Complex attacks. Nonmalware attacks. Fileless attacks and malware plants by physical access. Zero-day exploits leveraging new tools and increasingly agile cybercrime techniques. In today’s volatile threat landscape, preventive technologies alone can’t protect businesses against advanced threats. Add to this the fact that cybercriminals can mount an effective targeted attack at minimal cost, and it’s no surprise that the number of successful attacks continues to rise globally.
According to the findings of analytical agency B2B International, commissioned by Kaspersky Lab and published in Kaspersky Lab’s New Threats, New Mindset: Being Risk Ready in a World of Complex Attacks report, targeted attacks became one of the fastest growing threats in 2017, increasing in overall prevalence over 2016 by 6% for SMBs and by 11% for enterprises.
More than a quarter of businesses (27%) admitted that they had experienced targeted attacks on their infrastructure, up from 21% the same time the previous year, and 33% of businesses felt that they were being specifically targeted by cybercriminals. Of the companies surveyed, 57% said they expected that a security breach would happen to them at some point, and 42% were still unsure about the most effective strategy to respond to these threats.
A traditional approach is no longer good enough
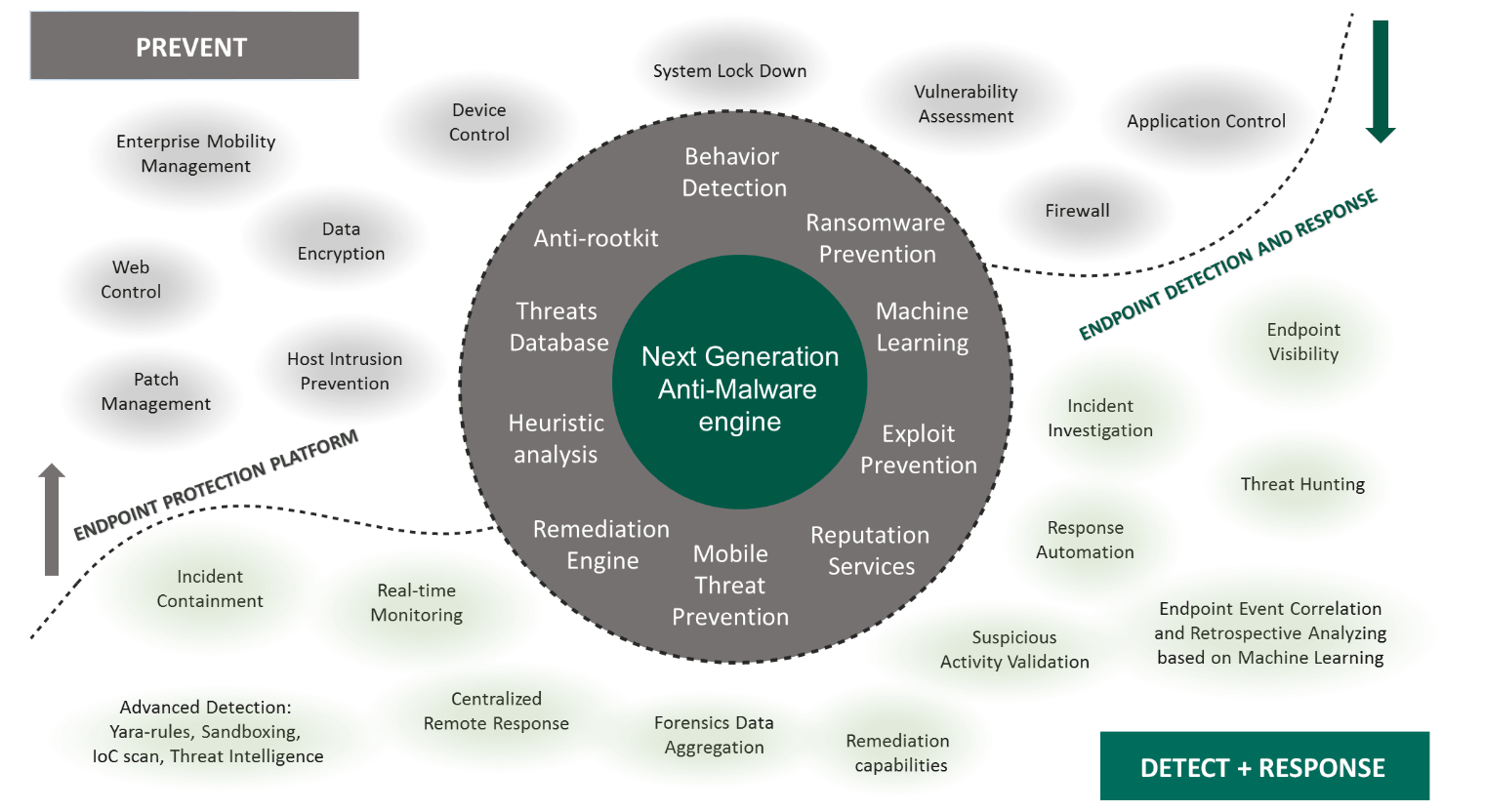
Endpoint protection platforms (EPPs), which typically exist in an organization’s infrastructure, control known threats such as traditional malware. They can also handle unknown viruses, which might use, for example, a new form of known malware directed at endpoints. These systems are excellent at protecting against known, and some unknown, threats. However, cybercrime techniques have evolved significantly in recent years, and cybercriminals have become