Android is a good operating system whose developers truly care about security, but with so many OS versions and applications, keeping an eye on all of them is a tall order. Therefore, new ways to circumvent the built-in security mechanisms surface fairly often. The latest way to hack Android is called “Man-in-the-Disk,” and that is what we are going to talk about.
“Sandboxes,” the foundation of Android security
A key Android principle is that all applications must be isolated from one another. This is achieved through the use of so-called sandboxes. Each application, together with its private files, lives in a “sandbox” that other applications cannot access.
The idea is to keep a malicious application, even if it infiltrates your Android device, from stealing data that other, good applications store, such as the username and password of your online banking app, or your message history. It’s no surprise that hackers are hard at work looking for new ways to circumvent the mechanism, pursuing something called a “sandbox escape.” They succeed, too, from time to time.
For example, Slava Makkaveev’s speech at DEF CON 26 focused on how an application with no particularly dangerous or suspicious permissions can escape the sandbox. He dubbed the method “Man-in-the-Disk,” after the well-known Man-in-the-Middle type of attack.
How the Man-in-the-Disk attack works
Apart from the sandbox areas that house application files, Android has a shared external storage, appropriately named “External Storage.” An application must ask the user for permission to access the storage: “Access photos, media and files on your device” (that is effectively two permissions – READ_EXTERNAL_STORAGE and WRITE_EXTERNAL_STORAGE). These privileges are not normally considered dangerous, and nearly every application asks for them, so there is nothing suspicious about the request.
Applications use external storage for lots of useful things, such as to exchange files or transfer files between a smartphone and a computer. However, external storage is also often used for temporarily storing data downloaded from the Internet: First, the data is written to the shared part of the disk, and only then transferred to an isolated area that only that particular application can access.
For example, an application may temporarily use the area to store supplementary modules that it installs to expand its functionality, additional content such as dictionaries, or updates. The problem is that any application with read/write access to the external storage can gain access to the files and modify them, adding something malicious.
In a real-life scenario, you may install a seemingly harmless application, such as a game, that may nevertheless infect your smartphone with something truly nasty.
The creators of Android actually realize that use of the external storage may be dangerous, and the Android developer site even features a few helpful tips for app programmers.
The problem is that not all app developers, not even Google employees or certain smartphone manufacturers, follow the advice. Examples presented by Slava Makkaveev include exploitation of the vulnerability in Google Translate, Yandex.Translate, Google Voice Typing, and Google Text-to-Speech, as well as system applications by LG and the Xiaomi browser.
By the way, Google researchers recently discovered that the very same Man-in-the-Disk attack can be applied to the Android version of a very popular game, Fortnite. To download the game, users need to install a helper app first, and it is supposed to download the game files. Turns out, using the Man-in-the-Disk attack, someone can trick the helper into installing a malicious application. Fortnite developers – Epic Games – are aware of this vulnerability and have already issued a new version of the installer. So if you’re into Fortnite, use version 2.1.0 or later to stay safe. If you have Fortnite already installed, uninstall and then reinstall it from scratch using the aforementioned version.
How to protect your Android from the Man-in-the-Disk attack
Makkaveev singled out just a few really popular apps to demonstrate how bad things are, but vulnerable apps are likely numerous.
How can you protect yourself? We have a few tips that are easy to follow:
- Install applications only from official stores such as Google Play. Malware does creep in, but it is far rarer — and removed on a regular basis.
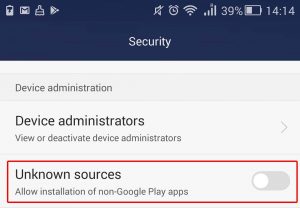
- Disable the installation of applications from third-party sources in your smartphone or tablet settings; those are the most dangerous sources. To do that, select Settings -> Security and uncheck Unknown sources.
- Choose applications by verified developers. Check the application rating and read the reviews. Avoid installing anything that looks fishy.
- Do not install anything you do not need. The fewer apps you have on your smartphone, the better.
- Remember to remove applications you no longer need.
- Use a reliable mobile antivirus application that will give you a timely notification if a malicious app is trying to penetrate your device.
 DEF CON
DEF CON

 Tips
Tips