A role-based approach to overcoming this year’s challenges
A year like no other
There is no doubt that 2020 was a year like no other. The pandemic that gripped the planet led to accelerated digital transformation across nearly every industry. The home office became the only office for millions of workers. This in turn presented new cybersecurity headaches for organizations across the globe.
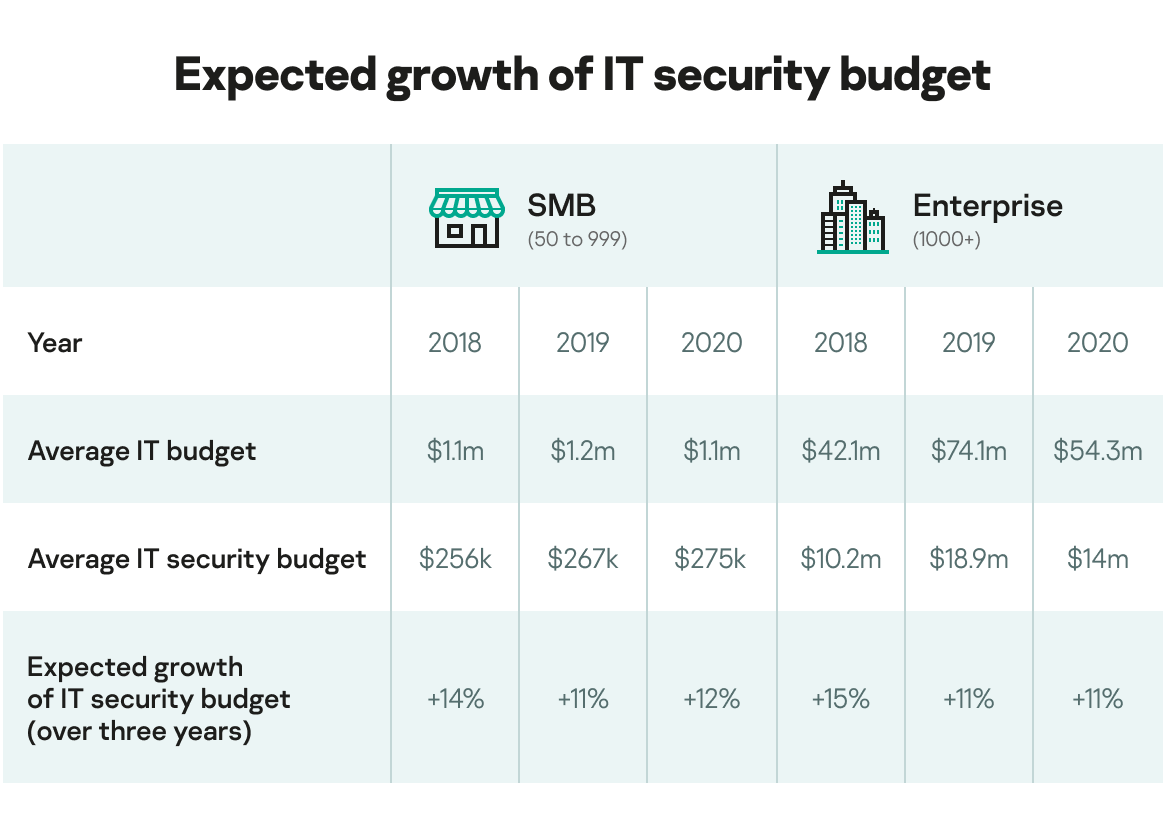
The stark reality is that, as the risk of cyberattacks continues to rise, IT teams are being asked to do more, with less. In fact, Kaspersky has found that the average IT security budget for enterprises for this year was $14 million – a drop of over a third (26%) compared to 2019. Similarly, the average IT budget dropped by 27% to $54.3 million. What’s more, looking at the entire three-year period in the chart below, there have been some minor contradictions. For instance, enterprises and SMBs expect IT security budgets will increase by 11% and 12%, respectively, but this may not correlate to monetary value in reality. While there is a trend for the share of IT security spending to grow in the overall IT budget, experts predict a decline in investments made in IT.
Role-based predictions
In these constantly changing times, Kaspersky conducted research with both enterprises and SMBs to learn more about their approach to IT security economics, to create a series of reports including: ‘Investment adjustment: aligning IT budgets with changing security priorities‘ and ‘How businesses can minimize the cost of a data breach’.