more aggressive in their attack processes. The combination of common threats, unique malicious patterns, and activities based on complex infiltration techniques from cybercriminals makes advanced threats and targeted attacks extremely dangerous for any organization relying solely on a conventional approach to cybersecurity.
Businesses are at risk of theft or attack from every angle — to data and finances, intellectual property, sensitive commercial data, and specific personal or other sensitive data, against business processes and competitive advantage, and so on.
Incidents related to advanced threats have a significant impact on business: the cost of responding and process recovery, having to invest in new systems or processes, the effect on availability, damage to reputation and brand, financial loss, and so forth. Organizations need to consider not only the growing number of widespread malicious programs, but also the increase in complex advanced threats and targeted attacks.
That means they need to extend their protection beyond network, mail, and Web traffic to endpoints, including workstations, laptops, servers, and smartphones. These endpoints are commonly used entry points into an organization’s infrastructure during targeted attacks, making endpoint visibility critical in today’s threat landscape.
According to the SANS 2017 Threat Landscape Survey, 74% of respondents said that clicking a link or opening an e-mail attachment was the top way for threats to enter the organization, and 48% named Web drive-by or download. A full 81% of companies surveyed considered endpoint security tools the most helpful means of threat detection.
The need for specialized tools for endpoint detection and response
Clearly, just blocking the easy threats on endpoints is not sufficient; today, companies need tools that help them to detect and respond to the latest, most complex threats.
