Users tend to think it’s safe to install apps from Google Play. After all, it’s the most official of all official stores for Android, and all apps there are thoroughly vetted by Google moderators, right?
Bear in mind, however, that Google Play is home to more than three million unique apps, most of which get updated regularly, and to vet all of them thoroughly — that is, really thoroughly — is beyond the resources of even one of the world’s largest corporations.
Well aware of this, makers of malicious apps have developed a number of techniques to sneak their creations onto Google Play. In this post, we take a look at the most headline-grabbing cases of 2023 regarding malicious apps on the official Android store, with total downloads in excess of — wait for it — 600 million. Let’s go!…
50,000 downloads: infected iRecorder app eavesdrops on users
Let’s start with the fairly minor, but quite interesting and highly illustrative case of iRecorder. This unremarkable screen-recording app for Android smartphones was uploaded to Google Play in September 2021.
But then, in August 2022, its developers added some malicious functionality: code from the remote access Trojan AhMyth, which caused the smartphones of all users who had installed the app to record sound from the microphone every 15 minutes and send it to the server of the app creators. By the time researchers discovered the malware in May 2023, the iRecorder app had been downloaded more than 50,000 times.
This example demonstrates one of the ways in which malicious apps creep into Google Play. First, cybercriminals upload an innocuous app to the store that’s guaranteed to sail through all moderation checks. Then, when the app has built an audience and some kind of reputation (which can take months or even years), it’s augmented with malicious functionality in its next update uploaded to Google Play.
620,000 downloads: Fleckpe subscription Trojan
Also in May 2023, our experts found several apps on Google Play infected with the Fleckpe subscription Trojan. By that time, they’d already chalked up 620,000 installs. Interestingly, these apps were uploaded by different developers. And this is another common tactic: cybercriminals create numerous developer accounts in the store so that even if some get blocked by the moderators they can just upload a similar app to another account.
When the infected app was run, the main malicious payload was downloaded to the victim’s smartphone, after which the Trojan connected to the command-and-control server and transferred country and cellular operator information. Based on this information, the server provided instructions on how to proceed. Fleckpe then opened web pages with paid subscriptions in a browser window invisible to the user, and by intercepting confirmation codes from incoming notifications subscribed the user to needless services paid for through the cellular operator account.
1.5 million downloads: Chinese spyware
In July 2023, Google Play was found to be hosting two file managers — one with one million downloads, the other with half a million. Despite the developers’ assurances that the apps don’t collect any data, researchers found that both transmitted a lot of user information to servers in China, including contacts, real-time geolocation, data about the smartphone model and cellular network, photos, audio and video files, and more.

File managers on Google Play with Chinese spyware inside. Source
To avoid being uninstalled by the user, the infected apps hid their desktop icons — another common tactic used by mobile malware creators.
2.5 million downloads: background adware
In a recent case of malware detection on Google Play in August 2023, researchers found as many as 43 apps — including, among others, TV/DMB Player, Music Downloader, News, and Calendar — that secretly loaded ads when the user’s smartphone screen was off.

Some of the apps with hidden adware. Source
So as to be able to carry out their business in the background, the apps requested the user to add them to the list of power-saving exclusions. Naturally, affected users experienced reduced battery life. These apps had a combined total of 2.5 million downloads, and the target audience was primarily Korean.
20 million downloads: scammy apps promise rewards
A study published in early 2023 revealed several shady apps on Google Play with more than 20 million downloads between them. Positioning themselves primarily as health trackers, they promised users cash rewards for walking and other activities, as well as for viewing ads or installing other apps.
