Every year Kaspersky Lab experts evaluate the level of cyber-threats. In 2014 we saw considerable growth in the number of malicious attacks on user computers and mobile devices, further development of financial malware and a change in the vectors of web attacks.
Every year Kaspersky Lab experts evaluate the level of cyber-threats. In 2014 we saw considerable growth in the number of malicious attacks on user computers and mobile devices, further development of financial malware and a change in the vectors of web attacks. In 2013, most web attacks were carried out using malicious web resources located in the USA and Russia while in 2014 Germany hosted more malicious sites than everywhere except the USA. The Netherlands remained in 3rd place.
2014 in figures
- 6.2 billion malicious attacks on user computers and mobile devices were blocked by Kaspersky Lab antivirus products in 2014, one billion more than in 2013.
- 38% of user computers were subjected to at least one web attack over the year.
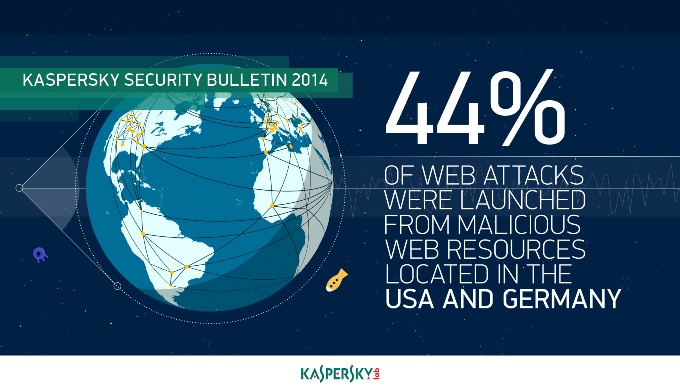
- 44% of web attacks neutralized by Kaspersky Lab products were carried out using malicious web resources located in the US (27.5% of all attacks) and Germany (16.6%). The Netherlands (13.4%) came 3rd.
- Attempts to steal money via online access to bank accounts were blocked on almost 2,000,000 user computers.
- Kaspersky Lab products protected their users from an average of 3.9 million Internet-based attacks a day.
- Kaspersky Lab's web antivirus detected over 123,000,000 unique malicious objects: 74% of them were found at malicious URLs.
- A total of 3.7 million attempts to infect OS X- based computers were blocked by Kaspersky Lab products
- An average Mac user encountered 9 threats during the year
- Kaspersky Lab solutions blocked 1.4 million attacks on Android-based devices, four times as many as last year.
Mobile threats
- 295,500 new mobile malicious programs, 2.8 times as many as in 2013
- 12,100 mobile banking Trojans, 9 times as many as last year
- 53% of attacks involved mobile Trojans targeting users’ money (SMS-Trojans, banking Trojans)
- 19% of Android users (one in five) encountered a mobile threat at least once over the year.
- Mobile malware attacks were registered in more than 200 countries worldwide
“2011 was the year of mobile malware formation, especially on Android-based devices; 2012 was when they developed and 2013 was when they reached maturity. In 2014 mobile malware focused on financial issues: the number of mobile banking Trojans was nine times greater than in the previous year and developing in this area is continuing at an alarming rate,” said Roman Unuchek, Senior Mobile Malware Analyst at Kaspersky Lab.
Financial threats
The fraudsters who specialize in mobile financial malware are probably inspired by their experienced “colleagues” who have been stealing money via personal computers for years. Zeus remains the most widespread banking Trojan with ChePro and Lohmys coming second and third. Three quarters of attacks targeting users’ money were carried out using banking malware but these are not the only financial threats. Bitcoin wallet theft was the second most popular banking threat (14%). Bitcoin mining software (10%) is another threat related to the crypto currency. It uses computing resources to generate bitcoins.
Maria Garnaeva, Security Expert at Kaspersky Lab’s Global Research and Analysis Team, said: “One of the most effective ways to deliver malware to user computers is to exploit vulnerabilities in Oracle Java and in browsers such as Explorer, Mozilla Firefox, etc. In addition, cybercriminals continue to use exploits for Adobe Reader vulnerabilities. These infection techniques remain popular simply because social engineering techniques are still effective. Each year we see how cybercriminals are creative more inventive ways of luring in their victims. That is why recipients are still willing to read a seemingly harmless e-mail from an unexpected source and then open attachments or follow links that expose them to malicious programs.”
To watch Kaspersky Lab's video “Hacked off in 2014: the cyber-battle for cash and privacy”, please click here.
The full report is available on the Securelist website.