Kaspersky Global Research and Analysis Team detected a new malicious campaign targeting Android users. It uses fake wedding invitations to lure victims into installing a malicious application that was labelled by Kaspersky as the Tria Stealer. It forwards content from text messages and emails, along with other data to the attackers, hijacks device owners’ WhatsApp and Telegram accounts to ask for money from friends or family.
With the interception of SMS messages, attackers also have the opportunity to gain access to accounts in different apps or services (for example, online banking) by requesting OTP login codes from these services and reading them in the intercepted SMS messages. The primary targets of the campaign are users in Malaysia and Brunei.
On Android devices it is possible for users to install apps directly from installation files, which come in the APK file format, bypassing official app stores like Google Play. While this can come in handy in some scenarios, it also poses risks and is sometimes used by cybercriminals to spread malware. Specifically, the Tria Stealer is distributed as an APK installation file via personal and group chats on Telegram and WhatsApp, using social engineering to invite the recipients to an alleged wedding and asking them to install the APK to view the invitation card.
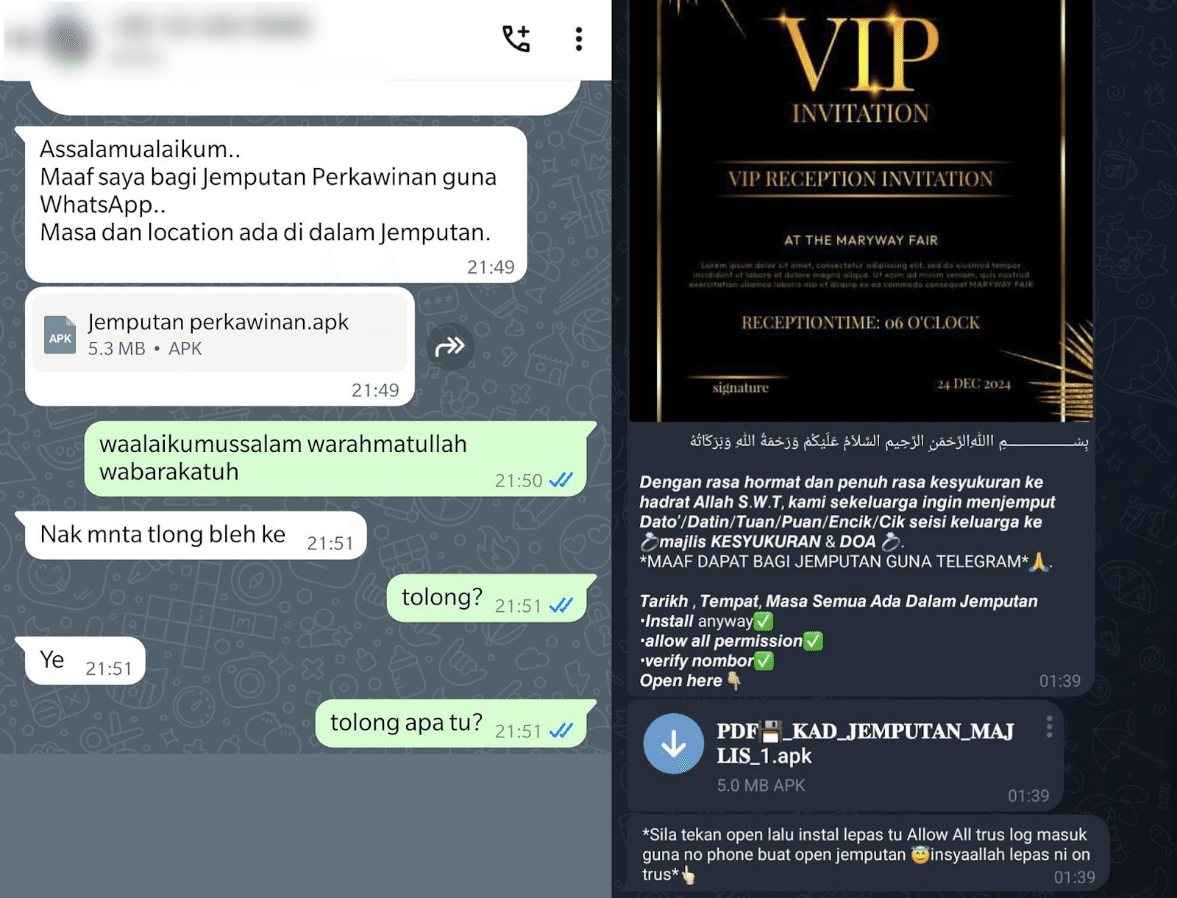
Delivery through a compromised WhatsApp
account (on the left)
and through a compromised Telegram account (on the right)
After it is installed, the malware requests permissions which allow it to access sensitive data and functions, such as reading and receiving text messages, monitoring phone status, call logs, and network activity, as well as performing actions like displaying system-level alerts, running in the background, and starting automatically after device reboot. Collectively, these permissions grant significant control over device operations and the attackers can intercept victim notifications to steal messages and emails. The application mimics a system settings app with a gear icon to trick the victim into thinking that the requests and the app itself are legitimate.
