In our experience at Kaspersky Lab, ensuring True Cybersecurity for enterprise IT infrastructure requires multilayered solutions. By multiple layers we mean not only using overlapping protective technologies or covering different levels of IT network. We also imply that utilized range of solutions should possess qualities allowing corporate security to dynamically adapt in line with the ever-changing threat landscape.
Why do we think this approach makes the most sense? Whatever you might think of it, we are participating in an never-ending arms race. By continuously improving protection technologies, we try to make them more effective than the tools and techniques used for cybercriminal activity. But what matters is that we cannot settle for purely reactive measures. To efficiently deflect various attacks, we need flexibility to optimize protection not reactively, but proactively, before new threats are out.
Moreover, we think that a single super-technology that guarantees protection from all threats is a utopian dream. Even a new method demonstrating proven impressive results shortly after its conception will be effective only until cybercriminals strike back.
Effective protection framework is cyclical
We think the most viable security architecture is the one described by Gartner. It is based on a cycle of activities and divided into four key areas: Prevent, Detect, Respond, and Predict. Essentially, it assumes intrusion detection and prevention systems should function in concert with threat analytics. Ideally, this strategy helps to create a cybersecurity system that continuously adapts and responds to the emerging challenges of the digital world.
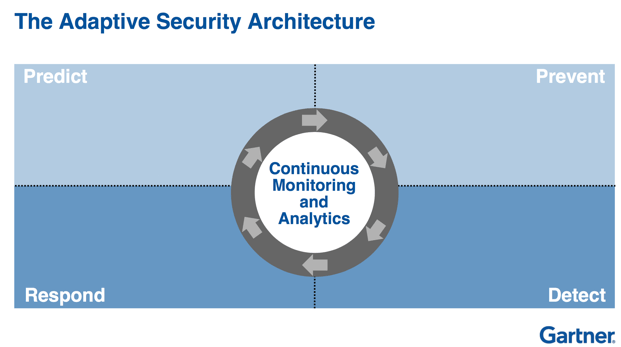
Here is how this adaptive security model could be deployed.
Prevent
The “Prevent” segment is, to put it simply, technologies which use iron-clad reasoning to define whether an object is safe or malicious and block in the latter case. This segment includes such solutions as firewalls, signature-based engines, and proactive technologies using machine learning. They are all, in essence, included in all of our products for Next Gen endpoint protection: Kaspersky Security for Business, Kaspersky Security for Virtualization, and others.
These solutions don’t need to be managed by a security expert. Most frequently, such systems are managed by general-purpose IT administrators who can also take care of things like databases or local networks. They need a security solution to be robust and hassle-free.
Such products block up to 99% of threats, blocking not only well-known (70%) but also previously unknown (29%) malware. But what about the remaining 1% of advanced threats, which are the most tricky and dangerous? Especially with that 1% inflicting heaviest damage on attacked businesses?
Detect
Some objects and events can be classified as inherently malicious, and some could be inherently safe. However, such classification is not always enough. Some of them are in the gray zone — for example, advanced threats such as APTs, which go to great lengths to evade or mislead security systems.
To control the gray zone, we need the “Detect” level. Security solutions belonging to this layer do not block threats themselves. They serve to detect and report suspicious activity. Such solutions should be managed not by IT generalists, but by skilled infosec professionals.
“Detect” technologies include behavioral analytic systems and dynamic code analyzers. An example of such technologies is the recently launched Kaspersky Anti-Targeted Attack Platform. Among its features, it boasts the Targeted Attack Analyzer, which controls network events. It is based on an approach we call HuMachine Intelligence: a seamless fusion of Big Data-based Threat Intelligence, Machine Learning and Human Expertise. It is highly effective because human and machine intelligence work better when they complement each other, rather than work separately and benefit from most relevant globally acquired knowledge of the threat landscape. The Targeted Attack Analyzer detects suspicious activity by analyzing the system’s working patterns and comparing them to ‘normal’ picture . If any activity does not match the usual state of things, the system alerts personnel. The normal model is created with the help of machine-learning processes functioning both on Kaspersky Lab servers and on customer’s premise. Thus, the system knows what is normal and what is not in certain environment.
As an example, let’s look at a medium-size company that works in the sphere of trade. It does not conduct business with, say, Vietnam. None of the employees are Vietnamese. And one day a computer in the enterprise network connects to a .vn Web resource in the dead of night. The Targeted Attack Analyzer knows that no one from within the organization has ever visited Vietnamese websites. Also, according to the Kaspersky Security Network, no one has ever connected to that server. Therefore, the .vn connection is a reason to employ some deep analysis tools. Of course, it could be entirely innocent and coincidental, but it is abnormal, so it makes sense to double-check the incident.
Respond
“Respond” is the next logical step in this framework. In our case, the threat can be neutralized with help of both technologies and services, and by the latter we mean work of analysts who investigate attacks and prepare reports.
Kaspersky Lab offers a wide range of these services, including incident research and malware analysis. In addition, we are working on a toolset to optimize these processes by automating evidence collection, searching for compromised endpoints, employing remote configuration, and more.
In the meantime, further development of Kaspersky Anti Targeted Attack platform involves introduction of Endpoint Detection and Response capabilities, which would not only greatly enrich detection context, but also provide response functionality on the scale of the extensive enterprise network. Also, it provides forensic specialists with extended range of data crucial for subsequent incident investigation.
The collected data also helps us to better understand today’s cyberthreat landscape, thus creating more effective protection solutions. This is what the next level is all about.
Predict
Various data feeds, obtained through both automatic acquisition (data on malicious links and files) and by expert analysts (APT research), are indispensable assets that can be used to predict future attacks and attack vectors and thus improve security posture. This data, constantly fed into Kaspersky Lab internal analytical systems, is thoroughly assessed. The results of the analysis are used to improve security mechanisms, including adjustments to machine learning processes.
To improve our technologies, we also use data obtained during pentesting and application security analysis (see the “Prevent” section above). Having processed all available information, our technologies can automatically block more threats — which brings us back to the ‘Prevent’ level we started our article with.
And there you have it: the never-ending cycle of Adaptive Security Architecture. Ideally, it enables us to stay ahead of cybercriminals, creating and improving security systems according to the current state of the threat landscape and preventing huge losses for businesses.
 HuMachine
HuMachine

 Tips
Tips