Update: The app described in this post is discontinued. To protect your Android smartphone or tablet use .
Android OS has settled down for good on the top of the two hit parades. Firstly, it is a mobile OS rating. Secondly, it’s the rating of the mobile platforms which are being infected most often. According to Kaspersky Lab more than 99% of mobile malware are Android-oriented. Applications on Google play are being regularly checked to safeguard users, moreover Google has implemented a number of protective measures in the Android OS itself. For example, during the application installation there is verification which can guarantee the origin of a software and the confidence that files were not changed by strangers. Unfortunately, these measures are not perfect and malware has had a good opportunity to get into the smartphone by a back door for a long time.
The backdoor
The last year specialists found several flaws in the Android protection mechanisms. Because of these flaws, a malicious application can penetrate the smartphone by disguising itself as a popular and trusted service, or by “piggybacking” the legitimate application, i.e. adding itself into the installation package. The vulnerabilities called Master Key and FakeID are presented in most of the modern Android smartphones. They are a little bit less famous than renowned Heartbleed(Android smartphones are also subjected to it partly), but it is very important to remove them. The difficulty is that although Google released the necessary fixes long time ago, they should be implemented by either particular smartphone and tablet computer vendor or by a mobile operator that distributes them. And then the owner of this particular device should download and install this update. This often happens with a significant delay and often doesn’t happen at all. So the amount of vulnerable devices numbers millions.
To seal the hole
To get rid of the vulnerability without any assistance is not easy, but you can minimize associated risks for your devices. Here are the steps to do that:
- Check if there are such vulnerabilities as FakeID, Master Key or Heartbleed on your smartphone or a tablet. You can use the free scanner from Kaspersky Lab which is available on Google Play. Besides the presence of the vulnerability, it also examines if there are applications installed which use this vulnerability.
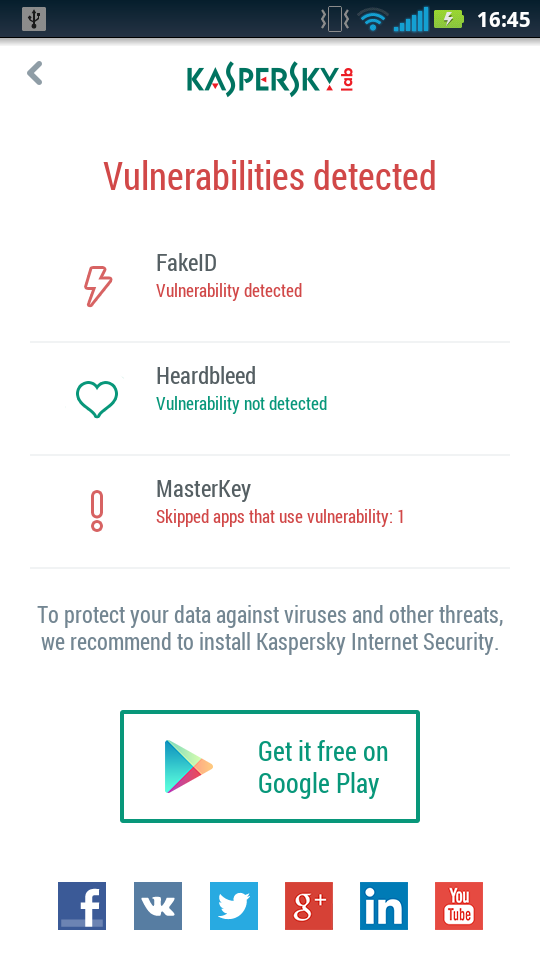
- If your device is vulnerable, check whether firmware (phone software) updates are available. Most Android vendors have a special “check for update” section in the settings, but in some cases you have to visit the official producer’s web-site. If updates are available, install them according to the manual and check your device as in p.1 again.
FakeID vulnerability allows a malicious app to sneak into your Android smartphone – learn how to fix it.
Tweet - If the vulnerability hasn’t been addressed yet, you could fix the breach by yourself, but it takes many complicated and somewhat unreliable procedures, which wouldn’t be recommended to the general public. (If you are brave enough and literate in this area you could read more on the xda-developers website.)
- Unpatched vulnerability isn’t a cause to throw the smartphone away, but you have to be vigilant to avoid loss of money and data:
- Use only large official applications stores (think Google Play)
- Download only the apps with high popularity and ratings
- Control the permissions of the application
- Use Reliable Android Security software.
Update: The app described in this post is discontinued. To protect your Android smartphone or tablet use .
 android
android

 Tips
Tips