Whether a business is a blue-chip enterprise or a disruptive SMB, this particular report provides an overview of the specific IT security and economic challenges that organizations and different stakeholders will need to address in 2021. To navigate to the section covering your dedicated cybersecurity forecast and recommendations, choose one of the following roles that best fits your current responsibilities:
- CEO – I am the main decision-maker and strategist who needs to understand overall cybersecurity trends and the main issues the company must deal with now and in the future
- CIO/CISO – I am a general technology and/or cybersecurity decision-maker who needs to understand the main cybersecurity risks for my business, as well as support the business’ changing technology requirements by deciding on the right resources and investments to meet our goals
- Head of SOC/SOC team lead – I am the main decision-maker for the security operation center who needs to understand what technologies and talents will be necessary for continued effective operation
- IT security manager/IT manager responsible for cybersecurity tasks – I need to know about the best protection technologies to address the growing scourge of cyberattacks or enable suitable protection for my company even with minimal resources
Methodology and contributors
The Kaspersky Global Corporate IT Security Risks Survey (ITSRS) interviewed a total of 5,266 IT business decision-makers across 31 countries in June 2020. Respondents were asked about the state of IT security within their organizations, the types of threats they face and the costs they have to deal with when recovering from attacks. Kaspersky also interviewed internal and external experts for their opinions on the impact on IT security and how businesses can mitigate expected cybersecurity challenges: Alexander Moiseev, Chief Business Officer at Kaspersky; Damir Shaykhelislamov, Advanced Threat Protection Solutions Group Manager at Kaspersky; Konstantin Voronkov, Head of SMB Product Management at Kaspersky; Veniamin Levtsov, Vice President of B2B Solutions at Kaspersky; Vladimir Kuskov, Head of Advanced Threat Research and Software Classification at Kaspersky, Nicola Sotira, Head of CERT of Poste Italiane S.p.A and Daniel Sanz, CISO at Deloitte.
Throughout the report, businesses are referred to as either SMBs (small and medium sized businesses with 50 to 999 employees), or enterprises (businesses with over 1,000 employees). Not all survey results are included in this report.
Forecasts and recommendations for CEOs
The need for staff to work from home when the world was in the grip of the pandemic caused a paradigm shift in attitudes towards remote working. After seeing seemingly no reduction in productivity, companies such as Facebook and Twitter announced that their employees could opt to continue working from home even after the coronavirus crisis eases. Global Workplace Analytics went so far as to estimate that between 25% and 30% of US employees will be working from home multiple days a week by the end of 2021.
Perhaps unsurprisingly, employees themselves have embraced the change and want more flexibility to their working practices moving forward. In fact, Kaspersky research has revealed that almost three quarters (74%) of employees wanted to keep a hybrid approach to working in the future.
To better protect an increasingly dispersed workforce in conditions of possible financial constraints, cloud services and the outsourcing of IT and security tasks will gain more traction in the coming year. Seven-in-10 (69%) businesses surveyed said they already plan to use a managed service provider (MSP) or managed security service provider (MSSP) in the next 12 months. This is for good reason as the service model is key to CEOs minimizing their capital investments and transitioning the business costs from CapEx into OpEx.
As Veniamin Levtsov, Vice President of B2B Solutions at Kaspersky explains:
“The transition to a service model involves minimizing investment in the moment, which is important in an unstable economic situation in which we all find ourselves. IT and IT security costs are spread over time, reducing the financial burden on the company. This model is also more flexible and can change as the business grows.”
Konstantin Voronkov, Head of SMB Product Management at Kaspersky warns of the dangers of trying to do too much internally:
“The most expensive option is to grow your own security expertise for mid-size and small companies. Qualified experts will be overpaid, and the churn is high as they often have limited scope to develop themselves.”
“In the short term, buying your own infrastructure might seem cost effective. However, when it comes to maintenance, replacement, scalability, fault tolerance requirements, flexibility, service scalability, availability, and many other aspects, the price for personnel or business idle time is double or even higher. It is important to pay attention to long term costs. Many out-of-the-box solutions available for customization are already ready to use within a software as a service (SaaS) model.”