Why?
First, because of the specifics of the targeted attacks that cybercriminals use:
- Security systems bypass — attackers conduct a thorough investigation into existing infrastructure, including the endpoint security system being used;
- Zero-day vulnerabilities, compromised accounts;
- Malicious software or specially created, unique software;
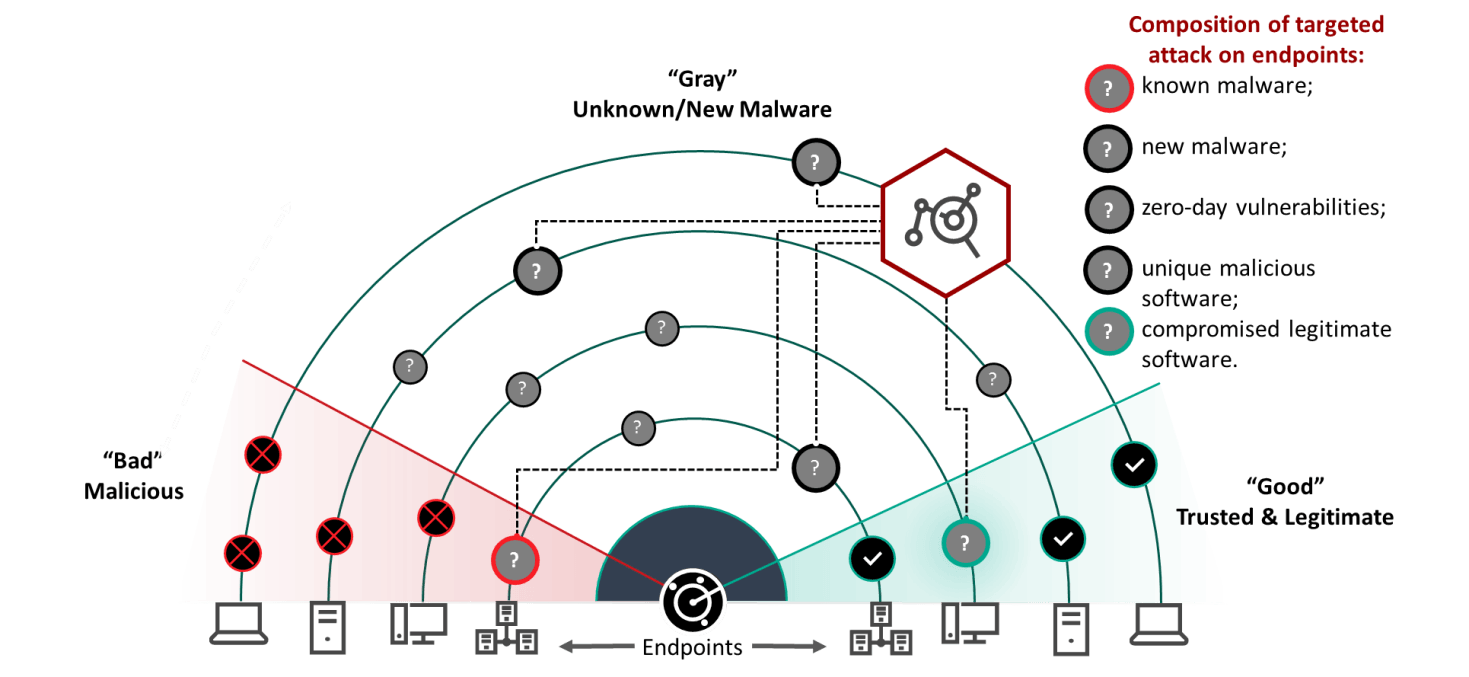
- Compromised objects that appear normal and therefore remain trusted;
- A multivector approach focusing on penetrating as many endpoints as possible: desktop computers, laptops, servers, etc.;
- Social engineering and data obtained from insiders.
Second, because of the technological limitations of traditional endpoint protection products, which:
- Aim to detect and block common (uncomplicated) threats, already known vulnerabilities or unknown threats typically built on previously known methods;
- Focus on the visibility of each single endpoint and aren’t designed to visualize and monitor in real time all endpoints simultaneously from a single centralized interface;
- Do not provide IT administrators with the necessary threat information to provide insight into the threat context, and lack full visibility into individual endpoint activity, into processes, timelines, and potential relationships with every endpoint in the company;
- Offer no built-in mapping or correlation of several verdicts from different detection mechanisms into a single, unified incident;
- Do not support functionality for detecting abnormal activity, deviations in normal activities, and so on, or analyze the work of legitimate programs;
- Cannot retrospectively analyze lateral malware movement;
- Have limited capabilities for detection of fileless attacks, memory injections, or malwareless threats.
