
DDoS On The Move
According to a study by Kaspersky Lab and B2B International, only 37% of the organizations surveyed said they currently have measures in place to protect against DDoS-attacks.
1278 articles

According to a study by Kaspersky Lab and B2B International, only 37% of the organizations surveyed said they currently have measures in place to protect against DDoS-attacks.

Kaspersky Lab has just publicized the discovery of a new cyber-espionage campaign. Unlike previous thresats, it’s targeting smaller entities – namely SMBs. That’s where it gets interesting.
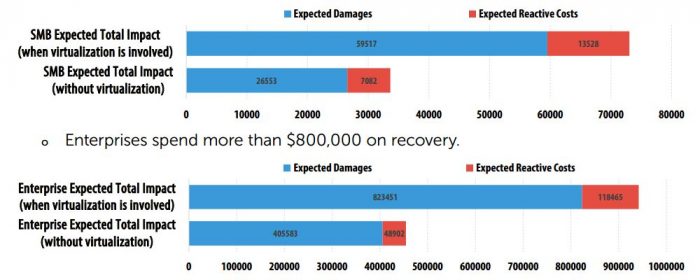
Technology dependence cannot be beaten, but the technologies can be laid out properly. With good system architecture and a proper security policy, the number of bottlenecks is brought to an absolute minimum.

For many people security measures are a “secondary accessory,” and not something that should be cared for first and foremost. This is a common, but innately flawed mode of thinking.

Simda was a rather mysterious botnet that had been used for dissemination of third-party potentially unwanted and malicious software. It has a built-in tools to detect and evade emulation, virtual machines and security tools, effectively allowing the bot to stay out of grid – apparently for years.

Encrypting ransomware is a relatively new, but extremely pesky, threat that is evolving at a rapid pace, becoming a more advanced problem for end-users and businesses alike. What can be done about it?

Kaspersky Lab experts have investigated one of the most active APTs (Advanced Persistent Threats) in Asia, operating specifically around the South China Sea area. It was named “Naikon” after the “nokian” User-Agent substring within an attack components’ code.

Kaspersky Lab hosted the Kaspersky Cybersecurity Summit 2015 in Singapore this April, dedicated to enterprise IT Security challenges – and solutions. The motto for the event was: “Business under attack:

Personal smartphones and tablets are used to store working data, both personal and corporate passwords, and other sensitive information. So, it is troubling that mobile protection often lags behind.

This post isn’t about smearing the good, evolving system that is Apple’s Mac OS X. The goal was to bring perception and reality together: just like the other operating systems, Mac OS X has its fair share of bugs, and while the historically smaller Mac user base has resulted in less cyber criminal targeting, it doesn’t make Mac OS X impervious. Macs’ user base has been growing steadily over the last few years, and criminal interest is following the same pattern.

Mid-April in Singapore was pretty hot not only because of tropical climate, but also because of INTERPOL World – a huge conference/exhibition organized by INTERPOL to give security product vendors

With an increasing amount of people using mobile devices for work, security of the data stored therein has become a hot topic. And since people also use mobile devices to access their finances, that makes them a prime target for cybercriminals. Android is the most popular mobile OS in the world right now, and the most targeted. How are users attacked and what is the current security status of Android?

Yet another Duke APT is hitting high-profile targets, including the US government office. This time it’s CozyDuke (also known as CozyBear, CozyCar or “Office Monkeys”, in honour of the video it employs as a decoy).

The necessity of a product that is positioned in-between the enterprise-level suites and home-users solutions became apparent only a few years ago.

The global workforce is increasingly going mobile: 37% currently, up to 50% by 2020. There are more actively used mobile devices in any more or less developed country than there are adult citizens, so clearly “mobility” is something related to us all.

Kaspersky Lab experts have discovered a new APT campaign that targets government institutions, mainly in the APAC region. It was named “Hellsing” after the string containing the project directory name found within the attack components’ code.

Security is a tough matter for small businesses for multiple reasons; startups and small entities tend to save on their IT wherever possible, and that’s where security failures are common.

The cybersecurity has become the everyone’s business, and it raises the demand for continuous update of information for everybody, both high-level security professionals and common corporate users. And especially for the latter, since it is them criminals attack most of the time.

A peculiar botnet codenamed Simda has been taken down as a result of a joint operation between a number of law enforcement agencies and commercial organizations.

Every security vendor has a portfolio of advanced “anti-malware technologies” that make its products good and even better than all the rest.

Over the last few years we have witnessed a number of high-profile, large scale security breaches with quite dramatic consequences, such as massive leaks of personally identifiable data.