At the beginning of 2020, The MITRE Corporation announced the publication of a knowledgebase of methods used to attack Industrial Control Systems - MITRE ATT&CK® for ICS. One of the most serious threats dealt with in this matrix is the attack based on Industroyer malware. MITRE experts have analyzed all available data on this threat and grouped all the actions that could be applied at every stage of this attack, providing detailed descriptions. This is a great opportunity for anyone looking to assess their ICS protection solution's ability to deal with complex multi-stage attacks
In this paper, we'd like to demonstrate how our products - Kaspersky Industrial CyberSecurity for Networks (KICS for Networks) and Kaspersky Industrial CyberSecurity for Nodes (KICS for Nodes) - can respond to the Industroyer techniques mapped by MITRE.
Overview
Industroyer, also known as CrashOverride, is sophisticated multi-component malware designed to disrupt the working processes of industrial control systems, especially those used in electrical substations. It's the first malware ever seen to have been specifically designed to attack power grids. The first known Industroyer attack occurred in December 2016.
In the ATT&CK for ICS database, all individual ‘techniques’ (methods of attack) are grouped around a number of ‘tactics’ (attack stages). MITRE defines these tactics as: Initial Access, Execution, Discovery, Collection, Inhibit Response Function, Impair Process Control and Impact. The colored cells in the matrix below highlight the techniques used in Industroyer-based attacks:
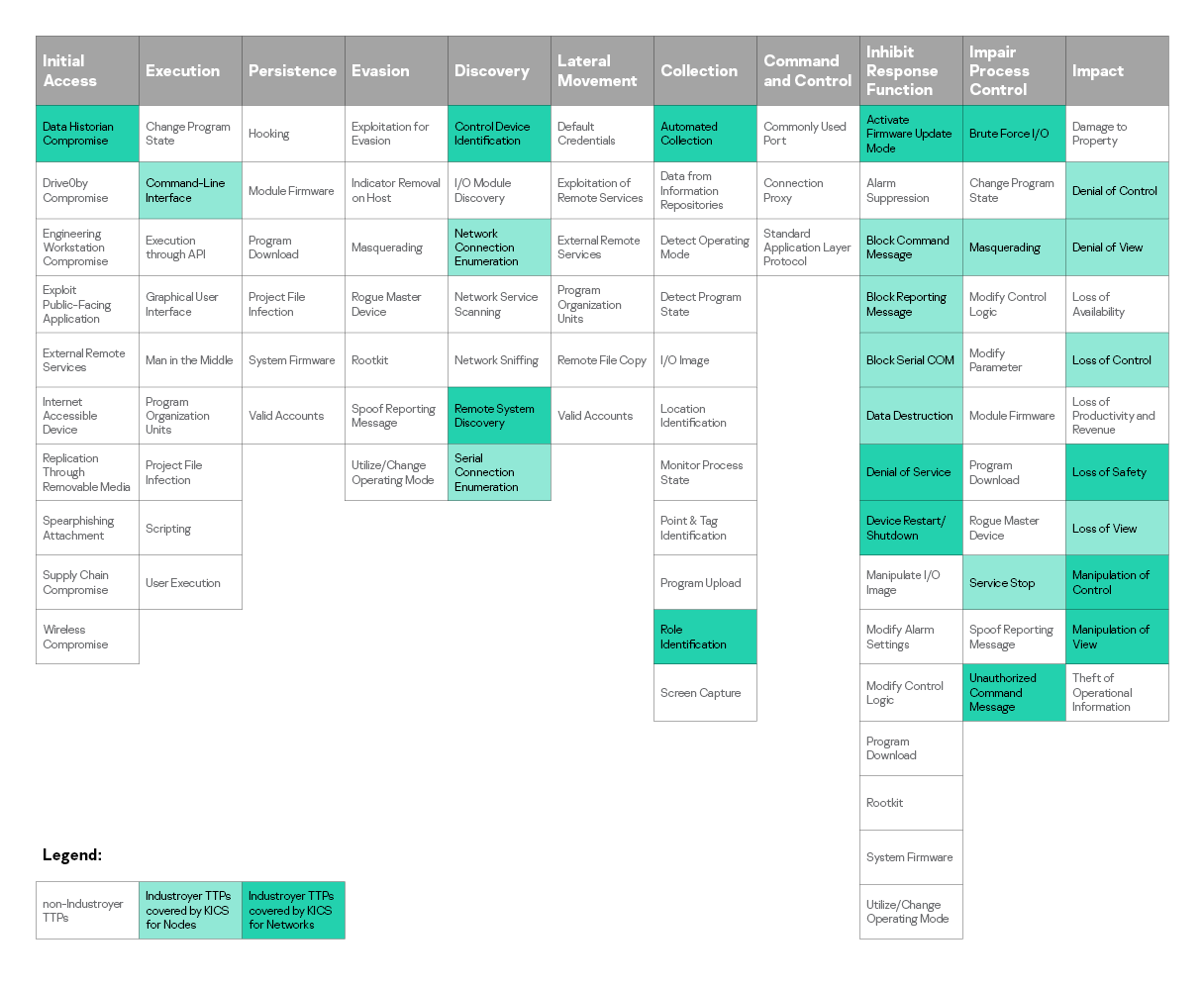