The user is also prompted to enter their phone number, which is sent to the attackers along with the device’s brand and model. All stolen data is transferred to the attackers via Telegram bots.
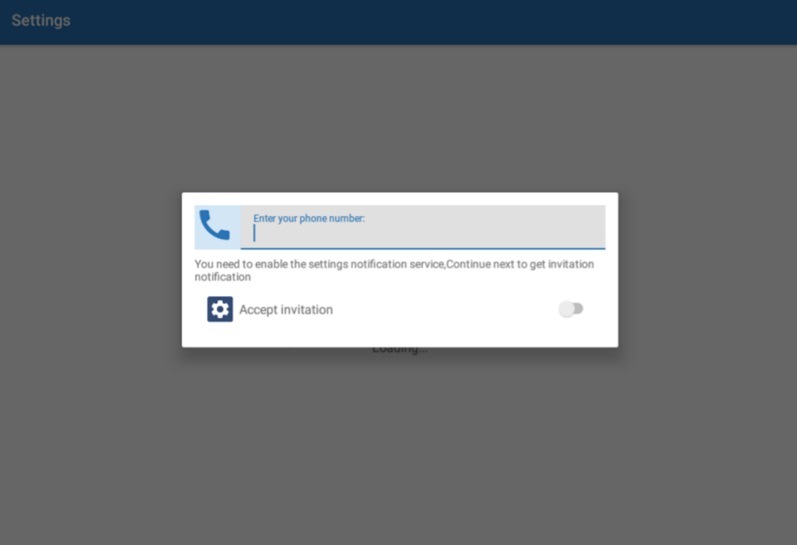
Custom dialog box prompts for the phone number
“This malicious application has been named ‘Tria Stealer’ by Kaspersky based on unique text strings found in the campaign’s samples. Our investigation suggests that this stealer is likely operated by Indonesian-speaking threat actors, as we found artifacts written in Indonesian, namely several unique strings embedded in the malware and the naming pattern of the Telegram bots that are used by the attackers,” comments Fareed Radzi, Security Researcher with Kaspersky GReAT. “Stealers can inflict serious financial losses and privacy breaches, and it’s very important for individuals and corporate users to always be on alert and avoid blindly following requests that they get online, even if these come from someone they know.”
Read more in a post on Securelist.
WhatsApp and Telegram messengers are among the top 10 most popular apps on the Google Play Store in Malaysia as of January 2025. At the beginning of this year, Telegram obtained a license under the Malaysian Communications and Multimedia Commission (MCMC) Act. In 2024, Telegram approached one billion monthly active users globally.
To protect yourself from mobile threats, Kaspersky shares the following recommendations:
- Download apps only from official stores like the App Store, Google Play, Amazon Appstore or others. Apps from these markets are not 100% failsafe, but at least they get checked and there is some filtration system — not every app can get onto these stores.
- Check the permissions of apps that you use and think carefully before giving permissions to a new app, especially when it comes to high-risk permissions such as reading text messages.
- Use a reliable security solution that will detect malicious apps.
About the Global Research & Analysis Team
Established in 2008, Global Research & Analysis Team (GReAT) operates at the very heart of Kaspersky, uncovering APTs, cyber-espionage campaigns, major malware, ransomware, and underground cyber-criminal trends across the world. Today GReAT consists of 35+ experts working globally – in Europe, Russia, Latin America, Asia, Middle East. Talented security professionals provide company leadership in anti-malware research and innovation, bringing unrivaled expertise, passion and curiosity to the discovery and analysis of cyberthreats.
