In the first half of 2022, malicious objects were blocked on every third OT computer, according to the ICS threat landscape by Kaspersky ICS CERT. Most often, attacks against industrial companies were carried out using malicious scripts and phishing pages (JS and HTML). Building automation infrastructure turned out to be the most “restless”: nearly half of the computers (42%) faced cyber threats. Since these systems may be not fully separated from networks of the organizations located in the building, they may be an attractive initial access targets for attackers.
In the first half of 2022, malicious objects were blocked in almost 32% of the OT computers protected by Kaspersky solutions. These computers are used in oil & gas, energy, automotive manufacturing, building automation infrastructures and other spheres to perform a range of OT functions – from the workstations of engineers and operators to supervisory control and data acquisition (SCADA) servers and Human Machine Interface (HMI).
Rising threats in H1 2022: malicious scripts, phishing pages and spyware
Most often in the last six months, perpetrators attempted to attack industrial computers using malicious scripts and phishing pages (JS and HTML) – these objects were blocked on almost 13% of the total number of the computers protected. This category of threats also showed the most dynamic growth compared to the previous half of the year, rising by 3,5 percentage points.
Malicious scripts and phishing pages are one of the most common ways to spread spyware. In H1 2022 it was detected on almost 9% of OT computers, seeing a rise by 0,5 percentage points between H1 2022 and H2 2021. The other way spyware can be spread is by phishing emails with a malicious document attached. Kaspersky reports a dramatic increase of nearly two times – to almost 6% – in the percentage of OT computers where malicious documents were blocked.
“It is vital to protect OT endpoints as well as IT ones with a dedicated solution, properly configured and kept up-to-date. The OT network should be separated, all remote connections and communications secured, monitored and controlled, any unauthorized access prevented. A proactive approach to identifying and eliminating possible vulnerabilities and relevant threats could save millions on incident costs”, - comments Kirill Kruglov, senior researcher at Kaspersky ICS CERT.
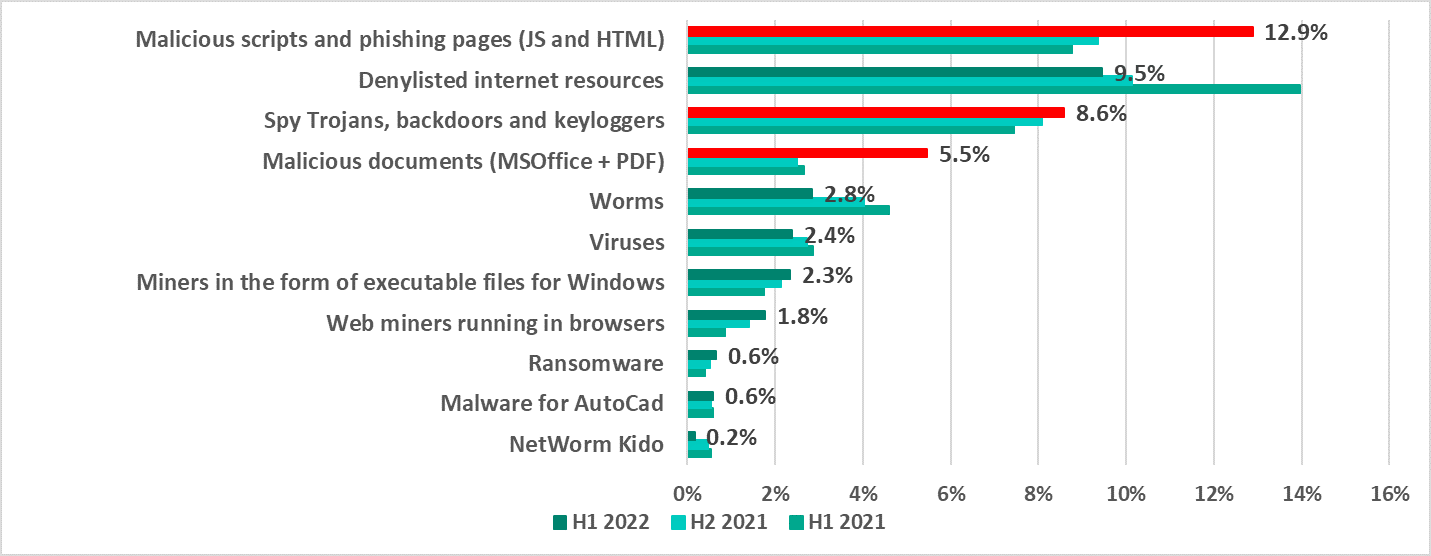 Percentage of OT computers
in which malicious objects from various categories were blocked
Percentage of OT computers
in which malicious objects from various categories were blocked
Building automation turned out to be the most “restless” type of OT infrastructure
Nearly half of the computers (42%) in building automation infrastructure, also referred to as Building Management Systems (BMS), faced cyber threats. These computers would normally belong to service companies, managing automated systems in business or shopping centers, municipalities and other types of public infrastructure. As for the industrial facilities and critical infrastructure objects, they often own the onsite building management systems.