Key takeaways:
- The working from home trend is here to stay, with employees supporting the move away from traditional offices to a hybrid office/home model
- Transition to a service model enables required levels of IT and IT security with lower investments
- Using MSPs and MSSPs helps turn CapEx into OpEx
Daniel Sanz, CISO at Deloitte, predicts that the full consequences of the SolarWinds attack are still yet to be seen by both medium-sized and large enterprises. Helping staff maintain cybersecurity practices when working from home will remain vital for many industries during the year to come:
In 2020, COVID-19 changed the world for both consumers and businesses. The pandemic has drastically altered our behaviors across the globe, from the way we connect to other people, the way we make purchases and the way we work. Some of these changes are going to stay with us forever, partly because the pandemic has been the accelerator we’ve all needed to bring more digitalization into our lives.
Digitalization has progressed over the last few years at different speeds, depending on its requirement in various countries or regions, and COVID-19 has drastically sped up this progress. It has also brought some vulnerabilities in the way we collaborate, communicate or work to the fore. This trend from the last few months of 2020 became a key challenge for both medium-sized businesses and large enterprises, and is likely to remain the case in the year ahead.
Business faced issues during the second quarter of 2020 relating to remote working. Having to solve technical issues became a colossal problem for smaller companies as well as bigger ones that were not well prepared. It is now time to transition the security posture we had while working from offices to a new climate with so many employees working from home.
We need to approach security measures in remote settings with the same level of attention as we would have done in traditional office spaces. Unfortunately, depending on the kind of business, this can be a challenging task. For example, security covers a wide range of areas, such as the (mis)use of physical papers, the destroying of assets or simply the returning of devices when people leave a business, and these have the potential to create incidents during 2021. While this is likely to happen in the first half of the year, the second half will hopefully see the return of companies operating from offices. This move may cause confusion in IT departments, as they could lose their focus on day-to-day maintenance activities.
If that does happen, it is the perfect breeding ground for criminal organizations to perform attacks. The methods they use will likely be the same as the ones we have observed over the last few years. These methods are often simple to perform and offer a great return on their investment. Phishing campaigns that infect companies with ransomware or other malware to easily monetize attacks will be the most common attack vectors, while spear-phishing attacks will continue to decrease. Double-extortion attacks are likely to increase, and we may even see ransom demands disappear. Companies will have enough to worry about, as it will become more likely they will experience leaked data reaching the dark web.
At the same time, the SolarWinds issue will be a trending topic for at least the first few months of the year. The issue transcends a common attack and the consequences are yet to be discovered. Researchers will firstly need to analyze what happened to discover what the attackers’ real objectives were. For most analysts, it doesn’t seem that FireEye was the ultimate objective of this attack and, depending on the real objectives, a lot of new related vulnerabilities will be disclosed in the first quarter of 2021. It is likely that security and IT organizations will have a lot of out-of-cycle patches to action. Likewise, the incident will have political and economic consequences. The media and politicians will use this issue as an argument to justify their positions, and countermeasures will be implemented on government agencies with or without a valid reason behind them. What may follow is security budgets increasing all over the world.
Focusing on how countermeasures may be applied, in 2021 the use of AI and other automation techniques will foster, and SOC teams and applications around the globe will begin to use them in a much more generalized way.
In general, 2021 is starting with a lot of corporate challenges, but that does not mean we should expect any drastic change to how companies currently approach security. However, this year is going to be a very busy and interesting, in which we should still be focusing on protecting against malware threats. E-mail protection and other perimeter protections are still important, but ultimately, due to various reasons, malware is going to be downloaded onto more end user devices.
Of course, avoiding that is our job, but when all the elements in the different layers of protection fail, what we usually have is a situation where it is paramount to ensure there is good protection on end user devices. It is important not to forget this basic principle in 2021.
Forecasts and recommendations for CIOs/CISOs
As workers are now so dispersed, simply protecting the perimeter is no longer an effective strategy. The principles of the past decade will have to change. Global headquarters will turn into regional offices, and local offices will turn into micro-offices that staff only visit on occasions. CIOs/CISOs can no longer consider everything going on inside the network as ‘trusted’ and that outside as ‘untrusted’. Nothing is so black and white anymore. Organizations need to reconsider their approach so that they can protect their workforce, wherever they reside.
“As office networks expand to include micro-offices in employees’ homes, we assume that the concept of cybersecurity assessment and certification of home workspace environments will become best practice. There should be tools that allow cybersecurity teams to scan the level of security in a workplace – from the presence of software vulnerabilities to connecting to an unreliable or unprotected Wi-Fi hotspot. Also, all remote employees who have access to sensitive, confidential information of course will have to follow strict cybersecurity policies and be equipped with corporate computers that have all the necessary protection installed,” says Veniamin Levtsov.
