Human beings are a curious lot. It’s in their nature to try and get to the ‘whys’ and ‘hows’ of everything and anything. And this applies in cybersecurity too; in fact – doubly so: getting to the ‘whys’ and ‘hows’ of cyberthreats is the very basis upon which cybersecurity is built; thus, upon which KL is built.
Getting to the ‘whys’ and ‘hows’ for us means meticulously taking apart every cyberattack into its respective constituent pieces, analyzing it all and, if necessary, developing specific protection against it. And it’s always better to do this proactively, based on the mistakes of others, and not waiting until what we protect is attacked.
To solve this challenging task we’ve a slew of intelligence services for enterprises. In this collection of cyber-precision-tools there’s staff training, security intelligence services to come up with detailed information about discovered attacks, expert penetration-testing services, app-audits, incident investigations, and more.
Well now the ‘and more’ includes our new service – KTL (Kaspersky Threat Lookup) – the smart microscope for dissecting suspicious objects and uncovering the sources/tracking histories of cyberattacks, multivariate correlations, and degrees of danger for corporate infrastructure. Quite the X-ray for cyberthreats.

Actually, all our users already has the lite-version of this service. The security rating of a file can also be checked with our home products, but enterprise customers need a deeper, more thorough analysis of threats.
To begin with, KTL can be used to check not only files, but also URLs, IP addresses and domains. It can analyze objects for the hallmarks of targeted attacks, behavioral and statistical specifics, WHOIS/DNS data, file attributes, download chains, and others.
Yep, it’s kinda like a search engine but with the searching being solely for cyberthreats. Dedicated staff need only enter details of a certain suspicious object into it and KTL will return the full low-down on it, including historical, geographical and other aspects, plus connections with other events and objects. All in real-time, 24/7.
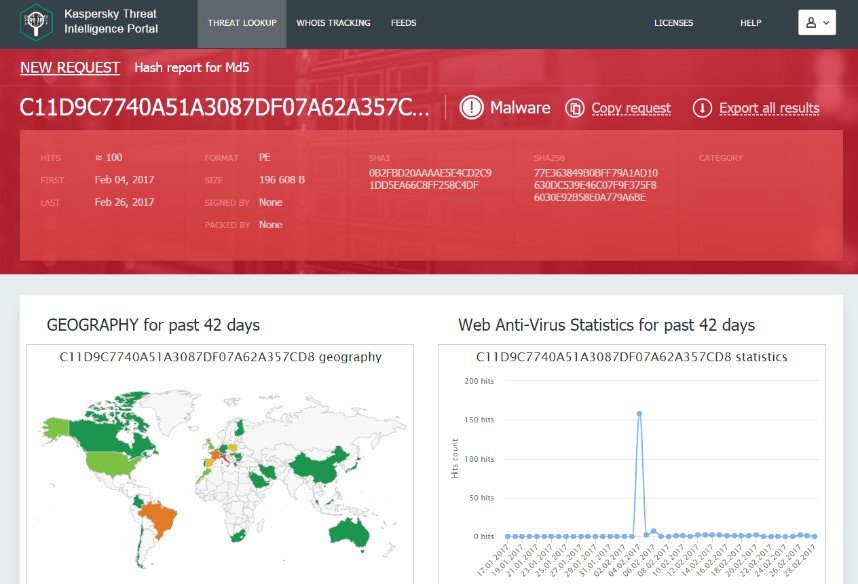
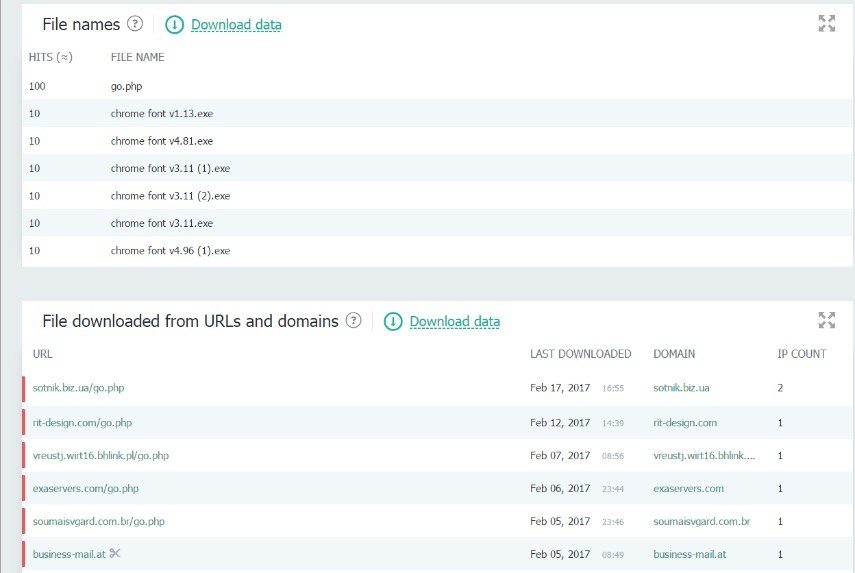
The results, suspicious objects, and other IoC can be exported in machine-readable sharing formats (STIX, OpenIOC, JSON, Yara, Snort, CSV…) for integration with corporate SIEMs.