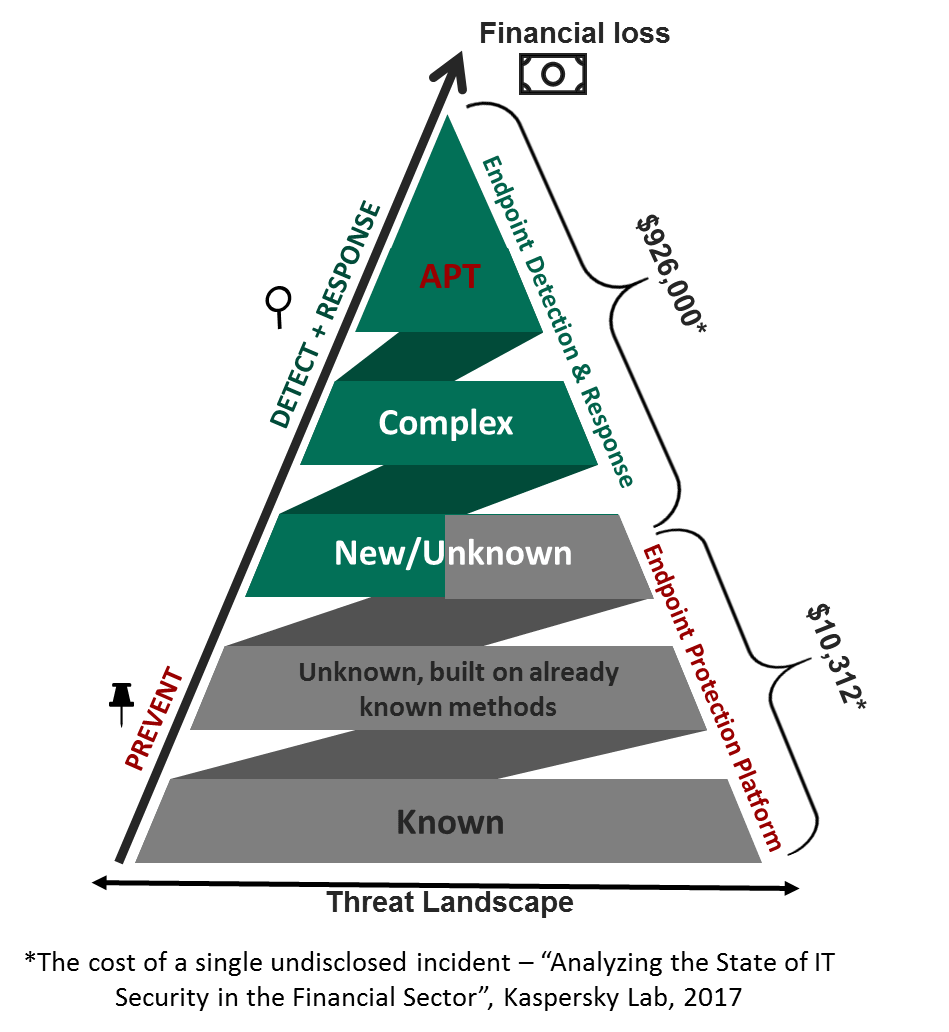
As we can see from the above, endpoint protection technologies work well with simple threats, which account for more than 90% of all threats. The cost of incidents associated with these threats (about $10,000) is negligible compared with the cost of incidents associated with an advanced persistent threat (APT) attack ($926,000). The earlier a purposeful composite attack is detected, the less the financial loss. In the face of complex threats, the quality and effectiveness of detection and response are of paramount importance. To protect against targeted attacks and APTs, organizations need to think about the use of specialized solutions to counteract targeted attacks and APT-level threats on endpoints.
The average cost of incidents, and the functionality gaps in traditional EPP solutions not designed to counter complex threats, clearly demonstrate the need for additional investment in specialized products for advanced threat detection and response. EPP products need greater flexibility and must include endpoint detection and response (EDR) functionalities or have the ability to integrate with standalone full-function EDR solutions, depending on a company’s size and requirements.
True end-to-end visibility and proactive detection
EDR is a cybersecurity technology that addresses the need for real-time monitoring, focusing heavily on security analytics and incident response on corporate endpoints. It delivers true end-to-end visibility into the activity of every endpoint in the corporate infrastructure, managed from a single console, together with valuable security intelligence for use by an IT security expert in further investigation and response.
Most endpoint protection platforms rely on stored patterns and signature files to stop known threats. More recent next-generation endpoint protection platforms, which use machine learning and deep-level detection mechanisms for threat hunting and discovery, also focus on delivering antimalware protection.
The main aim of EDR is the proactive detection of new or unknown threats, previously unidentified infections penetrating the organization directly through endpoints and servers. This is achieved by analyzing events in the gray zone, home of those objects or processes included in neither the “trusted” nor the “definitely malicious” zone.
