The recent Kaspersky report “Pushing the limits: How to address specific cybersecurity demands and protect IoT” revealed that 53% of businesses have faced a situation where they were unable to launch new projects because they could not address cybersecurity risks. This can be linked to troubles finding an appropriate security solution that would not cause performance, maintenance, or other issues to their project.
When developing or transforming a business, it is important to scale up protection against cyberthreats. According to an Accenture survey, almost 80% of organizations introduce innovations faster than they’re able to protect them. New subsidiaries, product development, digitalization or switching to remote work can all demand rebuilding of corporate networks in a more secure way. This means the implementation of additional protection tools or a sudden increase of licenses and or a change in corporate security policies.
For some companies, addressing new cybersecurity risks can become a real challenge. Of all the projects businesses have had to discard due to these issues, the most common is the implementation of new IT solutions (40%). This is closely followed by changes in corporate policy (39%) and the launch of new business projects (38%).
This issue reflects another finding from the report which shows around three-in-four organizations (74%) have, at times, been unable to find an appropriate security solution.
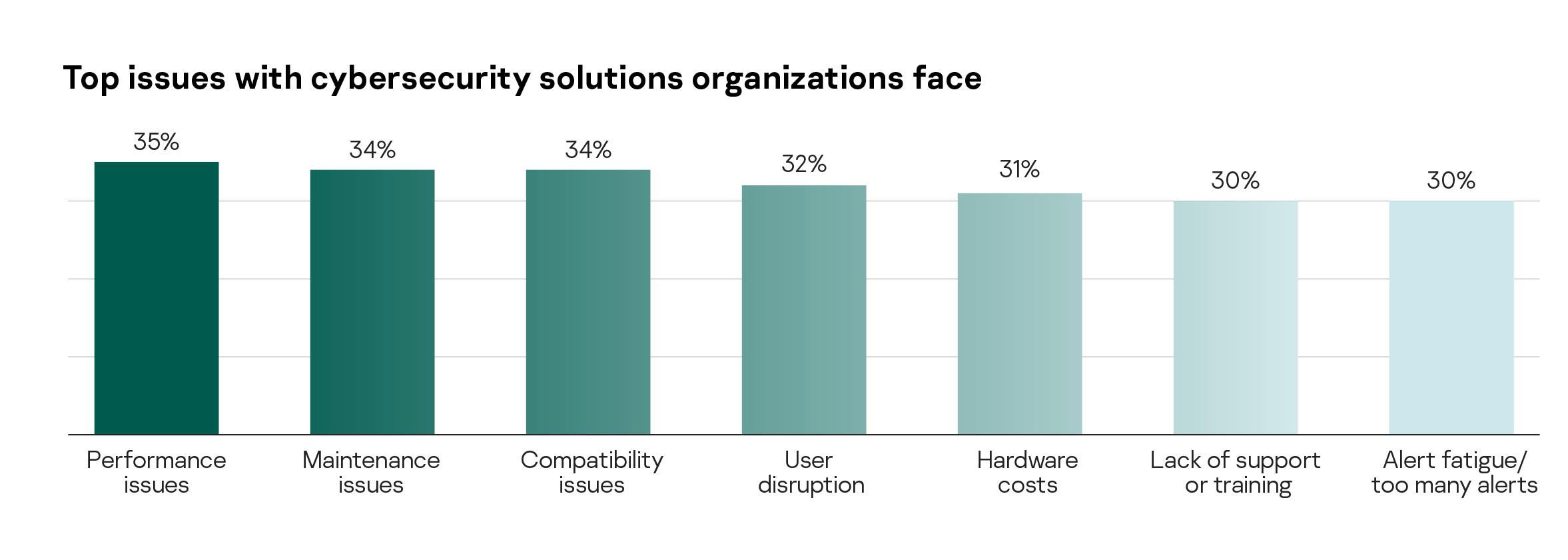
Protection tools may not be suitable for various reasons, the most common being performance issues (35%) and difficulties with maintenance (34%). These are critical as they can affect the level of protection provided, as well as the compatibility issues (34%) having an impact on business processes. This is particularly relevant when it comes to protecting specialized software or firmware, such as industrial, manufacturing, or IoT. It is therefore important that IT security teams find compromises and workarounds to deliver both performance and security.
“With the current pace of business innovation, cybersecurity should enable and support new initiatives, not stop them. To achieve this, every new solution should be approached with a dedicated cybersecurity risk assessment and analysis of available protection measures. For critical systems, such as Industrial IoT, there are new, solid security approaches such as Cyber Immunity. Along with the proven must-haves – network segmentation, nodes’ protection and awareness – this innate resistance to cyberattacks should make cybersecurity a reliable business partner,” – commented Andrey Suvorov, CEO at Aprotech (Kaspersky’s subsidiary IIoT company).
To help keep the protection up to date with changes, Kaspersky recommends adopting these practices:
- When choosing a cybersecurity solution, check performance tests from reputable laboratories and analytics companies such as: AV-TEST, NSS Labs, SE Labs, AV-Comparatives and ICSA. Customer feedback platforms like Gartner Peer Insights can also provide real life impressions about these products.
- Consider outsourcing the most difficult cybersecurity tasks such as organizing threat hunting, incident investigation, and response. This can be particularly helpful if a company doesn’t have enough human resources. Virtual CISO, external SOC, and managed detection and response services can help.
- For industrial control systems (ICS), there are threat intelligence services with vulnerability databases, including Kaspersky Threat Intelligence Portal. This service collects information on vulnerabilities and provides it in an actionable manner. Customers can then develop mitigating measures if patches aren’t yet available or can’t be installed due to process continuity requirements, system certification needs, or compatibility issues.
- For IoT related projects, IoT Security Maturity Model’s approach can help companies evaluate all the steps they’d need to go through to achieve a minimally sufficient level of IoT protection.
- To protect IoT or automotive projects, consider systems that are secure-by-design. KasperskyOS enables a Cyber Immune approach to development, which renders most attacks ineffective for KasperskyOS-based solutions.
The full report, “Pushing the limits: How to address specific cybersecurity demands and protect IoT” is available to download here.