The onus will be on the workforce more than ever in 2021. Employees must be prepared for the need to protect themselves. Cybersecurity awareness measures and training have never been so important. It is a case of safety in numbers. Effectively mitigating the impact of a cyberattack will only work if staff are properly educated on the possible threats, as well as how to avoid them. People have to see that new skills are relevant to their everyday life. Any training course has to be practical, up-to-date and relevant. Education needs to go beyond just being a box ticking exercise on the compliance sheet.
Unfortunately, this has come at a time when there remains a global cybersecurity skills shortage, with cybersecurity professions split into very narrow specializations such as database security experts, personal data protection experts or network security specialists – as well as others. Talent investment was already a key component of the IT budget last year, and that won’t change overnight. However, hiring staff for each specific role may be too expensive for smaller businesses and even unprofitable for larger enterprises. This is where outsourcing can help plug the gap. It allows organizations to save money on hiring expensive cybersecurity specialists. However, this shouldn’t be an excuse to skimp on internal training for cybersecurity staff. Even those businesses that outsource key cybersecurity components still need to focus on developing management skills for their in-house teams to handle those outsourced functions.
“In 2021 it will be necessary to invest in the expertise of in-house specialists to make staff more cloud-oriented and enable the transfer of working areas to external service providers,” predicts Levtsov. “As cybersecurity splits into different very narrow professions, it is too costly to hire a whole range of experts. There is also the challenge of keeping the best professionals as market demand grows. The way out of this is to attract trusted MSSPs. Using their services helps reduce the risk of a shortage of specialists. However, it is important to develop internal IT security competence to speak the same language as service providers. Make sure you boost your IT specialists’ management skills too.”
Flexibility of operations will come through an increased reliance on cloud services in 2021. According to IDG’s most recent Cloud Computing Survey, almost a third (32%) of the IT budget will be allocated to cloud services in the next 12 months. “To get flexibility, the business should plan to replace legacy software tools and move infrastructure to the cloud. There is a need to find a reliable partner and implement the right solutions for cloud and remote scenario protection. Tools I would recommend include those that provide shadow IT control for cloud application visibility and management, content filtering for cloud services, user behavior monitoring and control, remote management tools with no personal presence, and mobile device visibility and management,” says Voronkov.
Key takeaways:
- Protecting the perimeter is no longer enough
- Cybersecurity awareness measures have never been more important, but they should be practical, relevant and applicable in real life outside of the working environment
- Don’t skimp on training for internal IT security specialists but move them into management roles
- There will be an increased reliance on cloud services so dedicated management and protection measures will be necessary
Nicola Sotira, Head of CERT of Poste Italiane S.p.A. outlines the main cybersecurity challenges for enterprises and small businesses for the next year and warns that all new digital services should be built with cybersecurity in mind:
There was a rapid adoption of remote working, along with extremely fast infrastructural changes for companies throughout 2020. These changes have impacted small and large companies that, due to the pandemic, had to make corporate infrastructures even more readily available remotely. This scenario will not change in 2021, but it has sparked a digitization process that was previously just an idea, but can now be put into practice.
Next year, cybercriminals will increasingly try to leverage user behaviors and habits with their techniques. Employees have gone from an on-premise scenario to becoming remote workers, often changing technologies and operating methods as a result. This scenario was immediately exploited by cyberattackers, who launched sophisticated phishing campaigns and ransomware activity, looking for weak points in the postural change that not everyone was prepared to face.
This situation will not change in the year ahead and companies will need to offer better support for staff using their own devices for work purposes, with appropriate policies and tools. The pandemic and the widespread enabling of remote working on a large scale means this issue will require particular attention.
Even VPNs, now widely adopted to enable remote working, will need to be reviewed in the long-term as they can cause latencies, often hinder productivity, and also present scalability problems – including controlling access to internal resources in a more granular way to avoid staff being given permissions that do not match their roles.
The implementation of Zero Trust Network architectures is going to be a key challenge in the coming years, as there will an increase in smart working and companies must ensure scalable and effective security.
Cybercrime has also thrived thanks to fraud perpetrated through emails, with a marked increase in Business Email Compromise (BEC). This phenomenon will continue, given the monetary rewards fraudsters can generate if their activity is successful. This threat will have a substantial impact on victims’ portfolios in 2021, particularly for SMEs. A lot of work still needs to be done to raise awareness, as well as increase levels of protection offered by e-mail protection platforms that will be subjected to more sophisticated user-driven attacks than before.
