Kaspersky Labs, an international data-security software developer, informs users about the discovery of a new worm generation that is capable of Internet functioning absolutely sans using files. This type of malicious program conducts all operations-including spreading and perpetrating DDoS...
Kaspersky Lab, an international data-security software developer, informs users about the discovery of a new worm generation that is capable of Internet functioning absolutely sans using files. This type of malicious program conducts all operations-including spreading and perpetrating DDoS attacks-exclusively via a computer's system memory or TPC-IP packets; therefore, greatly complicating detection and neutralization.
The first family member of this network worm, known as "Bady" (a.k.a. "Code Red"), according to ZDNet, has already infected almost 12,000 servers around the world, and also has administered large-scale DDoS attacks on the White House, Washington, D.C. (http://www.whitehouse.gov), disrupting the sites regular operations. "Bady" infects only those computers operating on Windows 2000 (without any Service Packs installed) and Microsoft Internet Information Server (IIS) with the Indexing Service switched on. Namely because this software is widely used on the commercial Web, FTP, and e-mail servers, the worm has spread widely. The scale of the epidemic could have been far worse and devastating had it infected other Windows versions, such as Windows NT and XP; however, the worm's creator specifically targeted his "parasite" at Windows 2000. In order to penetrate remote computers, Bady exploits a security breach in IIS that was detected in June of this year that allows a malefactor to run arbitrary code without a user's knowledge. This is accomplished by Bady sending a special request to a randomly selected server to run the worm itself on an indicated computer. The worm, in turn, attempts to penetrate other servers. Hundreds of the worm's active processes, simultaneously in the computer memory, jam the server's operation. On June 18 of this year, Microsoft released a patch remedying this breach, however, most computer users to this point have ignored the warning and have yet to install the necessary software. "Bady once again proves the need to timely install software updates. Currently, this is one of the most important security measures for both individual home users and corporate users alike," commented Denis Zenkin, Head of Corporate Communications for Kaspersky Lab. "The current worm clearly demonstrates that a hacker only requires several days in order to unleash malicious code through the use of a security breach." The most important feature of Bady is that it does not use any files. "This worm is absolutely unique: it is either present in the system memory of the infected computer, or in the TCP/IP packet being transferred to a remote computer," elucidated Eugene Kaspersky, Head of Anti-Virus Research for Kaspersky Lab. "Such a 'fileless' worm presents a serious threat for server defense, inasmuch as it demands the installation of a special anti-virus module for modern firewalls." In addition to jamming the operation of an infected computer, Bady has other side effects. Firstly, the worm intercepts the user requests for viewing the infected Web-sites' content and replaces the original pages with the following message: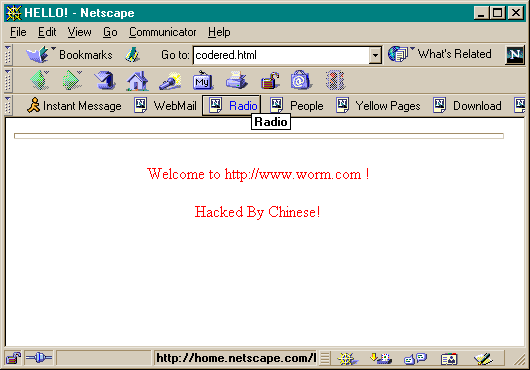 After having shown the bogus, hacked Web-site page within 10 hours, the worm automatically returns everything to norm so that a user only views the original site contents. It is important to note that this only occurs on sites where a "US English" codepage is set as default.
Secondly, from the 20th to the 28th of each month, the worm perpetrates a DDoS attack on the US White House's Web site (www.whitehouse.gov). In order to accomplish this, the worm copies to all the infected computers upon start-up, sending numerous connection requests to this Web site. The enormous amount of requests results in Web site overloads and the refusal of other service requests.
In order to neutralize and protect against Bady worm penetration, Kaspersky Lab recommends that users install the patch thwarting this breach in the IIS system security ASAP.
Users are also urged to consult these useful links:
Microsoft Security Bulletin MS01-033
For more technical details about the Bady worm, please see the Kaspersky Virus Encyclopedia at www.viruslist.com.
After having shown the bogus, hacked Web-site page within 10 hours, the worm automatically returns everything to norm so that a user only views the original site contents. It is important to note that this only occurs on sites where a "US English" codepage is set as default.
Secondly, from the 20th to the 28th of each month, the worm perpetrates a DDoS attack on the US White House's Web site (www.whitehouse.gov). In order to accomplish this, the worm copies to all the infected computers upon start-up, sending numerous connection requests to this Web site. The enormous amount of requests results in Web site overloads and the refusal of other service requests.
In order to neutralize and protect against Bady worm penetration, Kaspersky Lab recommends that users install the patch thwarting this breach in the IIS system security ASAP.
Users are also urged to consult these useful links:
Microsoft Security Bulletin MS01-033
For more technical details about the Bady worm, please see the Kaspersky Virus Encyclopedia at www.viruslist.com.