In the illustration below, we’ve highlighted the Industroyer techniques detected by KICS for Networks and KICS for Nodes in this matrix. There then follows a detailed report on our products' response to each of the techniques listed.
Tactic: Initial Access
Technique: Data Historian Compromise (T810)
At the initial phase of the intrusion, the adversaries use some legitimate ways to explore the attacked network, and specialized tools in order to collect user data. Let's suppose that these first steps of the attack are based on MS SQL servers' compromise. To reach these hosts, adversaries could scan the network and gain unauthorized access. KICS for Networks detects this type of activity with Asset Management (AM) and Intrusion Detection System (IDS), as shown below:
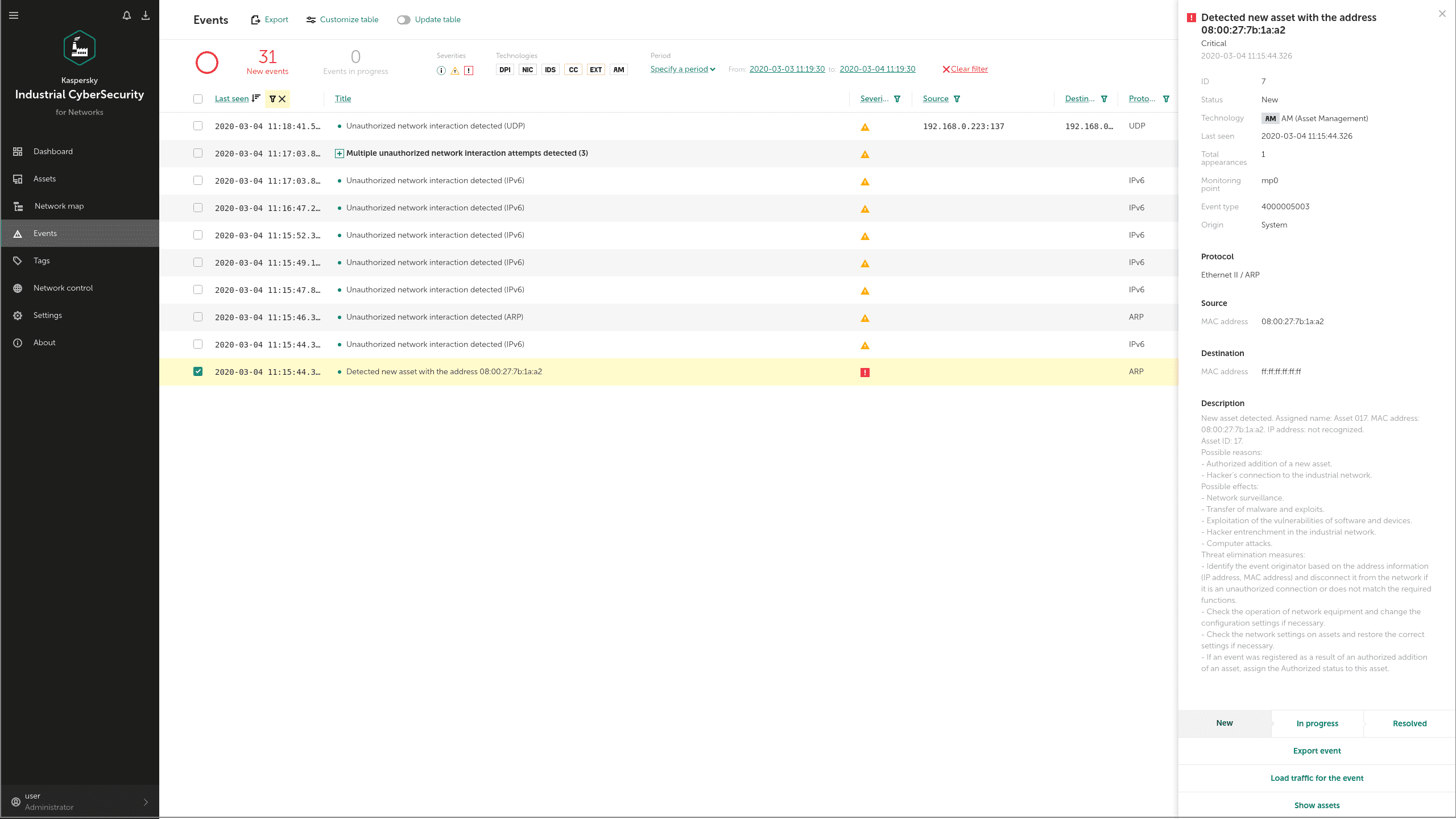
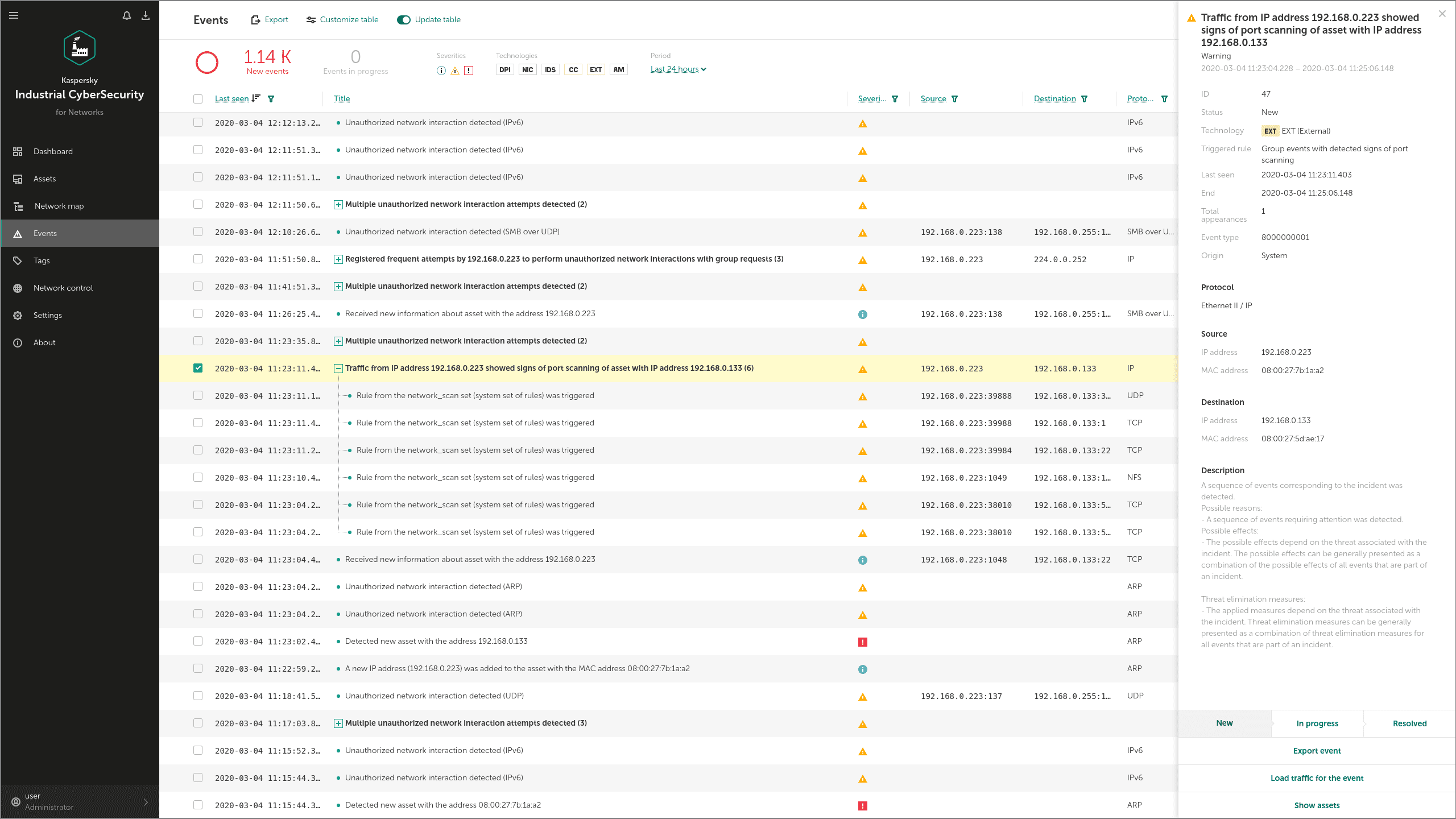
To run a remote process, the adversary has used a standard command (xp_cmdshell) of the compromised MS SQL server. This activity is also detected by our IDS component:
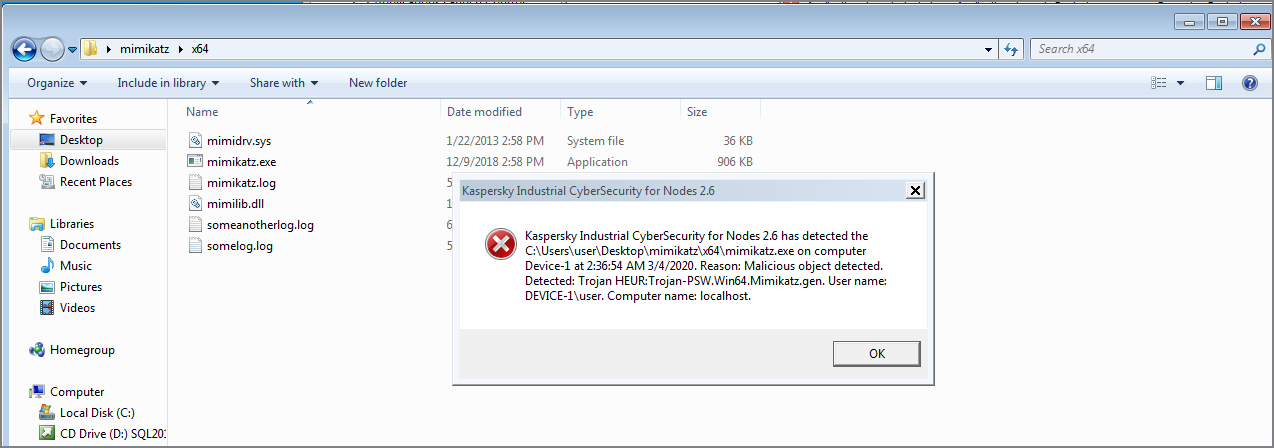
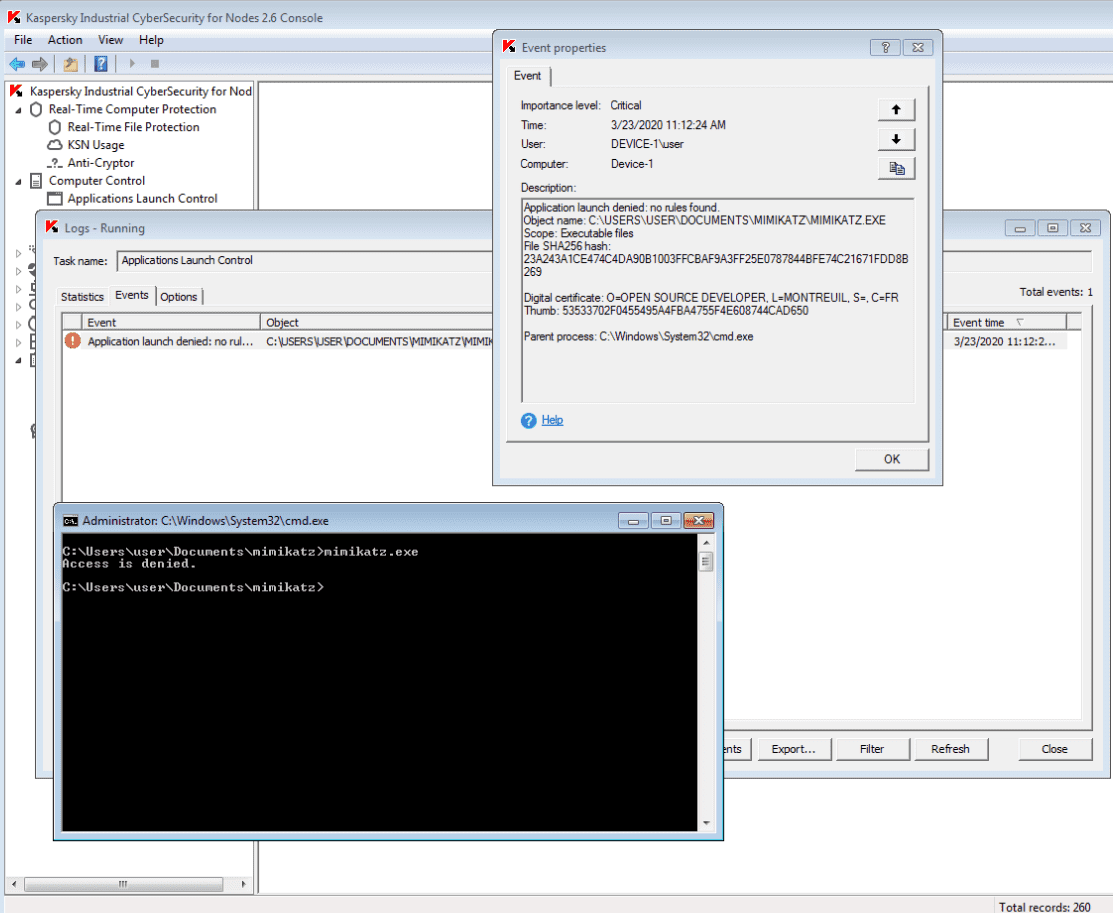
Now let's suppose the adversary tries to use the hacker tool mimikatz to collect user authentication data. On the host layer, this attempt is detected by the Real-Time Protection component of KICS for Nodes. The use of mimikatz is also blocked by the Application Launch Control module:
Tactic: Execution
Technique: Command-Line Interface (T807)
Attackers who want to run Industroyer malware use a command-line interface call with a specific parameter. Here’s an example of such a command: it will execute an Industroyer module for the industrial protocol EC 60870-5-104 (or simply IEC 104). This protocol is used in telecommunication networks for automation systems (mainly telemechanics).
