June is wrapping up this week; we’ve made it through half of 2015. Over the last year and a half quite a few new APT campaigns have been discovered, but there is a glimpse of a potential landslide in the making with two of them, both reported in 2015.
Let’s look at the map
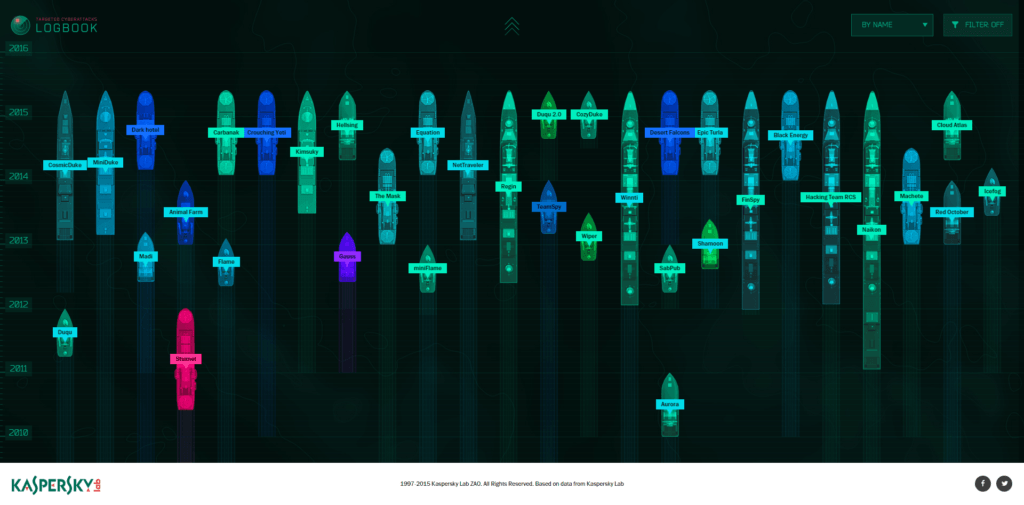
Let’s take a look at a visual tool dedicated to real-time monitoring of APTs – “Targeted Attacks Logbook”.
This is an interactive map of APTs, and currently it looks more densely populated than it was last year. Even though most of the campaigns reported this year were actually discovered in 2014. Judge yourselves:
This is 2014 Logbook from our initial announcement.
This is how it looks today.
The colors of the “ships” are indicative of the number of the APT’s victims. As we see, most of them are within green-cyan range, although Desert Falcons, publicized in the first quarter of 2015, might have snatched up to 5K of the targets.
Aside from Falcons, there are just three other APTs identified in Q1, 2015:
Equation APT – the “mothership”, “Death Star” of APTs, a massive cyberespionage framework, probably as old as 12 years old (according to the latest data, first known sample is dated 2002, but it may be even older).
Carbanak – the first ever criminal APT, but most likely not the last one.
Animal Farm – a french-speaking cyberespionage campaign, also quite old and massive, accounting for up to 5K victims.
A few more have been publicized since the end of Q1 – such as Hellsing APT (that surfaced after its counter-attack on yet another threat actor – Naikon), CozyDuke, SpringDragon and Duqu 2 which happened to be directed right at us, “Kaspersky Lab” :-)
And then there was Grabit.
At a glimpse, APTs are something that belongs entirely to that grey area of high (geo)politics: most of these campaigns, regardless of their size, are targeting large entities in an apparent attempt to gather intelligence of global importance from their targets. And these targets are mostly governmental organizations, embassies, as well as major players in various industries.
Then Carbanak and Grabit arrived
They are very different from each other, but they do have something in common: neither are playing by a book.
Carbanak is the first ever entirely criminal APT. It has nothing to do with politics; it’s all about stealing money from banks, not extracting valuable data.
Grabit, in turn, is an espionage campaign – it is, strictly speaking, not an APT, but has a purpose similar to that of APTs. And it targets almost exclusively small-to-medium businesses.
Is there a line that can be drawn between these two points? Probably not, but these two campaigns create the grounds for predictions which are within the same trend: commercialization and criminalization.
Simply put, criminals start using APT approaches and techniques for simple illicit profit, gradually switching from the larger targets to the smaller (and softer) ones.
It doesn’t mean that cyberespionage APTs targeting large corporations are going away any time soon, but APT techniques are going to become a problem for a much wider range of businesses. Their nature and size won’t matter much, in fact: criminals tend to be indiscriminate and unscrupulous about whom they attack as soon as there extractable money.
All businesses are potentially targeted by these criminals, but none of them have to fall victim to an attack of any kind, be that something sophisticated and targeted or indiscrete and occasional. Kaspersky Lab’s business products are capable of protecting its users – the companies of any size, from a small office to a large enterprise, from the threats described above.
 APT
APT

 Tips
Tips