Finally, the digitalization process forced by COVID-19 will continue steadily across all organizations for the next few years. The adoption of new technologies such as 5G and the extensive use of the cloud will allow companies to achieve greater innovation, together with scalability and simplicity driven by models increasingly oriented to user experience, machine learning and artificial intelligence. Security will have to match these models and adapt and carry out fundamental tasks, to enable new digital services and lay the foundations for a trusted and secure digital ecosystem.
Forecasts and recommendations for heads of SOC/SOC team leads
Unfortunately, almost four-in-ten (38%) enterprise organizations have experienced a targeted cyberattack in the past year. Also, as highlighted in the IT security economics 2020 executive summary, over a quarter (28%) of enterprises are particularly worried about the challenge of data loss from a targeted attack. Whilst it is important to know the latest threats to the enterprise in order to prevent such an attack, it is not enough to just stop specific malware. Security Operation Center (SOC) team leads need to go deeper and understand the attackers’ intentions: what they want to do, how and with what tools, what the targets are, and to what extent they may have already succeeded. This is a strategic story of the confrontation between two groups – attackers and security operation teams.
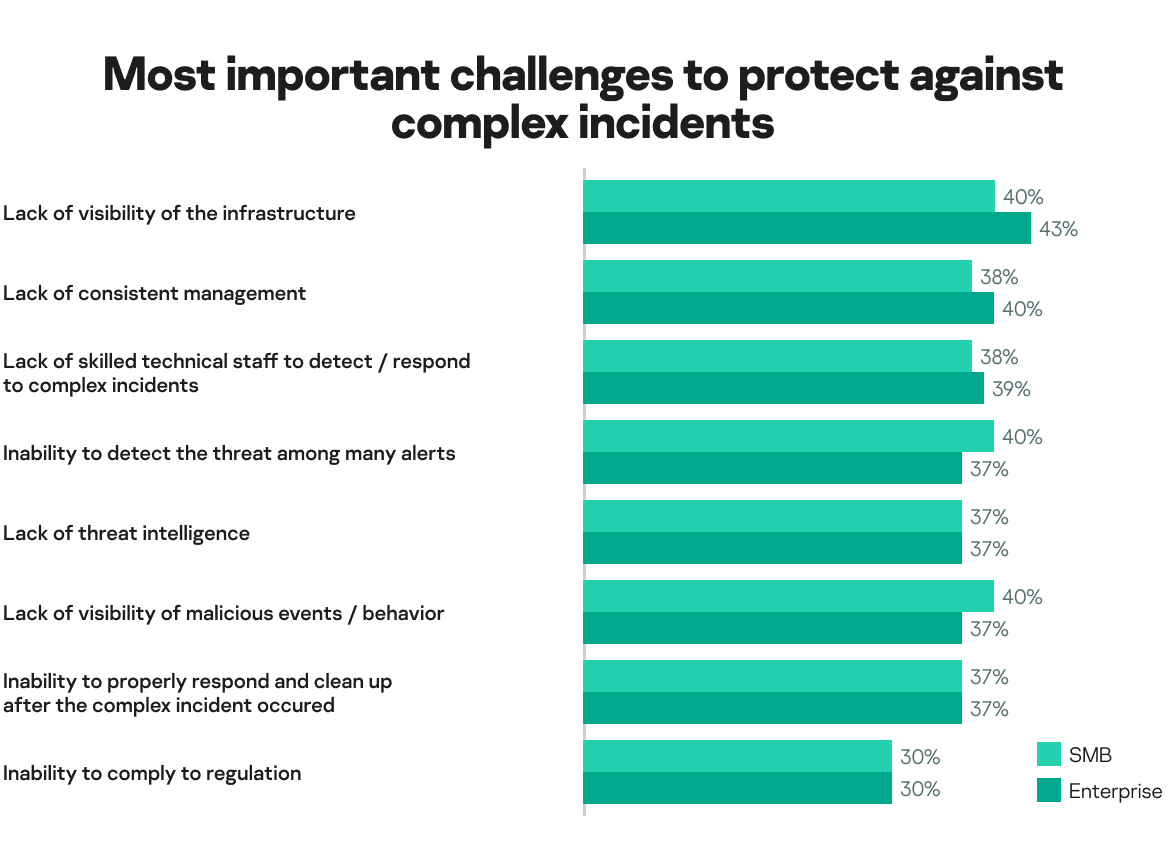
The need for deeper threat analysis and modeling, as well as a more proactive approach to threat detection and response, is paramount. However, at present, security analysts (43%, according to the graph below) confirm that they do not have a clear picture of the whole company’s IT landscape. It is therefore important to have a solution that can automatically integrate and correlate threat indicator data across multiple vectors (whether that be endpoints, cloud, network or email) and respond to it through a single interface. It enhances overall detection accuracy and minimizes analyst overload. It’s about knowing where to look. Only then can targeted attacks be detected effectively, even if the alerts across the systems are very minor.
