Because cybercriminals are constantly improving their sophisticated hacking techniques, combating APTs requires not only cutting-edge security solutions, but also access to the most comprehensive and constantly updated threat intelligence. The MITRE ATT&CK Framework provides a comprehensive outlook of all known techniques and procedures utilized by adversaries, so you can understand attacks from the adversary’s standpoint and catch attackers not by Indicators of Compromise – which are easy to change - but by their behavior, which is far more difficult to change.
By identifying the potential adversary perpetrating a cyber-incident, you can gain an understanding of all the tactics and attack methods ever used by that threat actor and by doing so, focus on detecting and mitigating the associated activity. For example, if a threat actor is known for adding Registry run keys to achieve persistence, the target organization can monitor the Registry for new run keys that shouldn’t be in that environment, and contain attacks at an early stage. Or if a threat actor is known for exploiting specific vulnerabilities, the target organization can check for and patch those vulnerabilities before exploitation. These are just simple examples in a long list.
However, the biggest challenge is operationalizing this vast knowledge base, and it’s a daunting task for even the most experienced teams. Many security vendors (Kaspersky is one of them) are starting to leverage the ATT&CK framework inside their products, so it’s a good idea to look into the technologies, services and products that provide mapping to the ATT&CK framework out-of-the-box. Doing so will give you access to that knowledge operationalized without the need to invest significant company resources into in-house research.
Kaspersky’s Global Research and Analysis Team (GReAT) is an elite group of renowned cybersecurity experts located around the world who bring their local expertise and threat intelligence understanding to the task of monitoring the global threat landscape. The team tracks 300+ APT actors and over 400 campaigns targeting all sectors and regions with 120+ APT Intelligence reports released every year. These reports provide an overview of each APT group, including country of origin, aliases, list of previous targets and victims, as well as the typical tools and descriptions of past campaigns.
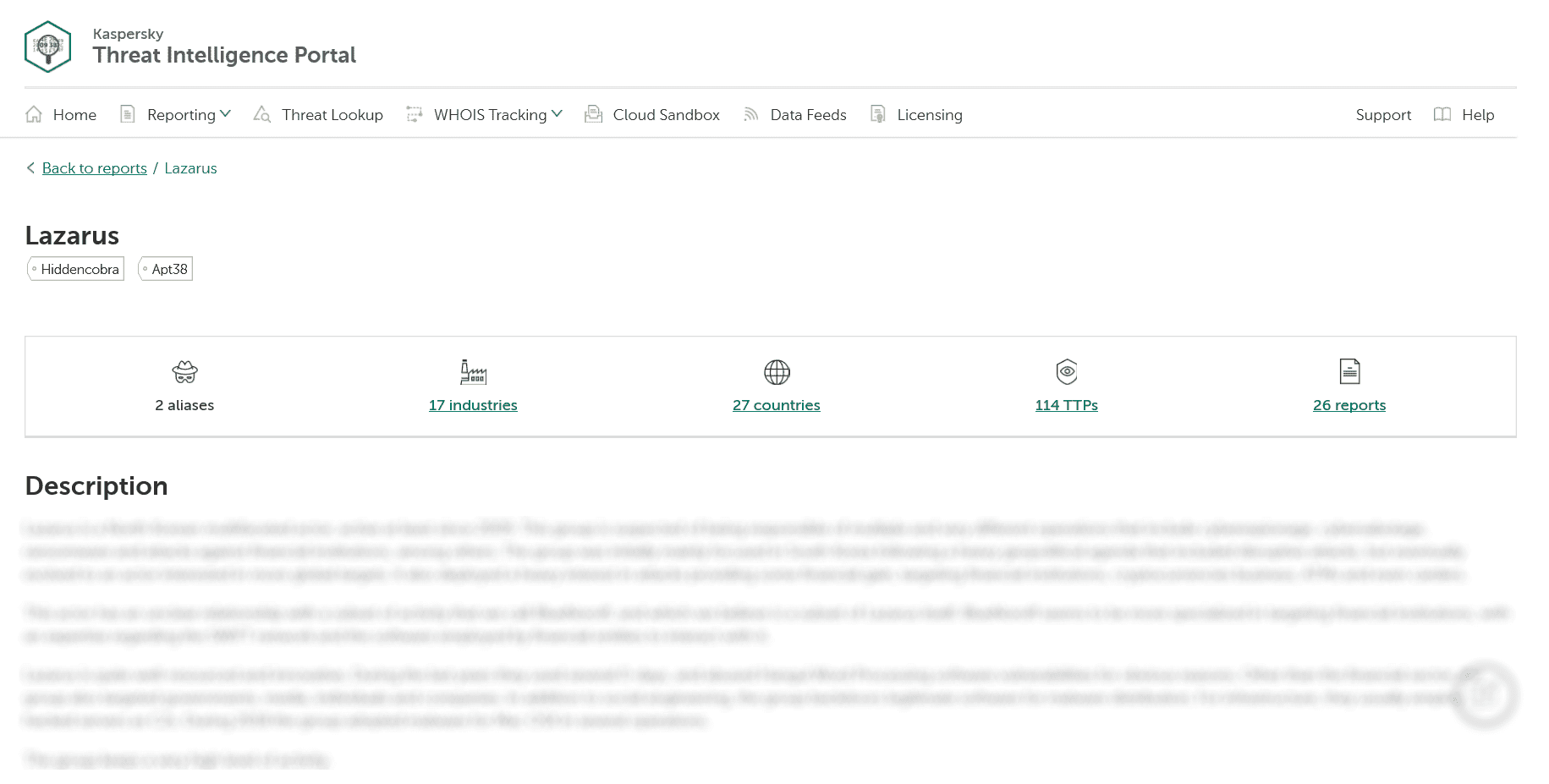
All the attack techniques and procedures observed are mapped to MITRE ATT&CK. Experts break down the attacks into several phases in accordance with the PRE-ATT&CK (covers an attacker’s behavior before an actual attack happens) and ATT&CK Enterprise matrixes, showing which tactics and techniques were leveraged at every stage. This complements Kaspersky’s own descriptive methodology, which divides a targeted attack into infection vector, implants and infrastructure phases. Kaspersky has been providing our own descriptive TTPs for several years now.
