Videocalls became much more widespread after the COVID-19 pandemic began, and they continue to be a popular alternative to face-to-face meetings. Both platforms and users soon got over the teething problems, and learned to take basic security measures when hosting videoconferences. That said, many online participants still feel uncomfortable knowing that they might be recorded and eavesdropped on all the time. Zoom Video Communications, Inc. recently had to offer explanations regarding its new privacy policy, which states that all Zoom videoconferencing users give the company the right to use any of their conference data (voice recordings, video, transcriptions) for AI training. Microsoft Teams users in many organizations are well aware that turning on recording means activating transcription as well, and that AI will even send premium subscribers a recap. For those out there who discuss secrets on videocalls (for instance in the telemedicine industry), or simply have little love for Big Tech Brother, there are less known but far more private conferencing tools available.
What can we protect ourselves against?
Let’s make one thing clear: following the tips below isn’t going to protect you from targeted espionage, a participant secretly recording a call, pranks, or uninvited guests joining by using leaked links. We already provided some videoconferencing security tips that can help mitigate those risks. Protecting every participant’s computer and smartphone with comprehensive cybersecurity — such as Kaspersky Premium — is equally important.
Here, we focus on other kinds of threats such as data leaks from the videoconferencing platform, misuse of call data by the platform, and the harvesting of biometric information or conference content. There are two possible engineering solutions to these: (i) hosting the conference entirely on participant computers and servers, or (ii) encrypting it, so that even the host servers have no access to the meeting content. The latter option is known as end-to-end encryption, or E2EE.
Signal: a basic tool for smaller group calls
We have repeatedly described Signal as one of the most secure private instant messaging apps around, but Signal calls are protected with E2EE as well. To host a call, you have to set up a chat group, add everyone you want to call, and tap the videocall button. Group videocalls are limited to 40 participants. Admittedly, you’re not getting any business conveniences such as call recording, screen sharing, or corporate contact-list invitations. Besides, you’ll need to set up a separate group for each meeting, which works well for regular calls with the same people, but not so much if the participants change every time.
WhatsApp and Facetime: just as easy — but not without their issues
Both these apps are user-friendly and popular, and both support E2EE for videocalls. They share all the shortcomings of Signal, adding a couple of their own: WhatsApp is owned by Meta, which is a privacy red flag for many, while Facetime calls are only available to Apple users.
Jitsi Meet: self-hosted private videoconferencing
The Jitsi platform is a good choice for large-scale, fully featured, but still private meetings. It can be used for hosting meetings with: dozens to hundreds of participants, screen sharing, chatting and polling, co-editing notes, and more. Jitsi Meet supports E2EE, and the conference itself is created at the moment the first participant joins and self-destructs when the last one disconnects. No chats, polls or any other conference content is logged. Finally, Jitsi Meet is an open-source app.
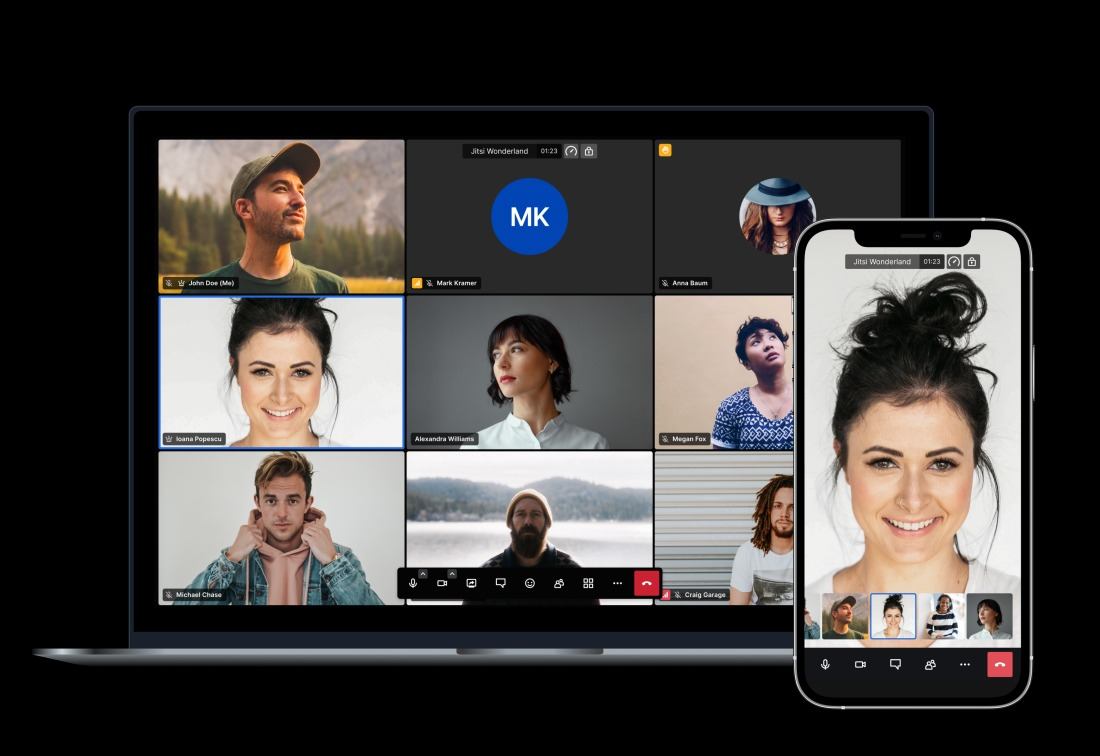
Jitsi Meet is a user-friendly, cross-platform videoconferencing tool with collaboration options. It can be self-hosted or used for free on the developer’s website
Though the public version can be used for free on the Jitsi Meet website, the developers strongly recommend that organizations deploy a Jitsi server of their own. Paid hosting by Jitsi and major hosting providers is available for those who’d rather avoid spinning up a server.