Here is a list of the challenges that were deemed most important when it comes to protection from complex cybersecurity incidents within an organization:
“In the past, targeted attacks were a synonym of APT attacks conducted by nation-sponsored actors. Now that’s different. Ransomware campaigns brought targeted, human-operated attacks to a new level, making them almost as widespread as common malware,” comments Vladimir Kuskov, Head of Advanced Threat Research and Software Classification at Kaspersky. “Organizations without mature security teams should consider investing in light EDR solutions and managed detection and response services. External SOC experts with deep expertise in detection and investigation of targeted attacks will detect suspicious activity in the organization network, analyze it and report an incident. This means an attack will be detected at its early stage, and the customer will be saved from the ransomware attack disaster.
“Similarly, organizations with mature security teams should use a reliable full scale EDR solution to achieve early detection and prevention of targeted attacks. A managed detection and response service is also useful for the same purpose as described above. But also, an MDR service can provide a second opinion even if the organization already has its own SOC team.”
Key takeaways:
- Almost four-in-ten enterprises (38%) have experienced a targeted cyberattack in the past year
- In order to understand threat actors’ overall attack goal and to what extent it is has been achieved, SOC staff need summarized information on the specific malefactor; including, for example, suspected country of origin and main activity, malware families used, industries and geographies targeted, and descriptions of all tactics, techniques and procedures used
- There is a need to correlate indicators of an attack across multiple vectors for threat hunting needs
- Outsourcing detection and response functions can help both medium and large enterprises improve response efficiency
Forecasts and recommendations for the IT security managers/IT managers responsible for cybersecurity tasks
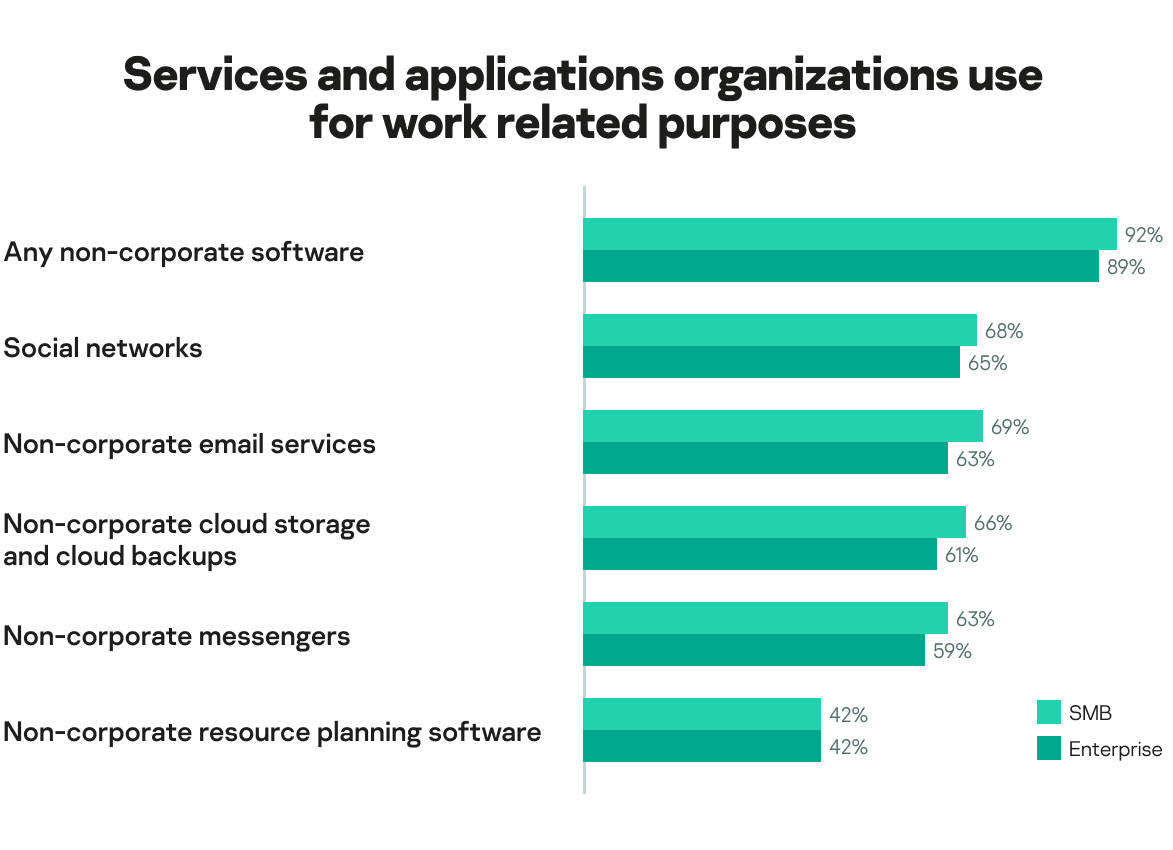
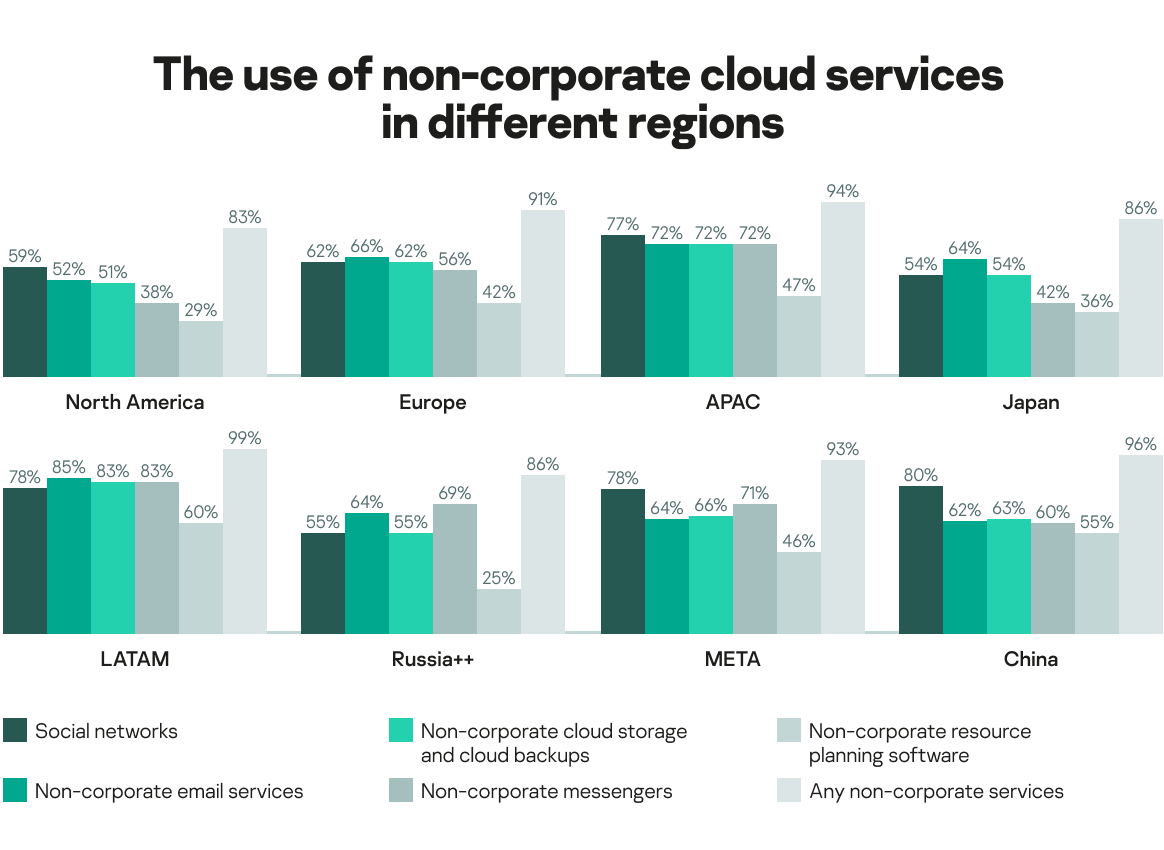
Employees being forced to work from home in 2020 has led to the inevitable merger of their private and professional lives. Today, most companies (89% enterprises and 92% SMBs) have non-corporate approved software and cloud services such as social networks, messengers or any other applications that are for use in the workplace. This is unlikely to change when staff return to the office.