In KICS for Nodes, this type of event is detected by the Application Launch Control module:
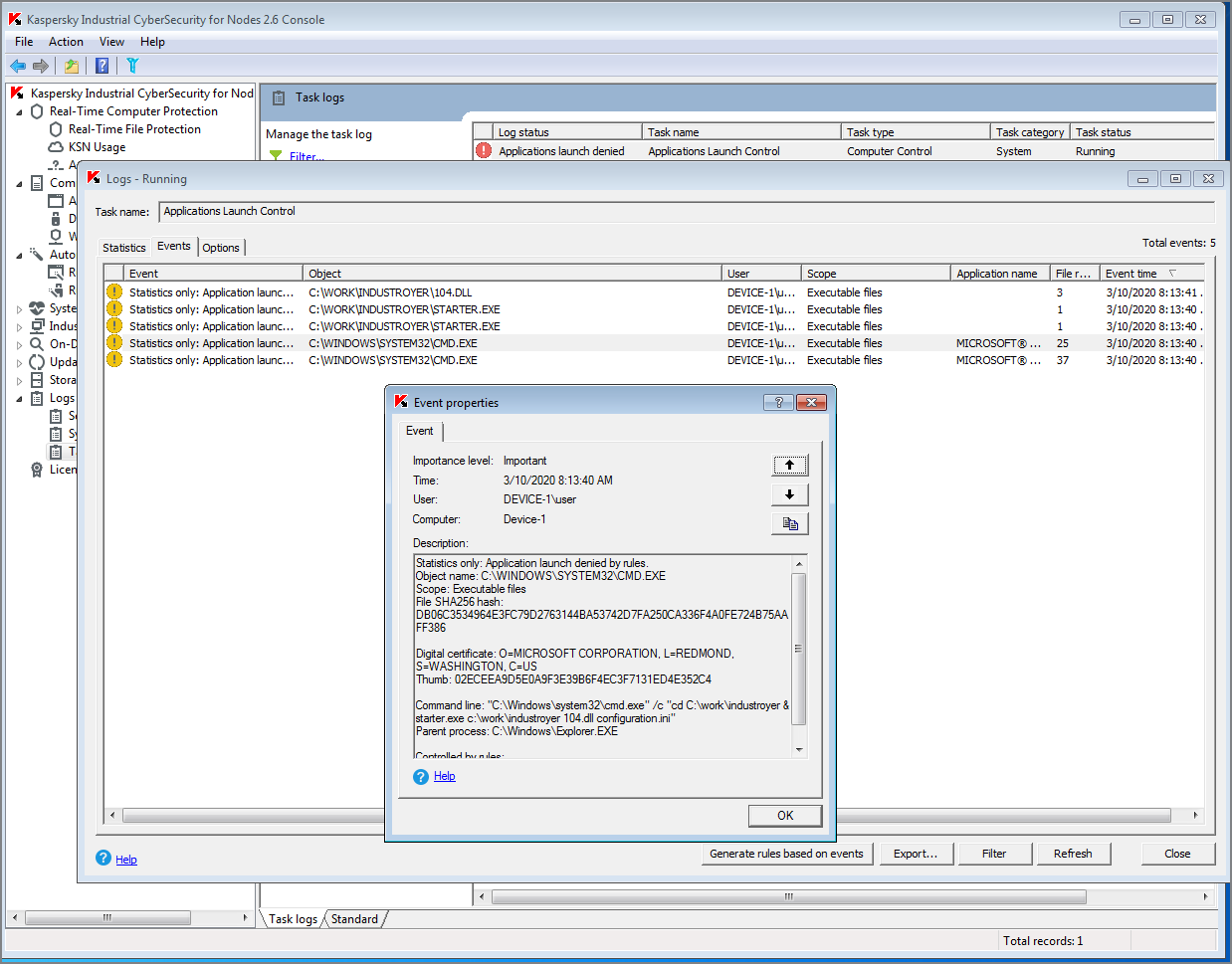
Tactic: Discovery
Technique: Network Connection Enumeration (T840)
To explore device communication patterns, adversaries may perform network connection enumeration using system utilities - ipconfig or netstat. The Application Launch Control in KICS for Nodes detects the unauthorized launch of such tools:
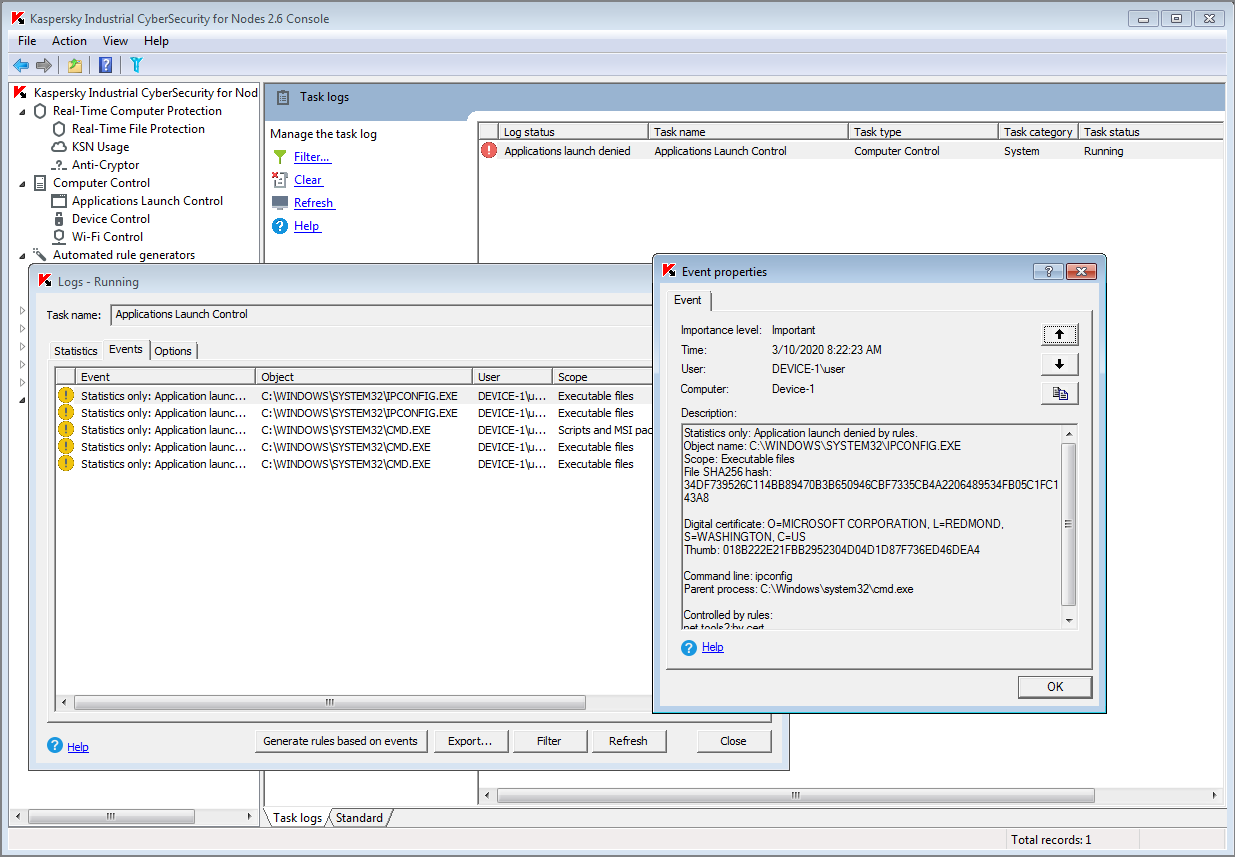
Technique: Remote System Discovery (T846)
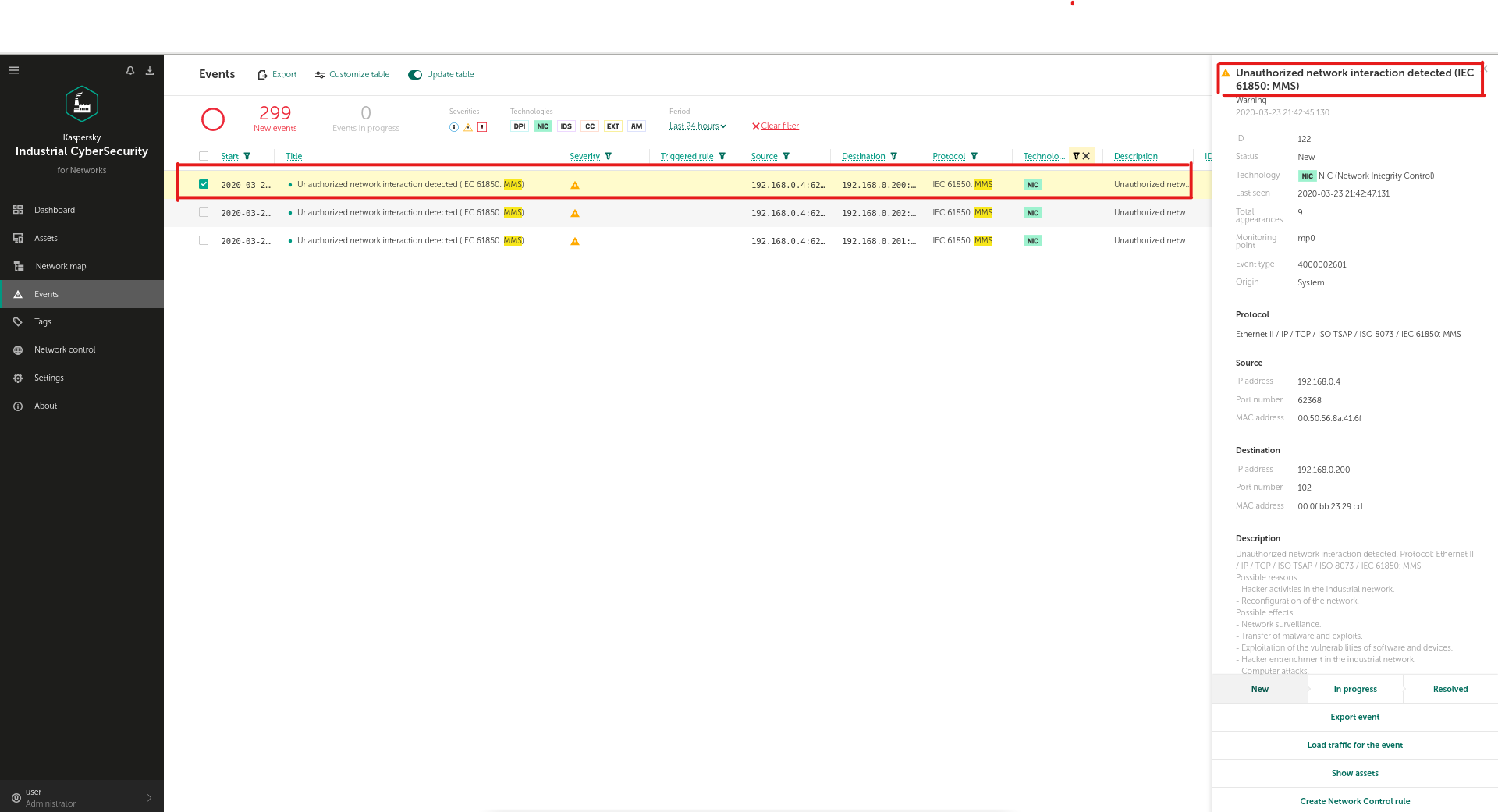
In the early stages of activity, Industroyer may use several reconnaissance techniques to explore the attacked system. For example, the Industroyer IEC 61850 (a special module that works via the IEC 61850 industrial protocol) looks for all connected devices by enumerating all possible IP addresses for each subnet mask for the interfaces on the infected machine, then tries to connect to port 102 on each of those addresses.