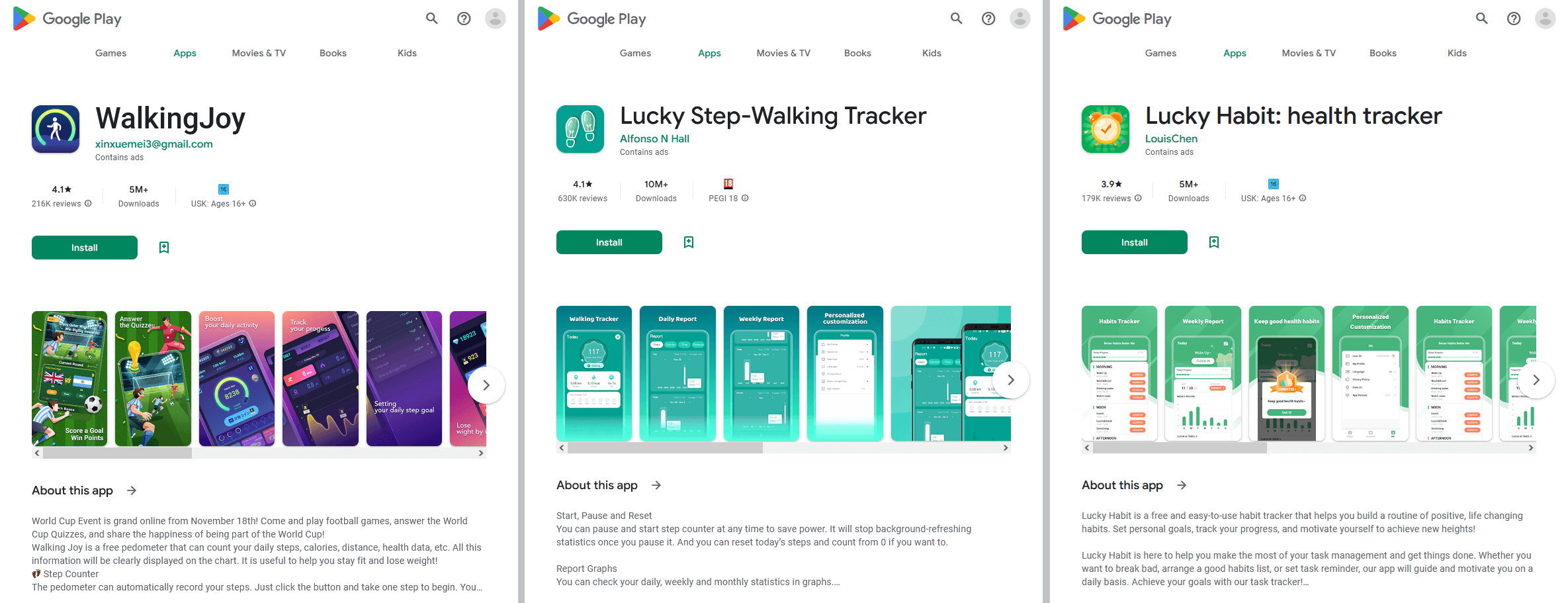
Apps on Google Play promising rewards for walking and viewing ads. Source
More precisely, the user was awarded points for these actions, which could then supposedly be converted into real money. The only trouble was that to get a reward, you had to amass such a huge number of points that it was effectively impossible.
35 million downloads: Minecraft clones with adware inside
Google Play also became home to malicious games this year, with the main culprit (and not for the first time) being Minecraft — still one of the most popular titles in the world. In April 2023, 38 Minecraft clones were detected in the official Android store, with a total of 35 million downloads. Hidden inside these apps was adware called, appropriately enough, HiddenAds.

Block Box Master Diamond — the most popular of the Minecraft clones infected by HiddenAds. Source
When the infected apps were launched, they “displayed” hidden ads without the user’s knowledge. That didn’t pose a serious threat per se, but such behavior could have affect device performance and battery life.
And those infected apps could always be followed up later by a far less harmless monetization scheme. This is another standard tactic of Android malware app creators: they readily switch between different types of malicious activity depending on what’s profitable at any given moment.
100 million downloads: data harvesting and click fraud
Also in April 2023, another 60 apps were found on Google Play infected with adware that researchers dubbed Goldoson. These apps collectively had more than 100 million downloads on Google Play and a further eight million on the popular Korean ONE store.
This malware also “showed” hidden ads by opening web pages within the app in the background. In addition, the malicious apps collected user data — including information about installed apps, geolocation, addresses of devices connected to the smartphone via Wi-Fi and Bluetooth, and more.
Goldoson seems to have gotten into all these apps along with an infected library used by many legitimate developers that were simply unaware that it contained malicious functionality. And this isn’t an uncommon occurrence: often malware creators don’t develop and publish apps on Google Play themselves, but instead create infected libraries of this kind that end up in the store along with other developers’ apps.
451 million downloads: mini-game ads and data harvesting
We close with the biggest case of the year: in May 2023, a team of researchers found a whopping 101 ineligible apps on Google Play, with combined downloads of 421 million. Lurking inside each and every one of them was a SpinOk code library.
Shortly after that, another team of researchers discovered 92 more apps on Google Play with the same SpinOk library, with a slightly more modest number of downloads — 30 million. In all almost 200 apps containing SpinOK code were found, with a total of 451 million downloads from Google Play between them. This is another case where dangerous code was delivered into applications from a third-party library.