In Europe, 91% of businesses are using some non-corporate services. This number rises to 94% in APAC and 99% in Latin America.
In the era of increasingly stringent data regulations, such as GDPR and others, to ensure that any corporate data is kept under control, better visibility over cloud access will be necessary in 2021. We also predict an increased demand for technologies that provide account and user access management, data loss prevention (DLP) and user behavior analytics (UEBA) too.
In addition to the secure use of cloud services, IT security managers should enable secure remote work thanks to dedicated tools. “Remote working leads to the dissolving of the corporate perimeter and a necessity to monitor many more devices,” explains Damir Shaykhelislamov, Advanced Threat Protection Solutions Group Manager at Kaspersky. “It will also require a wider adoption of VPN/privileged access management/multifactor authentication systems, the implementation of stricter monitoring, and the updating of existing contingency and emergency plans.”
As cloud adoption continues to grow, IT security managers will need to align themselves with this cloud paradigm and develop skills for cloud management and protection. In particular, there will be more demand for embedding security practices into development operations – DevSecOps. According to Deloitte, DevSecOps is ‘a transformational shift which incorporates secure culture, practices, and tools to drive visibility, collaboration, and agility of security into each phase of the DevOps pipeline’. IT security managers should be ready to embrace these practices to make DevOps more secure, as this is often a shadow area in terms of IT asset visibility and cyberprotection.
Key takeaways:
- Most companies have non-corporate approved software and cloud services in use, so better visibility over cloud access is necessary
- Specific remote workforce protection tools must have key features, such as VPN, access management and monitoring
- IT security managers will need to develop skills for cloud management and protection including DevOps
A shift in strategy
The pandemic hit at a time when organizations were already under pressure from an unprecedented level of cyberthreats. As nations went into lockdown, Kaspersky investigated how employees were adjusting to life in home offices, what new threats they face and their attitudes to cybersecurity when working on both corporate and personal devices. That research and the findings explored in the sections above demonstrate how corporate life is changing and, with shadow IT on the rise and an increase in the number of remote networks that need protection, why IT security has never faced such a swift need to adapt.
There was also a subtle, but definite, shift in strategy from cyberattackers. As those staff that have always been the soft underbelly of an organization’s cybersecurity defenses left the safety of their offices, they become more vulnerable than ever before.
“The home office has become part of the organization. These home computers will become one of the prime targets for attackers in 2021. Those employees who have access to valuable information will need increased protection. It is also important to provide them with an IT security awareness program,” warns Levtsov.
Team members with a level of responsibility for IT security across a business, from CEOs and CISOs to IT managers, all have their own set of challenges. These can be overcome by taking proactive actions to ensure an organization remains protected. These include gaining a full understanding of how specific threats are being carried out and where they are coming from, along with equipping remote workers with the right security solutions and policies to keep their home office networks safe.
Whilst there is never a good time for a global pandemic, it did unfortunately come at a time of a real talent shortage in the industry. However, while different roles in organizations face challenges, new technology is constantly being developed and current solutions are evolving in order to give both businesses and customers more opportunities. Along with endeavoring to improve cyberprotection across critical aspects of corporate IT, it remains very important to consider how cybersecurity can be implemented in any innovation at the start of its development and implementation.
Alexander Moiseev, Chief Business Officer at Kaspersky examines the important pillars that will support cybersecurity strategies in 2021: “We have seen two important changes in what customers expect from corporate cybersecurity offerings. Firstly, the quality of protection is no longer up for discussion: it used to be a differentiator for cybersecurity vendors, now it’s a ‘must have’. The technologies have become so advanced that administrating them effectively has become organizations’ biggest challenge and they are now looking more at manageability and user experience when choosing the right protection for their business. Another major trend is that deep integration between various components of corporate security, ideally from a single vendor, now plays a bigger role. For instance, there was a long-held belief in the industry that various specialized solutions from various vendors can help create the best combination for protection. Now organizations are looking for a more unified approach with maximum integration between different security technologies.”
To find out more about the financial impact of cybersecurity and data breaches in modern business, along with Kaspersky’s other IT Security Economics reports, follow #securityeconomics on social media.