In KICS for Networks, this attack technique is detected by the Network Integrity Control (NIC) module. When the security solution is integrated into the client's network, the NIC module defines all the permitted communications, so it can later detect all attempts to violate the established security policy. These violations are detected as ' Unauthorized network interactions”:
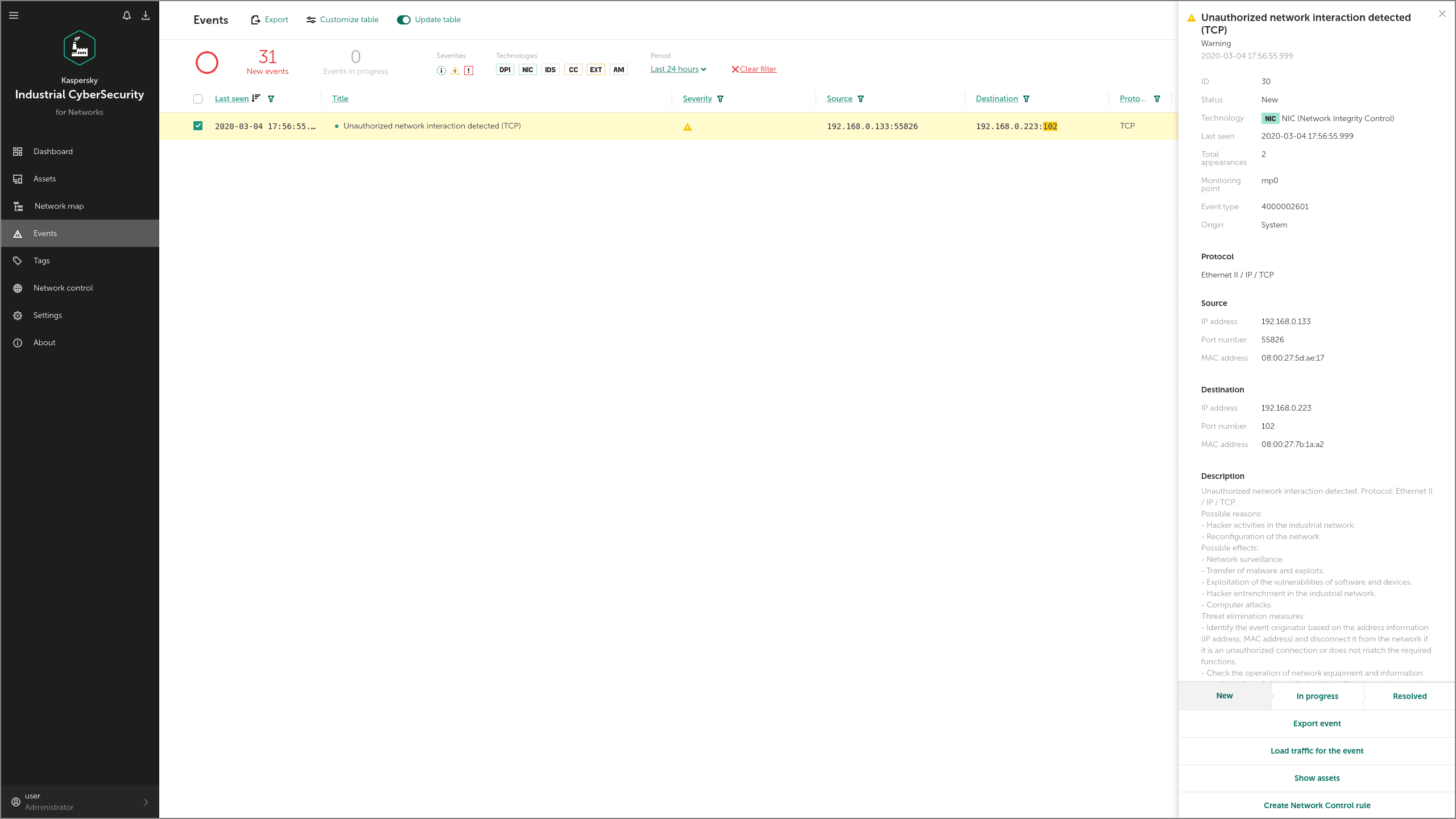
Technique: Control Device Identification (T808)
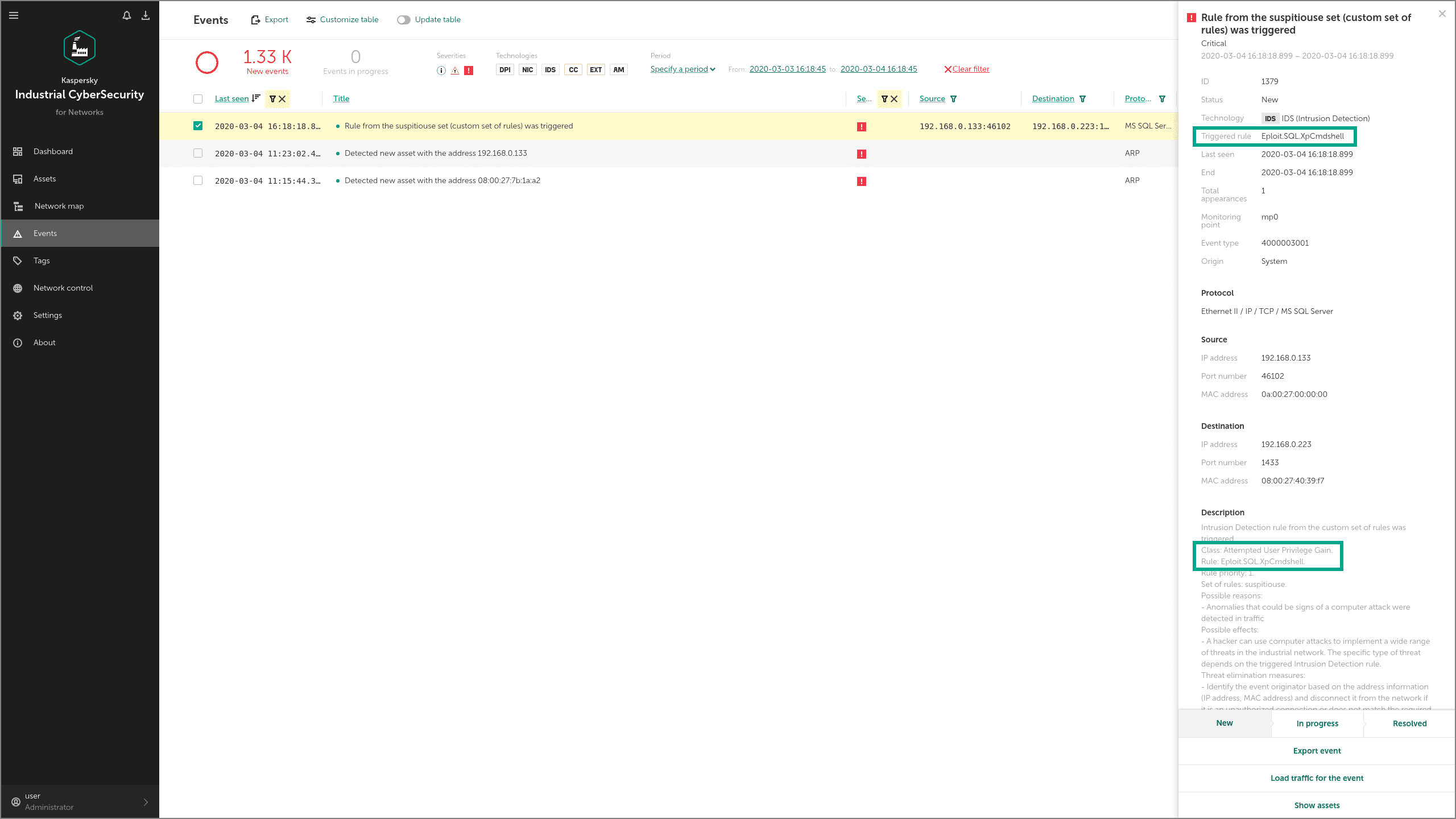
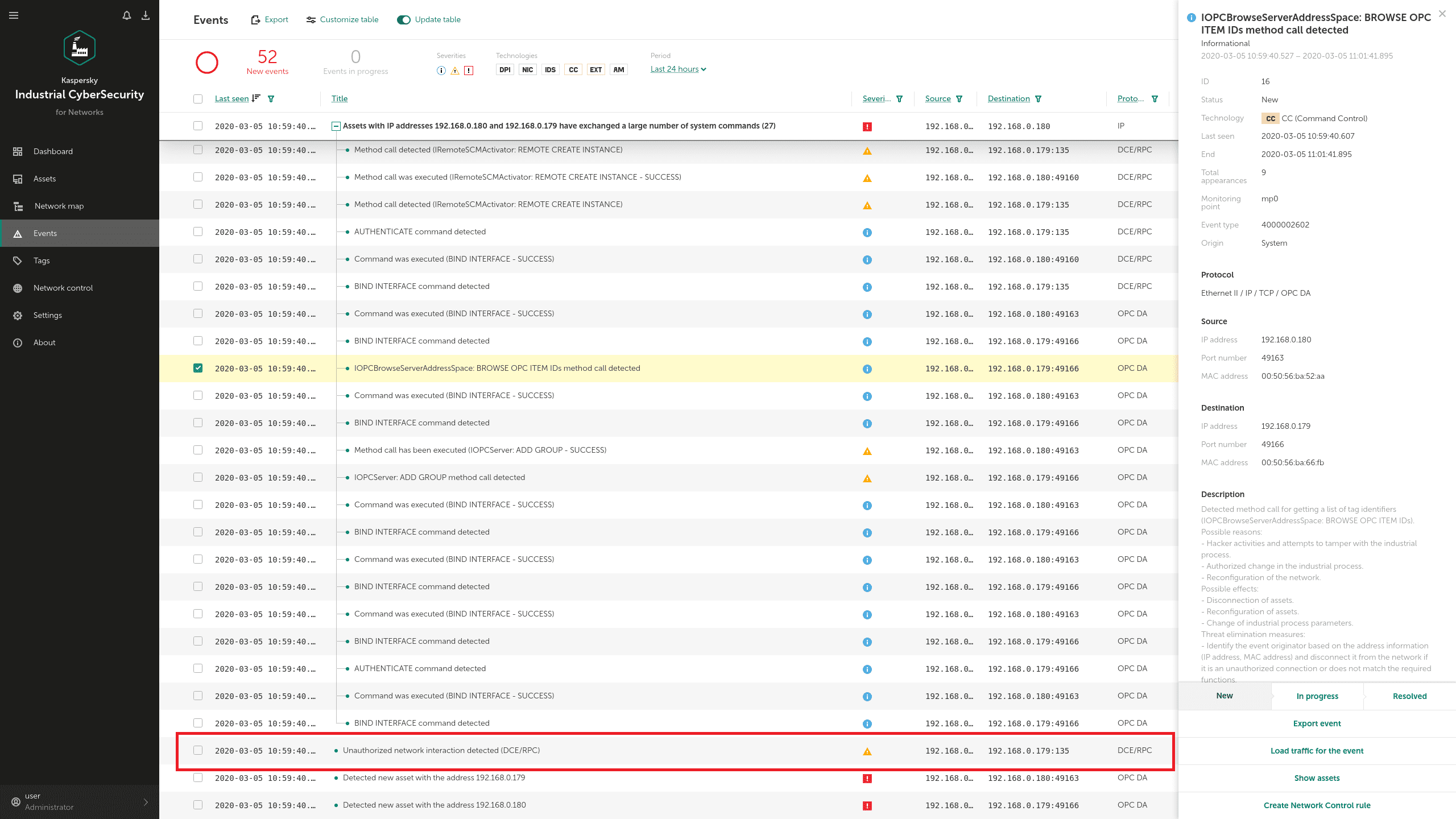
Industroyer contains an OPC DA module that can enumerate all OPC servers, identify those running, and collect additional information about them, for use in subsequent stages of the attack. To obtain this data, the malware uses different OPC protocol commands, such as IOPCBrowseServerAddressSpace.
