Kaspersky researchers analyzed the lifecycle of phishing pages and discovered that one third of phishing pages cease to exist within a single day, making the first hours of a page's life the most dangerous for users. This is the moment when a vast range of phishing links are spread before the site is detected and entered into databases by anti-phishing engines.
Kaspersky researchers analyzed the lifecycle of phishing pages and discovered that one third of phishing pages cease to exist within a single day, making the first hours of a page's life the most dangerous for users. This is the moment when a vast range of phishing links are spread before the site is detected and entered into databases by anti-phishing engines.
In this study, the researchers analyzed 5307 examples of phishing pages from July 19 to August 2, 2021. A significant portion of the links (1784) stopped being active after the first day of monitoring, and numerous pages cease to exist in the first hours. As a result, as early as 13 hours after monitoring, a quarter of all pages were inactive, and half of the pages lived no more than 94 hours.
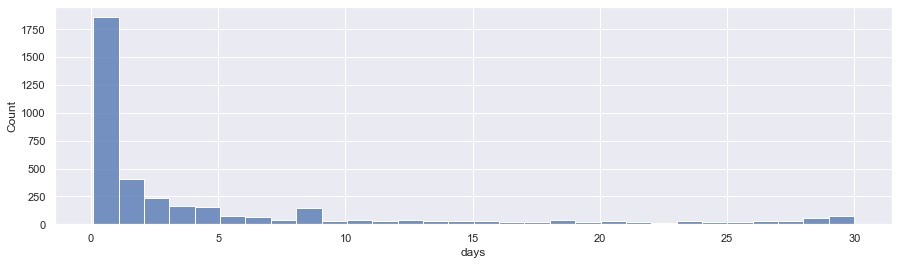 Classification of phishing links according to the number of active days
Classification of phishing links according to the number of active days
The lifetime of a phishing page depends on the moment it becomes visible to the site administrators and is removed by them. Even if phishers have deployed their own server on the purchased domain and are suspected of fraudulent activity, the registrars may deprive the phishers of the right to host the data on it.
With every hour of life of a new site, it appears in more anti-phishing databases, which means that fewer potential victims will visit it. Because the lifecycle of such pages is so short, phishers are interested in distributing links to phishing pages as soon as they are created, to ensure the widest possible reach to potential victims in the first hours while their sites are still active.
Much more often, attackers choose to create a new page instead of modifying an existing one. In addition, very rarely, phishers may change the page in order to avoid being blocked. For example, if phishers use a brand as bait, they might alter it to another one. However, most pages are simply blocked by the time phishers decide to change the form of activity. There is another method: creating randomly generated code elements that are not visible to the user but still prevent anti-phishing engines from blocking them for an uncertain amount of time. Nevertheless, the Kaspersky anti-phishing engine skillfully bypasses these tricks.
Among the pages whose content is modified to avoid being blocked, the vast majority mimic the PUBG giveaway, one of the most well-known events in this popular online game. Attackers change the content of the page in a timely manner to match the new season, a temporary event in the game, or to make the phishing page resemble the original as closely as possible.

 By sharing personal data in a fake PUBG giveaway, the player's account
falls into the hands of fraudsters
By sharing personal data in a fake PUBG giveaway, the player's account
falls into the hands of fraudsters
“Such research is not only useful for updating our databases, but it can also be used to improve incident response. For example, if an organization is undergoing a spam attack with fraudulent links, it's important to repel it in the first hours, as it’s the most beneficial time for phishers’ activity. In turn, it is important for users to remember that when they receive a link and have doubts about the legitimacy of the site, we recommend they wait for a few hours. During that time, not only will the likelihood of getting the link in the anti-phishing databases increase, but the phishing page itself can stop its activity. Users can rest assured that they are well protected, since we not only catch phishing, but also conduct research to improve how well we repel attacks”, comments Egor Bubnov, security researcher at Kaspersky.
Read the full report about the lifecycle of phishing pages on Securelist.
To avoid becoming a victim of phishing, Kaspersky recommends users to:
● Avoid logging in to online banking and similar services via public Wi-Fi networks. Hotspots are convenient, but it’s better to use a secure network. Open networks can be created by criminals who, among other things, spoof website addresses over the connection and thereby redirect you to a fake page.
● Sometimes e-mails and websites look just like real ones. It depends on how well the criminals did their homework. But the hyperlinks, most likely, will be incorrect — with spelling mistakes, or they can redirect you to a different place.
● It’s a safe practice to only enter a username and password over a secure connection. Even the HTTPS prefix is not always the indicator that the connection to the site is secure, because fraudsters can issue an SSL certificate.
● Install a trusted security solution and follow its recommendations. Secure solutions will solve the majority of problems automatically and alert you if necessary.
For organizations’ protection, Kaspersky suggests the following:
● Provide your staff with basic cybersecurity hygiene training. Conduct a simulated phishing attack to ensure that they know how to distinguish phishing emails
● Use a protection solution for endpoints and mail servers with anti-phishing capabilities, such as Kaspersky Endpoint Security for Business, to decrease the chance of infection through a phishing email.
● If using Microsoft 365 cloud service, don’t forget to protect it too. Kaspersky Security for Microsoft Office 365 has a dedicated anti-spam and anti-phishing as well as protection for SharePoint, Teams and OneDrive apps for secure business communications.
About Kaspersky
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 240,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.