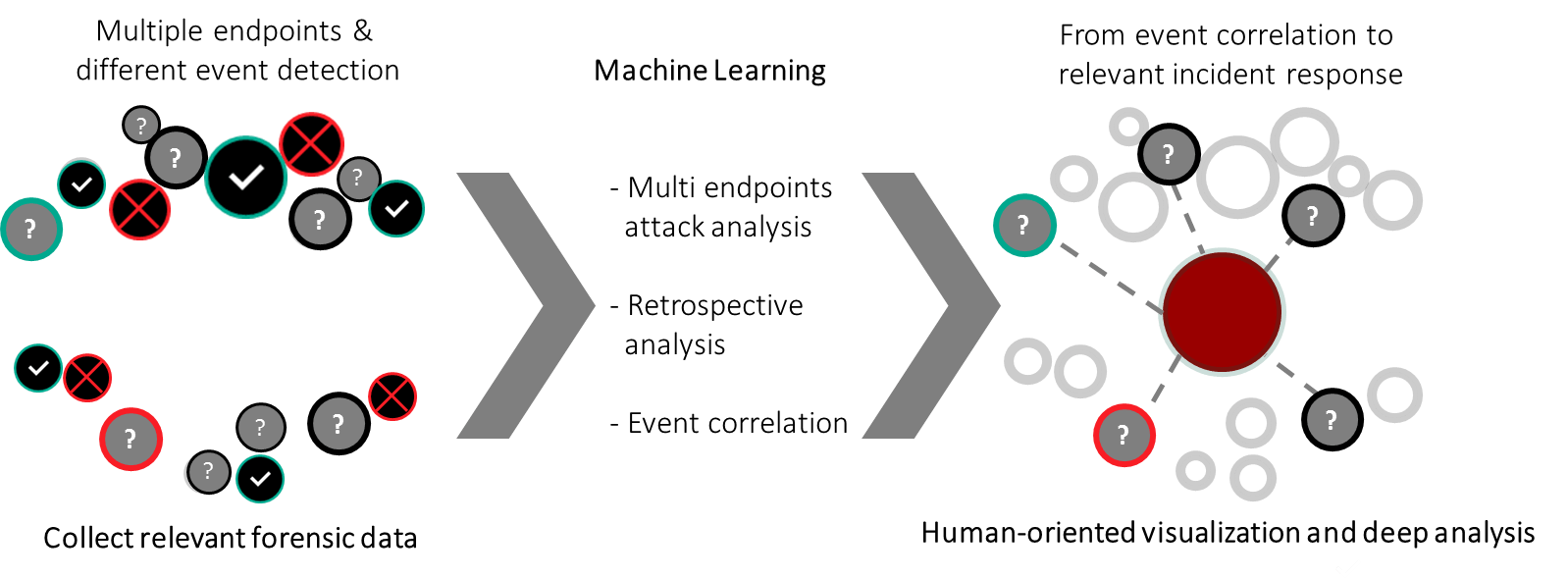
Without EDR functionality, classical EPP doesn’t technically support deep endpoint visibility, retrospective and multiendpoint attack analysis and event correlation, or the ability to select from multiple event detections relevant to complex attacks to determine the appropriate response. Not all EPP solutions on the market support access to the threat intelligence required to understand a threat’s main tactics, procedures, and techniques.
All of these functions are necessary to defend against modern threats and targeted attacks. Companies have to understand that endpoint security can no longer be covered by a single EPP solution. EDR has a far better chance of detecting unknown malware strains in zero-day and APT-level attacks because it uses advanced detection technologies such as YARA rules, sandboxing, scanning of IoCs (indicators of compromise), suspicious activity discovery and validation, retrospective analysis with event correlation based on dynamic machine learning, incident investigation and containment, response automation, remediation capabilities, and more.
For reliable, effective protection from advanced threats, the EPP and EDR collaborate — the EPP handling known threats and EDR dealing with more complex unknown threats. Powerful EDR platforms can help analysts to investigate and improve their defenses, rather than just reacting to damage already caused by an advanced threat that traditional endpoint protection solutions would miss.
Additionally, an EPP provides not just protection, but also application, device, and Web controls; vulnerability assessment and patch management; URL filtering; data encryption; firewall; and more.
An integrated approach to counteracting advanced threats
Each of the systems described above complements something missing (or only partially present) in another system, which means the solutions need to integrate and interact with each other. EPP and EDR have the common goal of countering threats, but they also have significant differences. They take different approaches to protection against different types of threats and use different tools.
According to Gartner’s “Strategic Planning Assumption 2017 for Endpoint Detection and Response Solutions” report, by 2021, 80% of large enterprises, 25% of midsize organizations and 10% of small businesses will have invested in EDR capabilities.
