
Why the discovery of “big” bugs is a good thing
2014 is making its way into Cybersecurity history books with two global-scale software bugs discovered over 6 months. They are obviously not the last ones, and it is actually a good thing.
3983 articles

2014 is making its way into Cybersecurity history books with two global-scale software bugs discovered over 6 months. They are obviously not the last ones, and it is actually a good thing.

Your primary email account is often the master key that can provide backup access to all other accounts, which is why you must be particularly careful with it.

Kaspersky Lab launches its solution Kaspersky DDoS Protection in Europe. A distributed network of data cleaning centers vs. distributed attacks.
Kaspersky Lab has signed a cooperation agreement with INTERPOL and a memorandum of understanding with Europol to extend the scope of collaboration between the company and the law enforcement agencies in their joint fight against cybercrime.

”Dear Chairman, dear Vice Chairman, dear members of the board, let me present to you the annual report… Oops… Just a moment, we are having some technical issues…”

September’s security news was dominated by three stories: the Home Depot data breach, the Apple celebrity nude photo leak scandal and the Shellshock vulnerability in Bash.

Elena Kharchenko, Head of Consumer Product Management, answers the important security questions that you submitted.

Phishing is the most developed form of Internet scamming. Let’s explore the topic in order to better understand why it became so prominent and what measures one can take to avoid a phishing attack.

We’ve gathered information for patching the most common Linux distros against the notorious Shellshock Bash Bug. If you see we’ve missed something, please drop us a tip!

Even when your iPhone is in your hands or on the table, it can reveal some of your secrets to strangers. Here are 10 tips to prevent this from happening.

Virus Bulletin is a traditionally enterprise-focused event, but each year topics of consumer interest, like Apple malware, hackable devices and Bitcoin are presented.

It’s been a day since the BashBug aka Shellshock bug was disclosed. What real damage has been inflicted and who is most in danger?

The Bash vulnerability affecting Unix, Linux and OS X systems is the latest Internet-wide bug to emerge, and a number of experts are saying it’s more dangerous than OpenSSL Heartbleed.

A new nasty bug discovered in Bourne again shell set the infosec on fire, Heartbleed-style. Is it as dangerous as the notorious OpenSSL flaw? It depends…

Online shopping is typically a money-saving move in and of itself, but there are tactics that you can use to keep even more cash in your pocket.

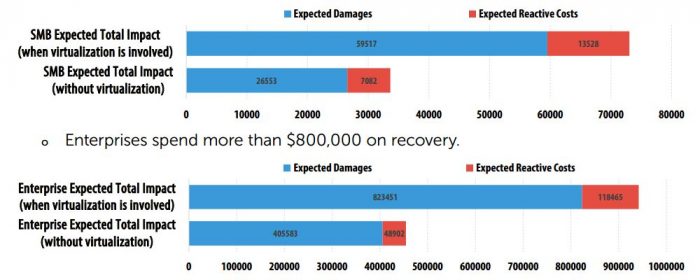
Critical infrastructure operators are often reluctant to deploy full-scale anti-malware protection. They are worried about compatibility, performance, compliance, and the most important thing: possible downtime. But our research shows that malware is the true enemy.

Brian Donohue interviews Adam Firestone, President and General Manager of Kaspersky Government Security Solutions, about why critical infrastructure systems are insecure, and why added on security does not work.

Have you ever imagined that you could be seen on camera without your permission? Unfortunately, it is possible: there is a chance that cybercriminals could access your webcam to watch you.

iOS-based devices have a large share in the enterprise, which assures a strong demand for BYOD-oriented security features. A number of them arrive in iOS 8.

This post is comprised of two topics: a Trojan Opfake.a, which made a lot of buzz earlier this months and analyzing mobile malware at home. The latter is quite possible, but requires protective measures.

With the release of iOS 8, Apple claims it can’t access the personal data on your iPhones and iPads and it can’t give it to authorities. But it seems there’s a catch.