In KICS for Networks, commands like this are detected on the network layer by the Command Control module and by Network Integrity Control:
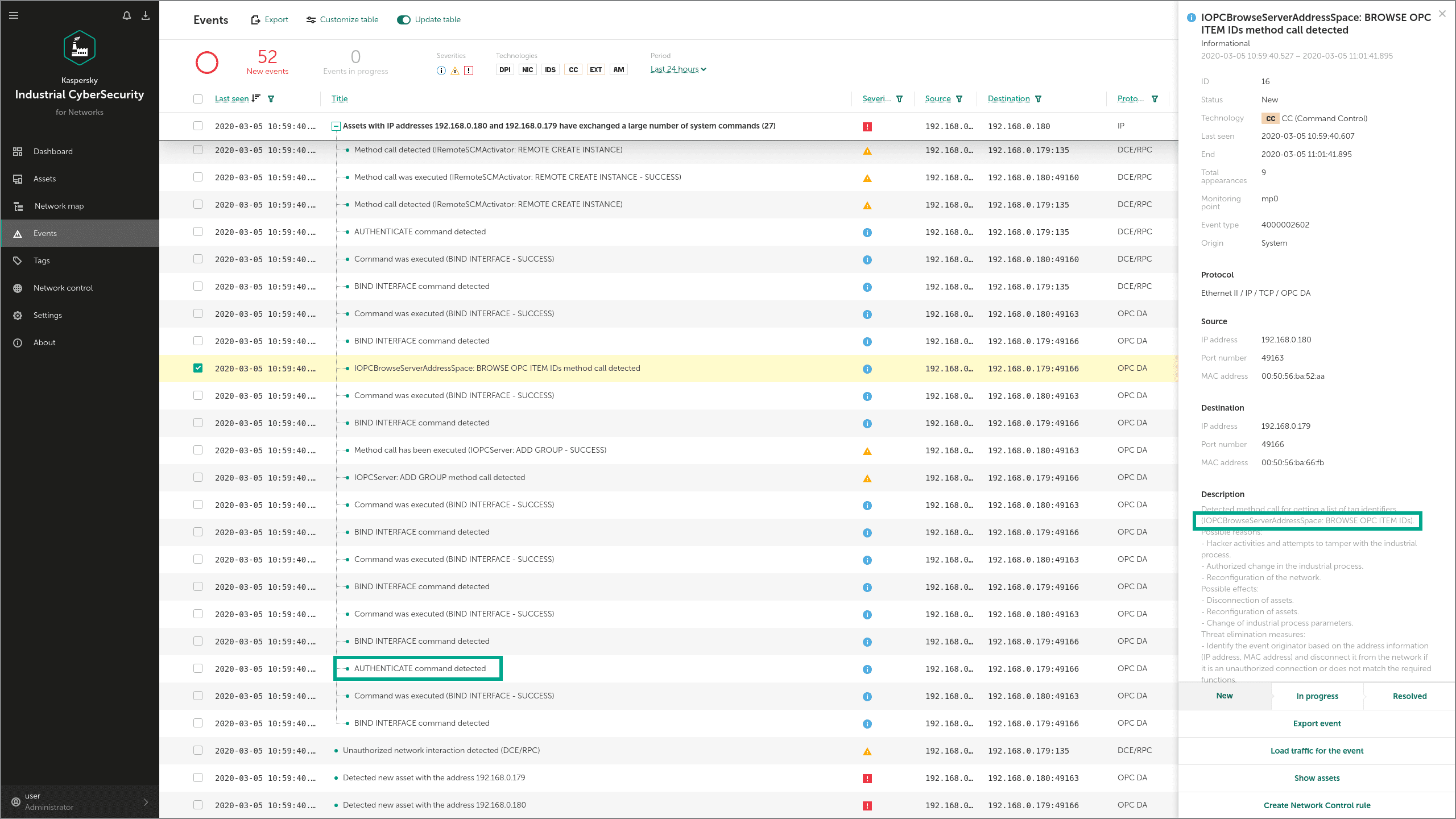
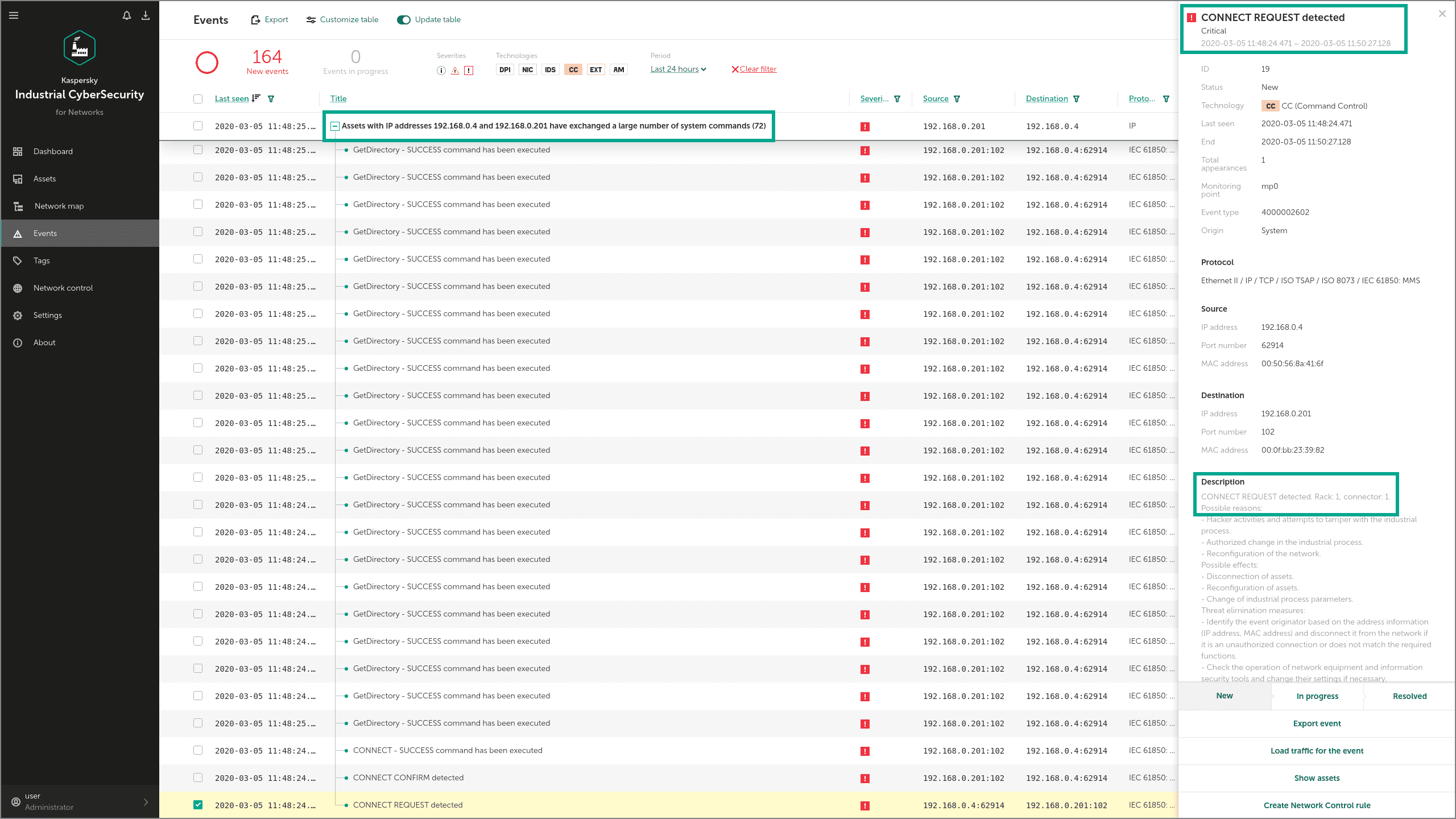
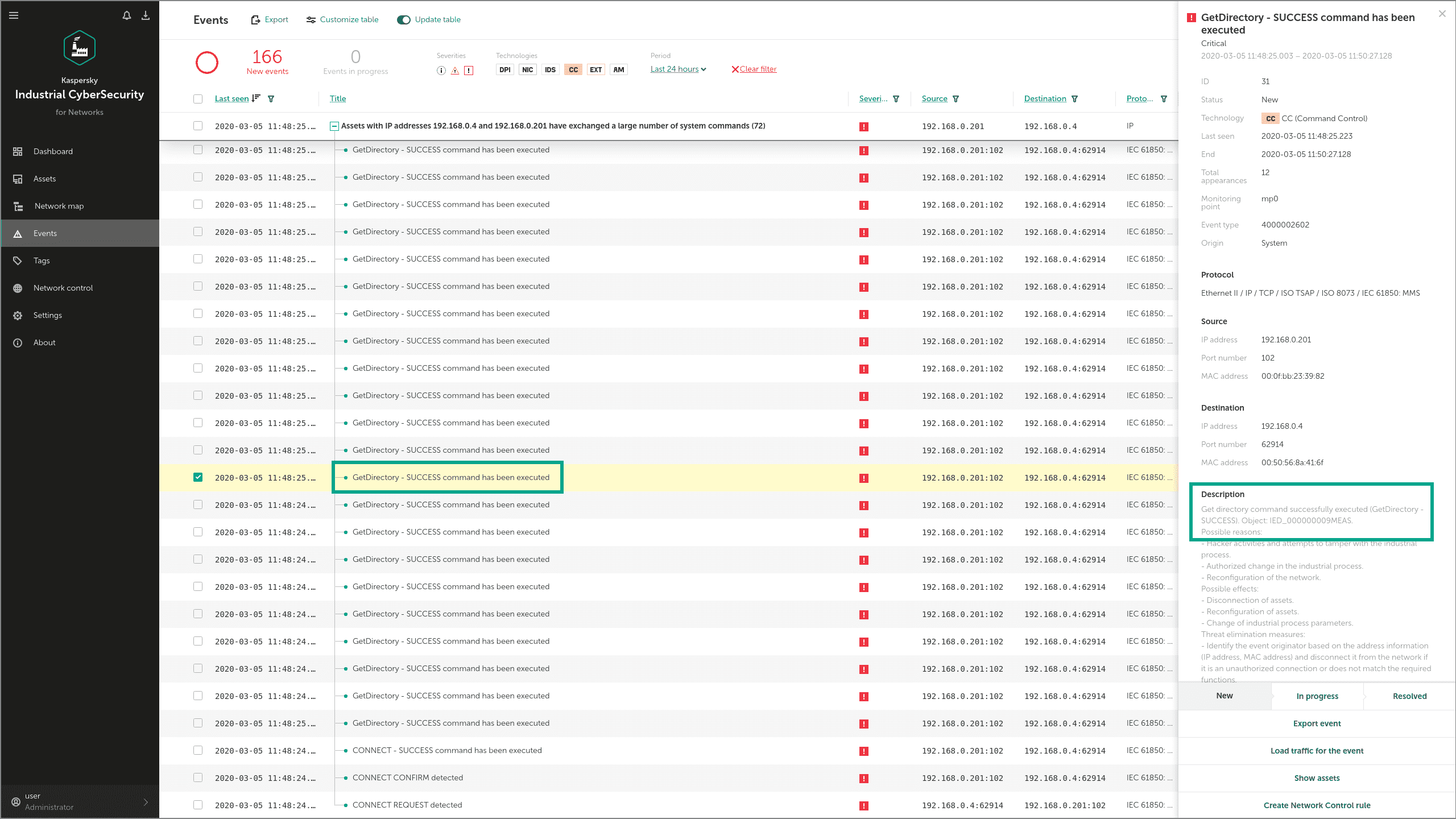
The Industroyer IEC 61850 module can use the MMS (Manufacturing Message Specification) protocol to get more information about the attacked controllers, using requests such as InitiateRequest and getNameList. These MMS requests are also detected by the Command Control and Network Integrity Control modules:
Technique: Serial Connection Enumeration (T854)
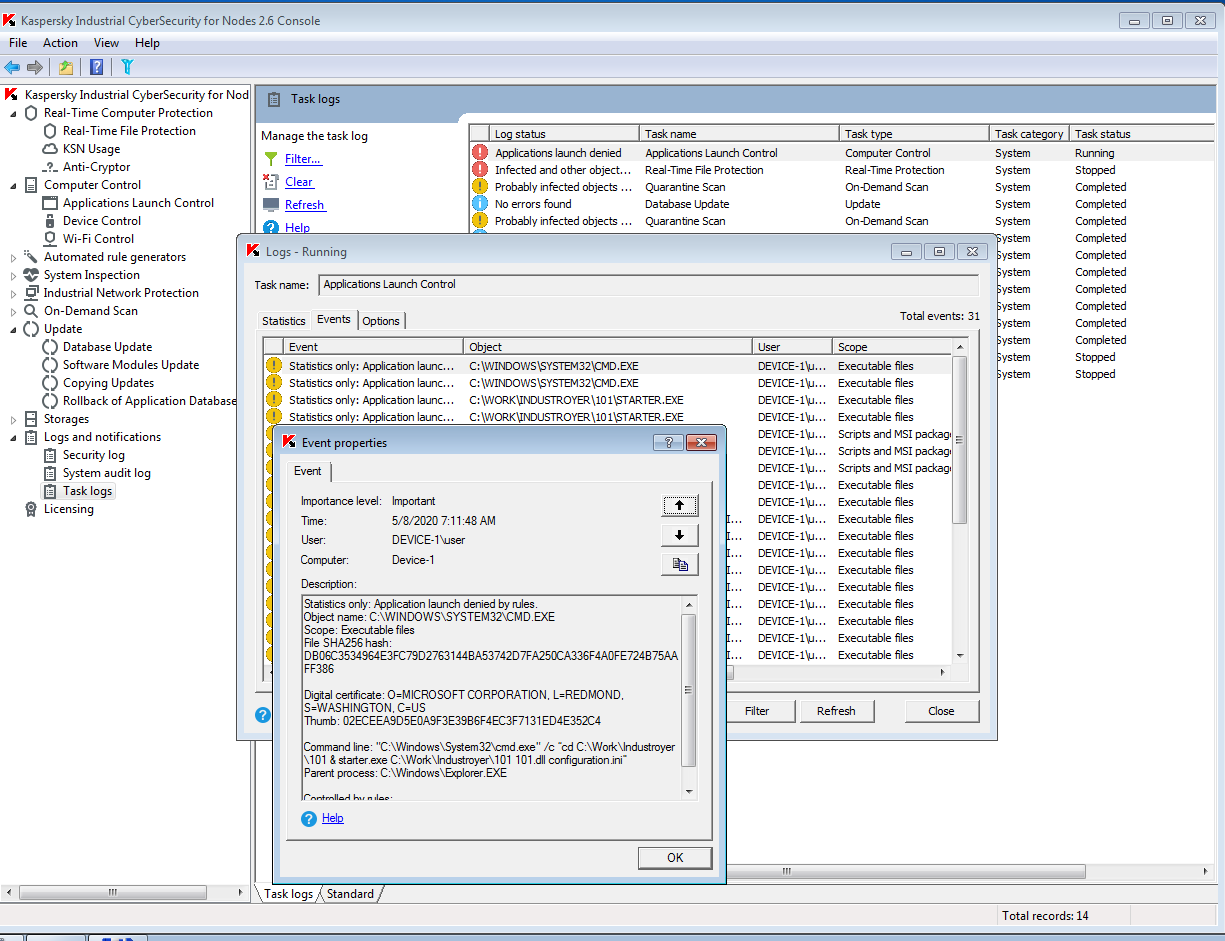
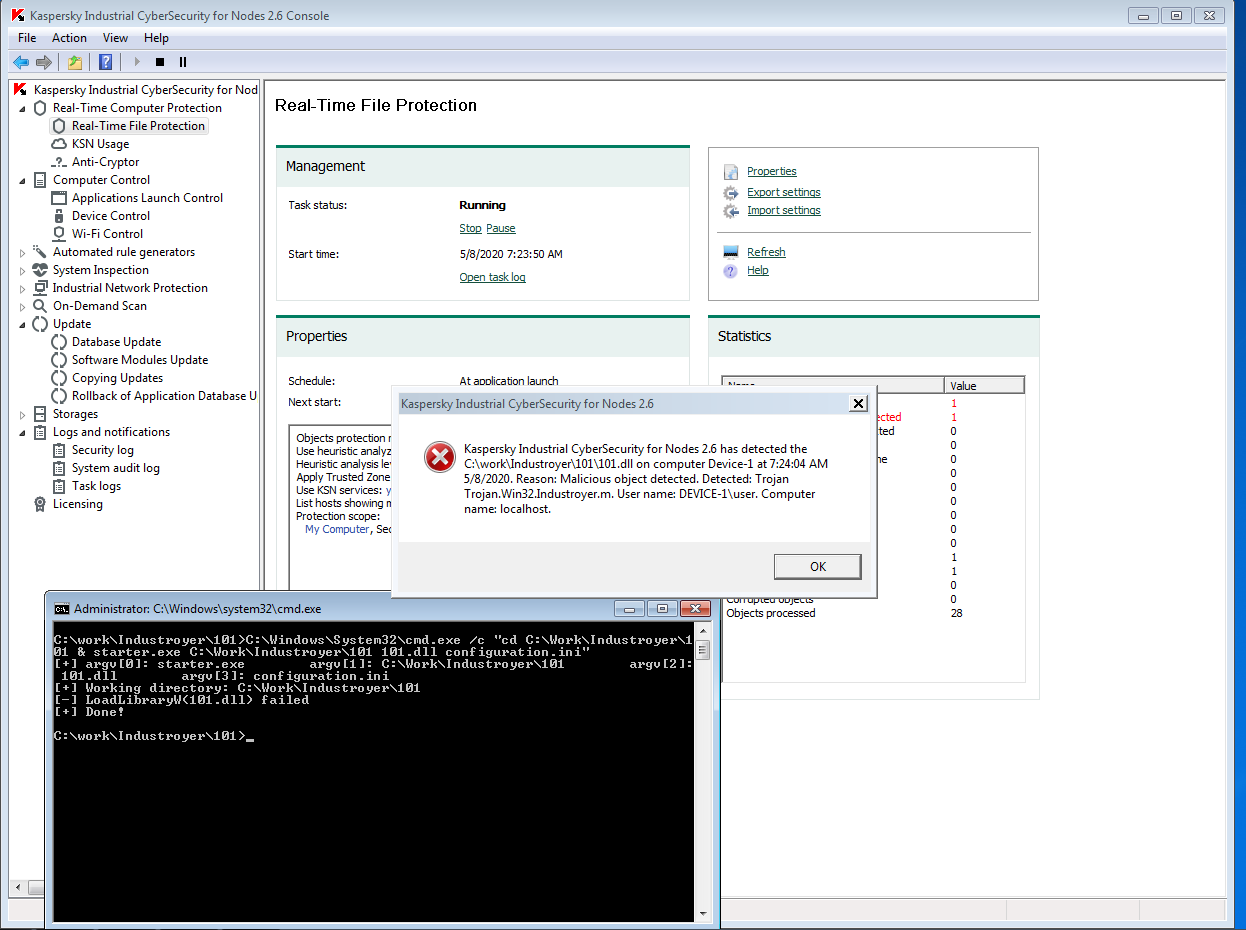
The Industroyer IEC 101 module for attacks via the IEC 60870-5-101 protocol automatically finds a serial port (COM port). This port is used in exclusive mode, so only one application can work with it at a time. This attack technique is detected by KICS modules as they discover the launch of an unauthorized application that implements this method. The malicious app is launched by this command:
C:\Windows\System32\cmd.exe /c “cd C:\Work\Industroyer\101 & starter.exe C:\Work\Industroyer\101 101.dll configuration.ini” |
Events like these are registered by the Application Launch Control module and the Real Time File Protection module (anti-malware module) of KICS for Nodes:
Tactic: Collection
Technique: Role Identification (T850)
By collecting role-based data on devices involved with physical processes, an adversary can launch more targeted attacks. When the Industroyer IEC 61850 discovers accessible devices via the MMS protocol (see above) it sends getNameList requests using each object name, to obtain named variables in a specific domain.