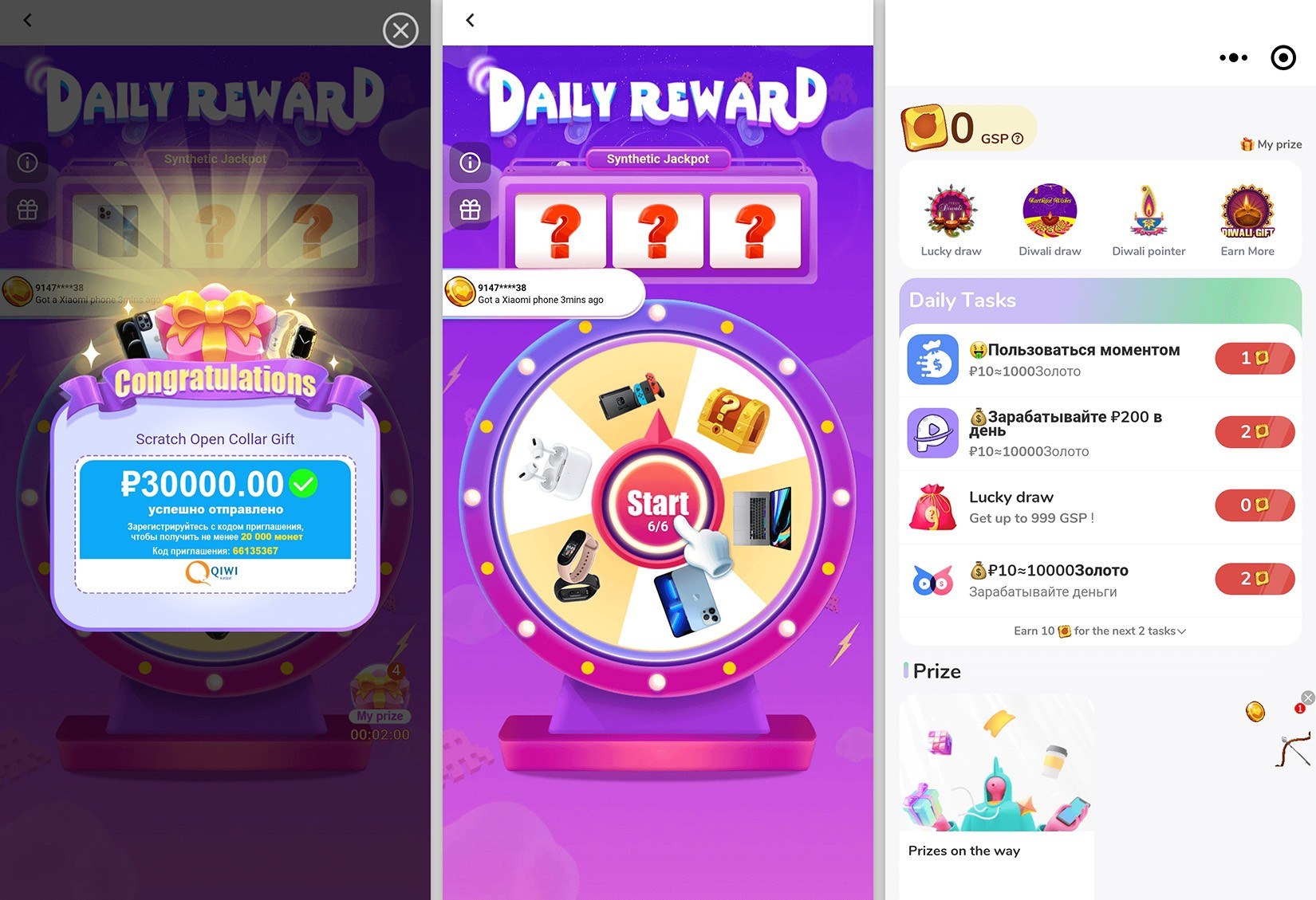
Mini-games promising “rewards” that showed users applications containing SpinOk code. Source
On the surface, the infected apps’ task was to display intrusive mini-games promising cash rewards. But that wasn’t all: the SpinOK library had the ability to collect and send user data and files to its developers’ command-and-control server in the background.
How to guard against malware on Google Play
Of course, we haven’t covered all the cases of malicious apps getting onto Google Play in 2023 — only the most eye-catching. The main takeaway from this post is this: malware on Google Play is far more common than any of us would like to think — infected apps have a combined download total in excess of half a billion!
Nevertheless, official stores remain by far the safest sources. Downloading apps elsewhere is far more dangerous, for which reason we strongly advise against it. But you must exercise caution in official stores as well:
- Every time you download a new app, carefully check its page in the store to make sure it’s genuine. Pay particular attention to the name of the developer. It’s not unusual for cybercriminals to clone popular apps and place them on Google Play under similar names, icons, and descriptions to lure users.
- Don’t be guided by the app’s overall rating, since this is easy to inflate. Rave reviews are also no trouble to fake. Instead, focus on negative reviews with low ratings — that’s where you can usually find a description of all the problems with the app.
- Make sure to install a reliable protection on all your Android devices, which gives an advance warning if a Trojan tries to sneak onto your smartphone or tablet.
- In the free version of our Kaspersky for Android application, remember to manually run a device scan from time to time, and be sure to perform an antivirus scan after installing any new app and before launching it for the first time.
- In the paid version of our protection suite — which, incidentally, is included in a subscription to Kaspersky Standard, Kaspersky Plus or Kaspersky Premium — scanning is performed automatically, keeping you safe from infected apps.
 Android
Android

 Tips
Tips