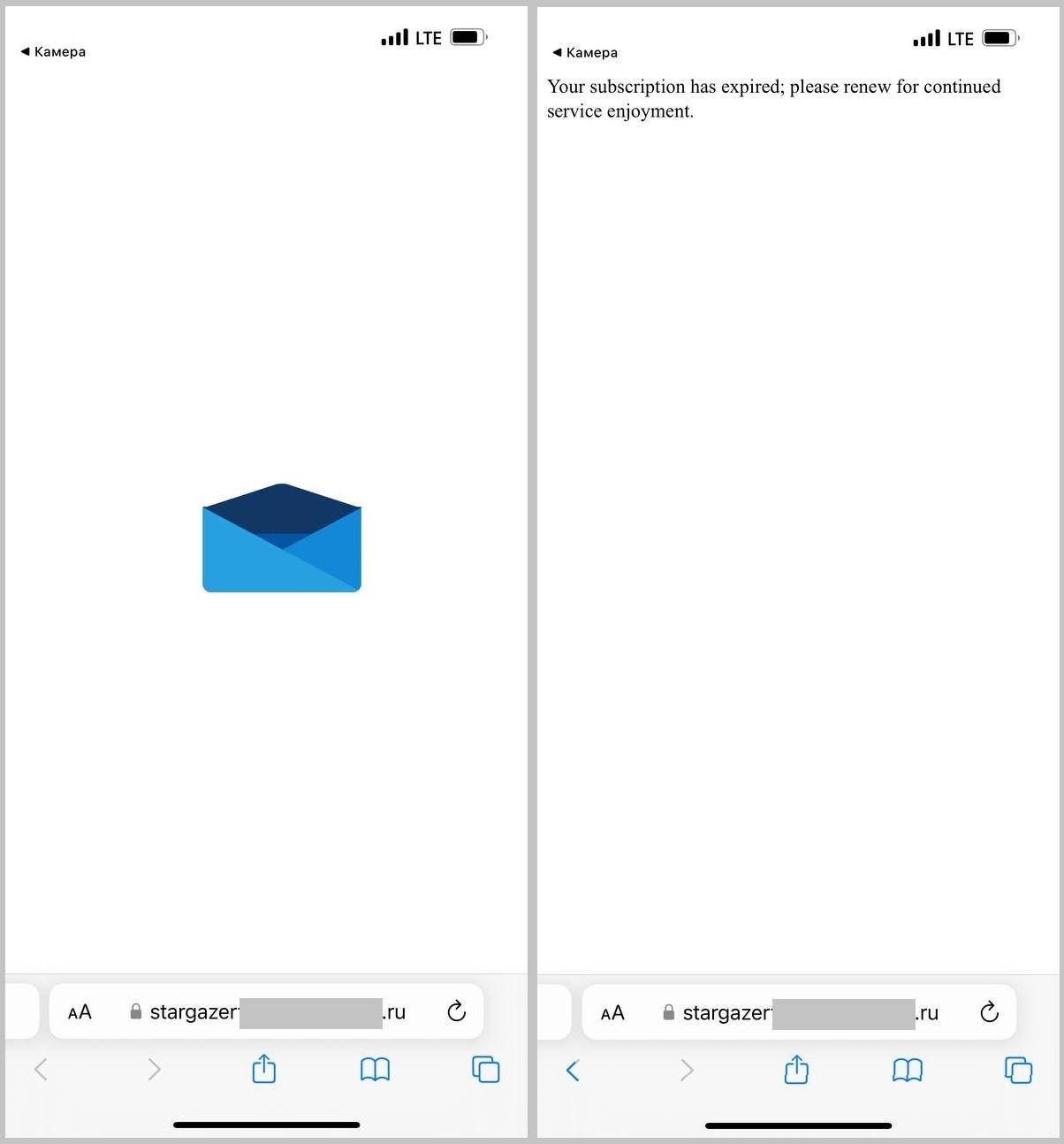
So what happens if the victim does pull out their phone and scan the code? Well, for starters, they’ll be greeted by Cloudflare’s verification system and asked to prove they’re human. Cloudflare is a legitimate service to guard against DDoS attacks, and cybercriminals like to put their phishing pages behind it to add plausibility.
But after that it’s a disaster. The website plays an animation of an envelope opening, then crashes with an error message.
It appears the attackers forgot to renew their subscription to the hosting services. Maybe the site had some more kooky tricks in store for the victim, but by the time the phishing emails were being pumped out, it was already defunct.
How to stay safe
To protect company employees from phishing:
- Secure corporate email at the mail-gateway level.
- Use local security solutions with anti-phishing technologies on all work devices (including mobile ones).
- Inform employees of the latest phishing tricks (for example, by pointing them toward our posts regarding signs of phishing).
- Hold regular cybersecurity awareness training for staff.
 signs of phishing
signs of phishing

 Tips
Tips