These requests have already been described in the previous section. This technique is detected by KICS for Networks in the same way as shown above in pic. 14 and 15.
Technique: Automated Collection (T802)
In Industroyer, the automated collection of industrial environment information is the same type of event we've seen in previous reconnaissance techniques - Control Device Identification and Role Identification. Industroyer automatically collects object data via the OPC and MMS protocols.
We’ve already demonstrated how KICS for Networks detects these OPC requests (pic.11-12) and MMS requests (pic.13-15), in the Control Device Identification section above.
Tactic: Inhibit Response Function
This group of techniques aims to hinder safeguards put in place for processes and products, preventing alarms and responses to failures, hazards or the unsafe state of the ICS environment.
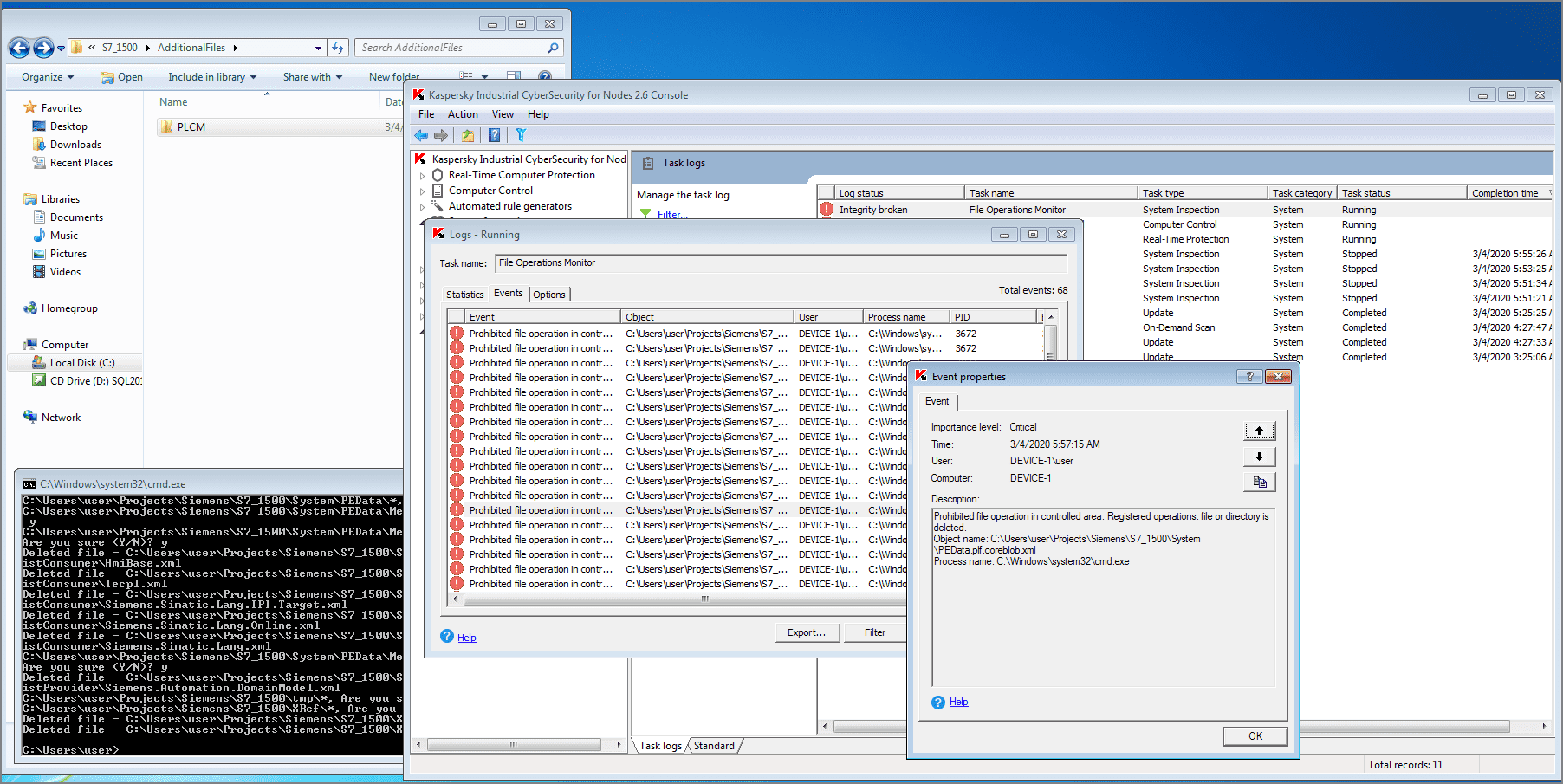
Technique: Data Destruction (T809)
The Data Wiper module of Industroyer can overwrite all configuration files across the infected hosts. To detect and prevent these actions, KICS for Nodes uses a File Operation Monitor module that controls access to critical assets. In the screenshot below, you can see how this module detects an attempt to delete Siemens Tia Portal files:
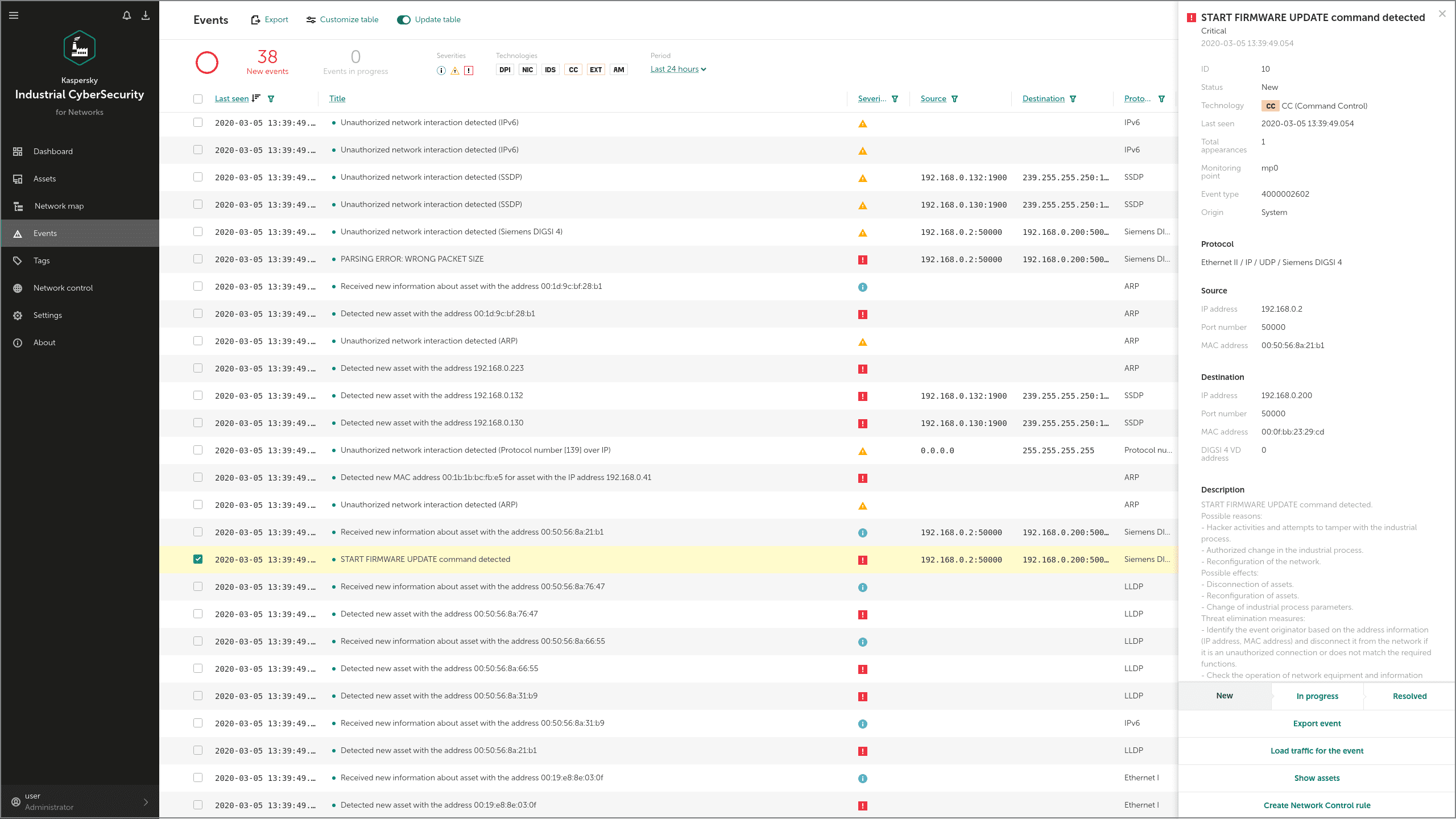
Techniques: Activate Firmware Update Mode (T800), Device Restart/Shutdown (T816) and Denial of Service (T814)
Industroyer can use a specialized exploit to launch a DoS attack on the Siemens SIPROTEC devices widely used in electroenergetics. By exploiting a known vulnerability (CVE-2015-5374) the malware can place the device into “firmware update” mode.