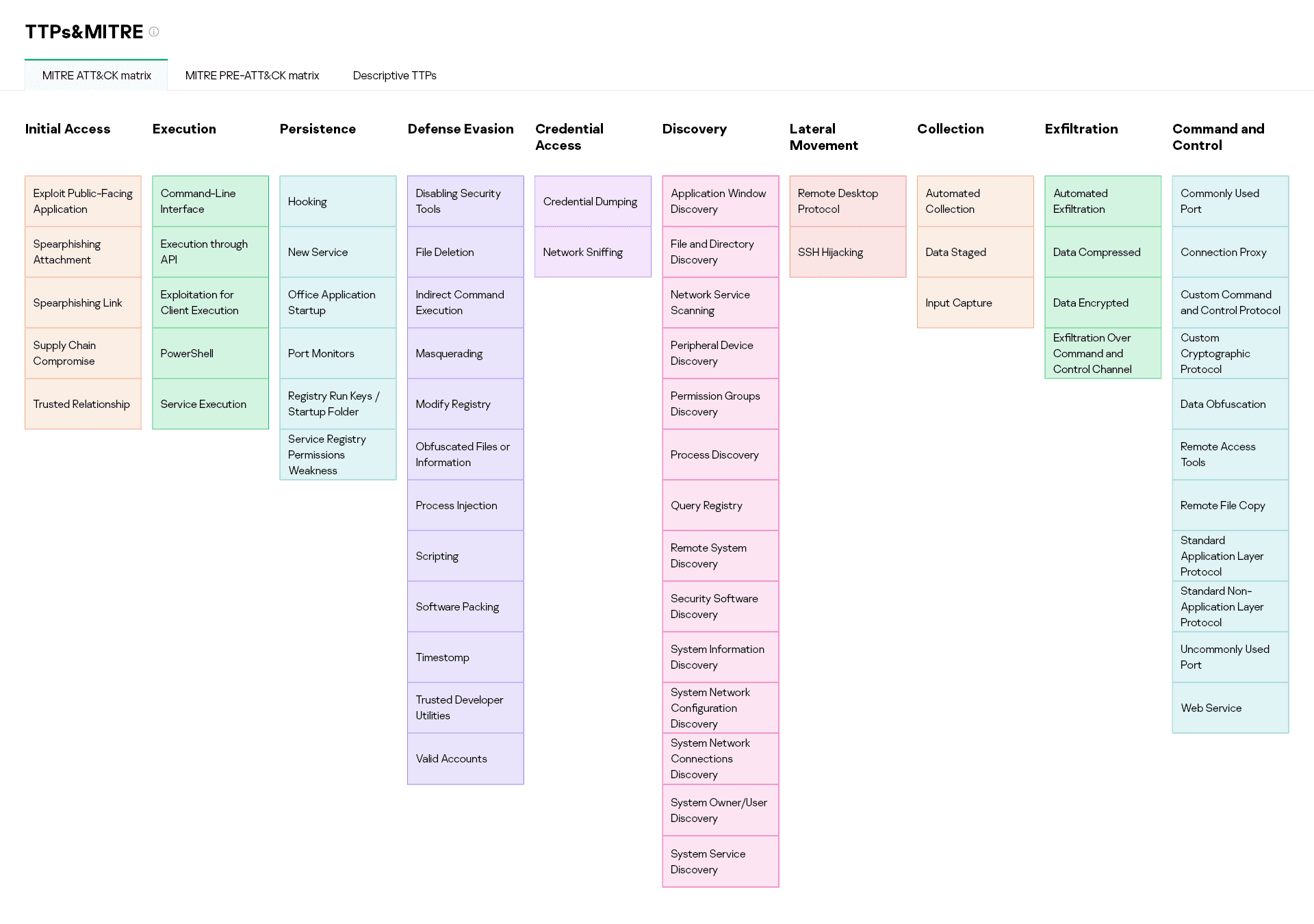
Mapping to ATT&CK lets you operationalize Kaspersky’s unique threat intelligence more effectively by implementing the various use cases of the framework. If a company wants to test its existing defenses against a specific adversary, it can allow tailoring of red teaming activities to the relevant attack techniques. If a SOC wants to improve its detection and response capabilities, it can perform gap analysis to further develop and prioritize the corresponding security monitoring use cases. And so on. The only requirement that is valid in most cases is to ensure that a company has the sources of telemetry needed to detect the specific techniques and procedures described in the framework.
Leveraging MITRE ATT&CK translates Kaspersky’s unique APT expertise and knowledge into common language. It helps to gain deeper insights into your adversaries, improve how you communicate the associated threats throughout the company, and guarantee informed defense in your organization.
Read about our participation in ATT&CK Evaluations - in other posts of Kaspersky in MITRE ATT&CK project.