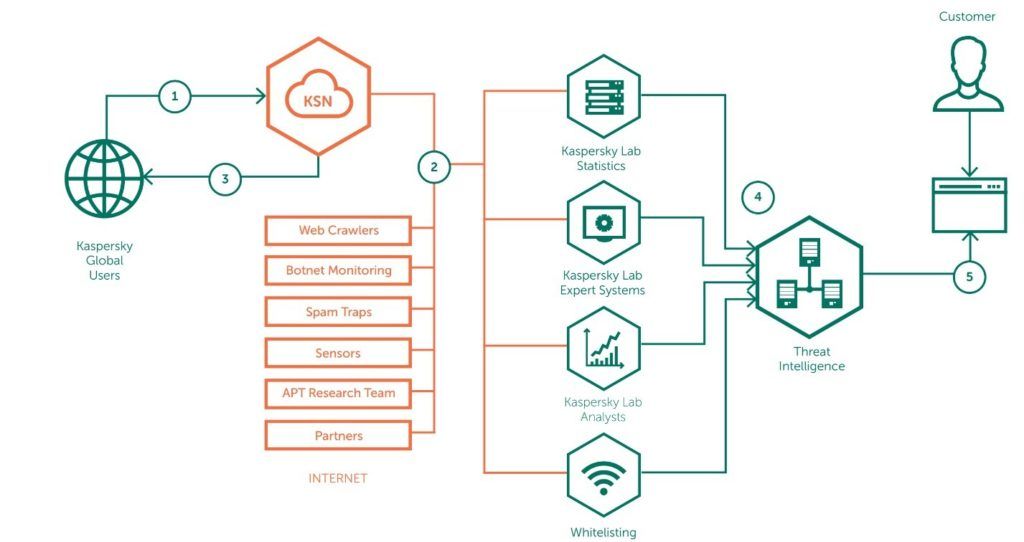
So where does KTL get its data from? There are several sources.
First, there’s our cloud-based KSN, which contains anonymized signals about the epidemiological situation from hundreds of millions of users all around the world. In using it, customers not only look after themselves (participation in KSN automatically increases quality of protection), but also help fulfill an important humanitarian mission: to look after others too, and in doing so reducing the overall cyberthreat level across the Internet.
Second, there’s our technology that analyzes network activity, including spam traps, botnet monitoring, web crawlers, various network sensors, and smart robots powered by machine learning. And of course there are the results of investigations of complex targeted attacks by the GReAT cyber-ninjas.
Third, there are our partner software developers. Incidentally, the role of these will grow over time, to eventually become predominant. Yep, we have big plans for the future, but I’ll not go into details here just yet.
For now – a bit on our near-future plans…
We’re currently working on adding to KTL functions of analysis of suspicious objects in a secure environment – a cloud sandbox.
For example, a file is placed in the sandbox and run on a special virtual machine (with a patented logging system). The virtual machines are fully isolated from each other and from internal networks, and have limited external connectivity too. The virtual machines are identical to physical computers so that the objects feel safe to do as they would in the real world. The machines then note down all the actions performed by an run object (much like our KATA protection from targeted attacks). All results are compiled in a detailed report; here is shown how the file would have acted if it was in a real-world situation, and a review of the full scope of the threat behavior is given too.
Also in the pipeline are Next Gen tools for working with metadata files and URLs. In upcoming versions there’ll be added the ability to extract different metadata and make customized searches in this metadata. Thus, it will be possible to conduct deep investigations of malware based on similarities across various parameters so as to understand the overall picture of sophisticated attacks. For example, with the help of this tool it will be possible to ask it to: ‘find me files that when launched do this or that’, or ‘find me all files with such a name’, or ‘find me files that are detected under this or that verdict of an AV engine’, or ‘find me files whose code contains this or that line’.
So, as you can see, we’ve got a multi-function cyber-X-ray in development, but some of its functionality can already be used right now (so you could recommend new useful features:).
More details about KTL – here.
 True Cybersecurity
True Cybersecurity

 Tips
Tips