Matrix and Element: every type of communication — fully encrypted
The Matrix open protocol for encrypted real-time communication and the applications it powers — such as Element — are a fairly powerful system that supports one-on-one chats, private groups and large public discussion channels. The Matrix look-and-feel resembles Discord, Slack and their forerunner, IRC, more than anything else.
Connecting to a Matrix public server is a lot like getting a new email address: you select a user name, register it with one of the available servers, and receive a matrix address formatted as @user:server.name. That allows you to talk freely to other users including those registered with different servers.
Even a public server makes it easy to set up an invitation-only private space with topic-based chats and videocalls.
The settings in Element are slightly more complex, but you get more personalization options: chat visibility, permission levels, and so on. Matrix/Element makes sense if you’re after team communications in various formats, such as chats or calls, and on various topics rather than just a couple of odd calls. If you’re simply looking to host a call from time to time, Jitsi works better — the call feature in Element even uses Jitsi code.
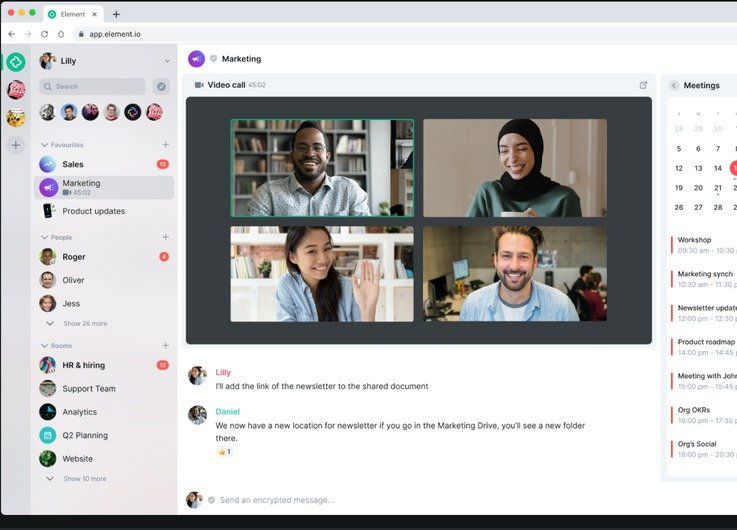
Element is a fully featured environment for private conversations, with video chats just one of the available options
Corporations are advised to use the Element enterprise edition, which offers advanced management tools and full support.
Zoom: encryption for the insistent
Few know that Zoom, the dominant videoconferencing service, has an E2EE option too. Until recently, this feature required a Large Meetings License, which lets you host 500 or 1000 participants for $600–$1080 a year. But now even free-plan users can activate it.
That said, you won’t find any such option in the Zoom client. To enable E2EE, you need to sign in on the Zoom website, go to your account’s control panel, and navigate to the Settings → Security section. Here, you can toggle the Allow use of end-to-end encryption setting. Enabling this setting requires you to provide your phone number and link it to your Zoom account. A confirmation code will be sent to it, and this number will be visible to your Zoom contacts.
Once you’ve enabled E2EE, an option to select the default encryption type – Enhanced or End-to-End – will appear below. Why Zoom calls its fairly basic encryption “enhanced” is anyone’s guess — from a security point of view, it’s clearly worse than end-to-end. If End-to-End is what you select, it will be used by default in conferences you host, but not necessarily in those you join as an invited participant — then the encryption method is in the hands of the conference host. To see what encryption is being used during the current conference, click the padlock icon in the upper left corner of the window.
According to the Zoom website, activating E2EE for a meeting disables most familiar features, such as cloud recording, dial-in, polling and others.
 privacy
privacy



 Tips
Tips