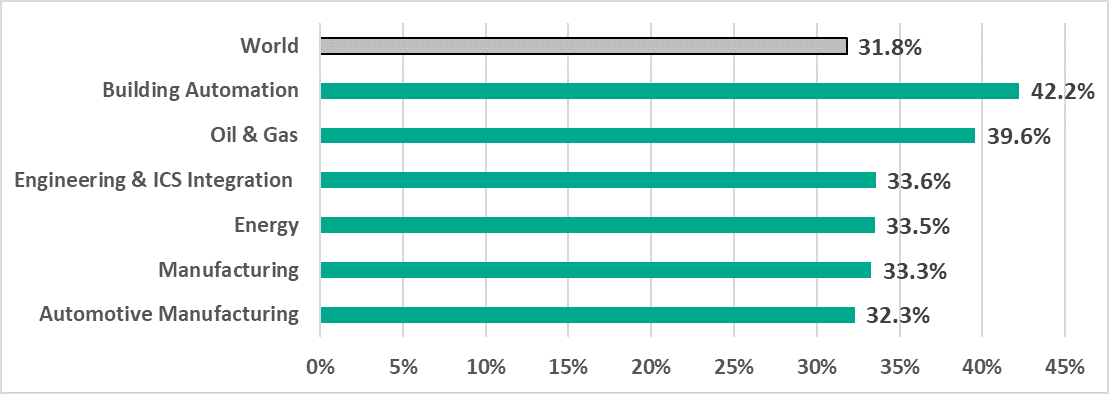
Percentage of OT computers where malicious objects were blocked in selected industries in H1 2022
In H1 2022 Building Management Systems (BMS) became the most "restless" type of OT infrastructure in terms of attackers’ activity, taking leading positions by the percentage of affected devices from different threat sources, namely internet resources (23%), malicious email attachments and phishing links (14%, which is two times more than the global average), malicious documents (11%), trojans, backdoors and keyloggers (13%) and others.
Engineers and operators of building automation use Internet resources and e-mail more actively than in other OT infrastructures. Besides, BMS may have no proper separation from other internal networks physically located inside the building, and therefore, may be an attractive target for sophisticated threat actors.
«It is quite natural that this type of environment is experiencing the impact of attackers’ activity for their high exposure and relatively low cyber security maturity state. Attackers compromise systems that could potentially have connections to internal networks of factories, public spaces, or even critical infrastructure facilities. As for the smart cities and public infrastructures, the systems may manage an entire district with access to lighting control, road traffic management and information, and other types of services for citizens – a real “piece of cake” for perpetrators. What is more alarming, 14% of all Building Management System (BMS) computers were attacked with the use of phishing emails, which is 2 times bigger than the global average”, says Kirill Kruglov, senior researcher at Kaspersky ICS CERT.
Read more about the ICS threat landscape in H1 2022 on the Kaspersky ICS CERT website.
To keep your OT computers protected from various threats, Kaspersky experts recommend:
- Conducting regular security assessments of OT systems to identify and eliminate possible cyber security issues.
- Establishing continuous vulnerability assessment and triage as a basement for effective vulnerability management process. Dedicated solutions like Kaspersky Industrial CyberSecurity may become an efficient assistant and a source of unique actionable information, not fully available in public.
- Performing timely updates for the key components of the enterprise’s OT network; applying security fixes and patches or implementing compensating measures as soon as it is technically possible is crucial for preventing a major incident that might cost millions due to the interruption of the production process.
- Using EDR solutions such as Kaspersky Endpoint Detection and Response for timely detection of sophisticated threats, investigation, and effective remediation of incidents.
- Improving the response to new and advanced malicious techniques by building and strengthening your teams’ incident prevention, detection, and response skills. Dedicated OT security trainings for IT security teams and OT personnel is one of the key measures helping to achieve this.
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 240,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.