The presence of preventive technologies such as EPP for the detection and automatic blocking of widespread threats and obviously malicious objects helps eliminate the need to analyze the large number of minor incidents that are irrelevant to complex attacks, increasing the efficiency of specialized EDR platforms aimed at detecting threats at an APT level. EDR, in turn, after detecting complex threats, can send verdicts to the endpoint protection platform. In this way, the two cooperate and provide a truly integrated approach to counteracting advanced threats.
Extracting maximum value from EDR
There’s something else we need to consider. Most organizations already need EDR functionality, but we also have to face the fact that a large percentage of these organizations don’t have the skills and resources for a full-blown EDR deployment or its proper use.
This is about the transition from simple EPP tracking by the IT department to the need to involve appropriate IT security team resources when using EDR. As we’ve seen, EDR technology offers much more than just standard protection. To maximize EDR’s benefits, businesses need security engineers and threat analysts with sufficient knowledge and experience. These professionals need to understand how to extract value from the EDR platform and organize an efficient process of incident response.
Depending on each organization’s maturity and experience in the field of security, and the availability of necessary resources, some businesses will find it most effective to use their own expertise for endpoint security but to call on outsourced resources for more complex aspects. Meanwhile, they can build up in-house expertise with skills training, through access to a threat intelligence portal and APT intelligence reporting, and using threat data feeds. Or — particularly attractive for overwhelmed or understaffed security departments — they can adopt third-party professional services from the outset, including:
- Security assessment services,
- Threat hunting,
- Incident response,
- Digital forensics,
- Malware analysis and reverse-engineering,
- 24/7 premium support.
The proposed solution from Kaspersky Lab
Kaspersky Lab’s approach to endpoint protection includes the following components: Kaspersky Endpoint Security, Kaspersky Endpoint Detection and Response, and Kaspersky Cybersecurity Services. For organizations unable, for reasons of regulatory compliance, to release or transfer any corporate data outside their environment, or that require complete infrastructure isolation, Kaspersky Private Security Network provides most of the benefits of global cloud-based threat intelligence as provided by Kaspersky Security Network (KSN,) without any data ever leaving the controlled perimeter.
These components adapt to the specific nature of each organization and its ongoing processes, delivering:
- A unique combination of renowned, leading preventive technologies to block the most common attacks;
- A range of advanced mechanisms and techniques to detect and rapidly respond to unique new and advanced threats;
- The ability to predict future threats and build proactive protection against them by using professional services;
- The ability to benefit from using global cloud-based threat intelligence without releasing any data from their controlled perimeter.
Kaspersky Endpoint Security is a multilayered endpoint protection platform based on next-gen cybersecurity technologies powered by HuMachine Intelligence, delivering flexible, automated defenses against a wide range of threats including ransomware, malware, botnets, and other advanced known and partly unknown threats.
Kaspersky Endpoint Detection and Response uses the same agent as Kaspersky Endpoint Security, providing a multifaceted approach to revealing and recognizing complex threats by using advanced technologies (including machine learning, sandboxing, IoC scanning, and threat intelligence). It responds to prevent future malicious actions through the timely discovery of advanced threats, sending the verdicts to Kaspersky Endpoint Security for follow-up blocking.
Kaspersky Cybersecurity Services offers prompt and professional assistance during an ongoing incident — and afterwards — helping reduce the risk of compromised data and minimize financial and reputational damage. The Kaspersky Cybersecurity Services portfolio includes our broad security training curriculum, up-to-the-minute threat intelligence, rapid incident response, proactive security assessments, fully outsourced threat hunting services, and 24/7 premium support.
Dealing with advanced threats requires advanced tools
To withstand advanced threats and targeted attacks, businesses need automated tools and services designed to complement each other and help security teams and existing corporate security operations centers (SOCs) prevent most attacks, detect unique new threats rapidly, handle live attacks, respond to attacks in a timely manner, and predict future threats.
With the right combination of technologies and services in place, organizations can establish and follow a comprehensive adaptive security strategy and be ready to deal with the ever-changing nature of cyberthreats, improving their protection and mitigating the risk of future attacks.
 EDR
EDR

 Tips
Tips