KICS for Networks detects these commands via its IDS and Command Control modules as shown below. In this example, obfuscated IP-addresses are used:
The same CVE-2015-5374 vulnerability can be used by Industroyer to disable Siemens SIPROTEC controllers. KICS for Networks detects this form of attack with the IDS module:
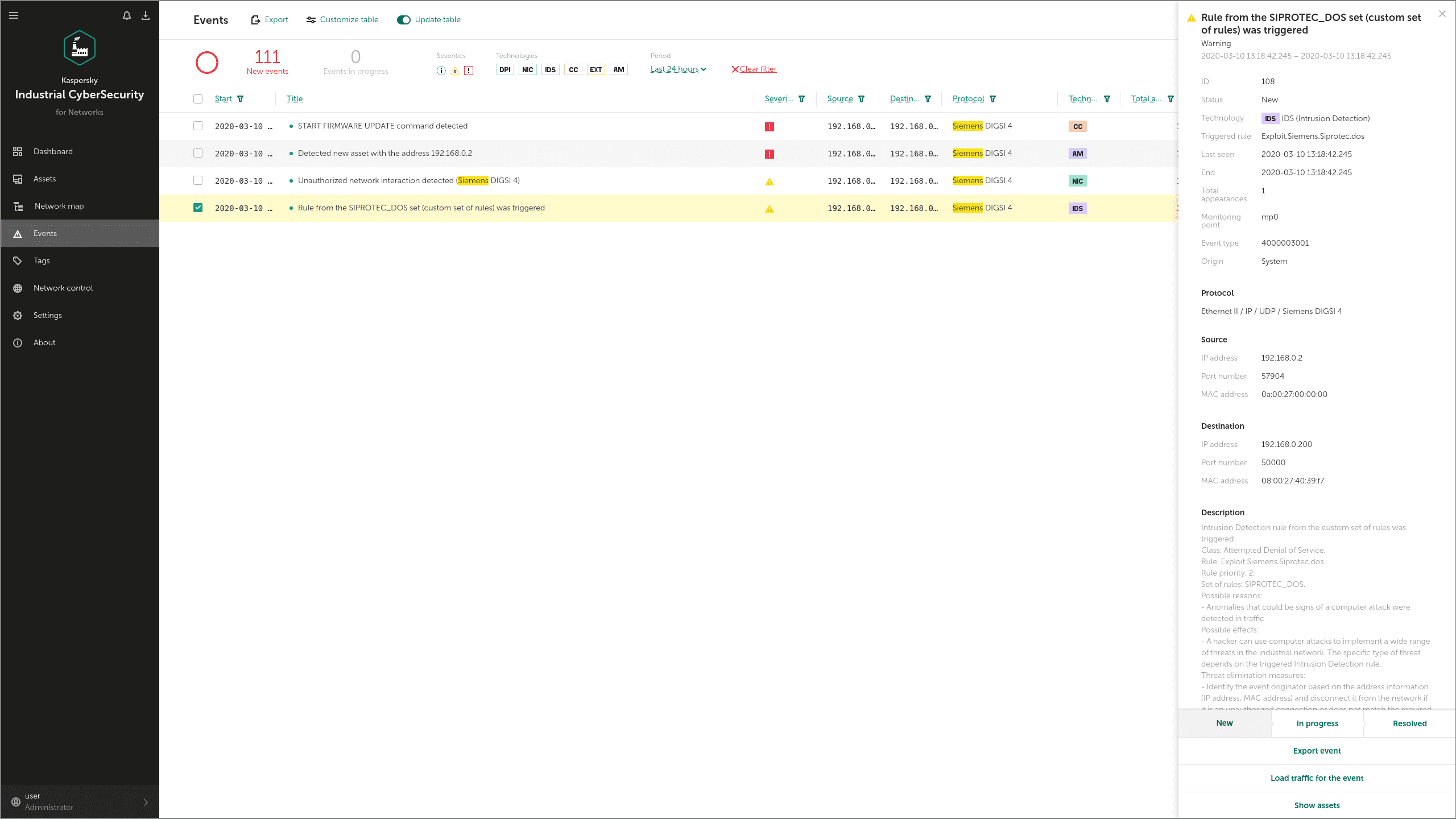
Techniques: Block Command Message (T803), Block Serial COM (T805), Block Reporting Message (T804)
Attack techniques that include manipulations with a serial port (COM) are detected by KICS as the launch of an unauthorized application used in the attack. This approach is based on the fact that as only one application can use a COM port at a time, the Industroyer IEC-101 module first has to stop all the apps that use serial ports - only after this can Industroyer run a malicious app that connects to those ports. These events are detected by the Application Launch Control and the Real Time File Protection modules of KICS for Nodes. You can see how this works in 'Serial Connection Enumeration' section above.
Tactics: Impair Process Control
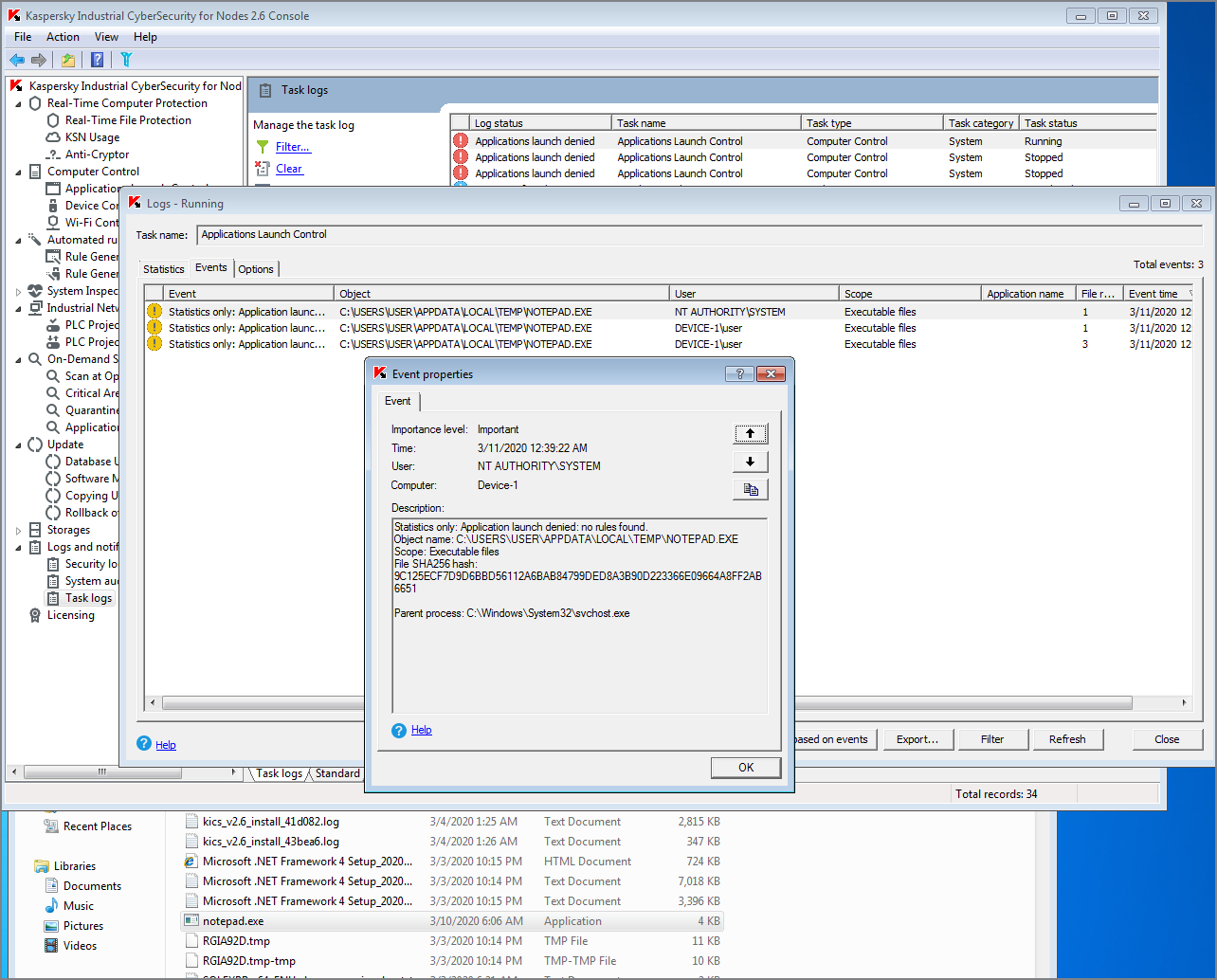
Techniques: Masquerading (T849)
Industroyer can inhibit the normal SCADA primary communication functions and then activate a replacement primary communication module managed by the malware. In our test example, adversaries try to install Industroyer by means of a trojan masquerading as a legitimate Windows application - notepad.exe. KICS for Nodes detects this attempt through its Application Launch Control module:
Technique: Unauthorized Command Message (T855)
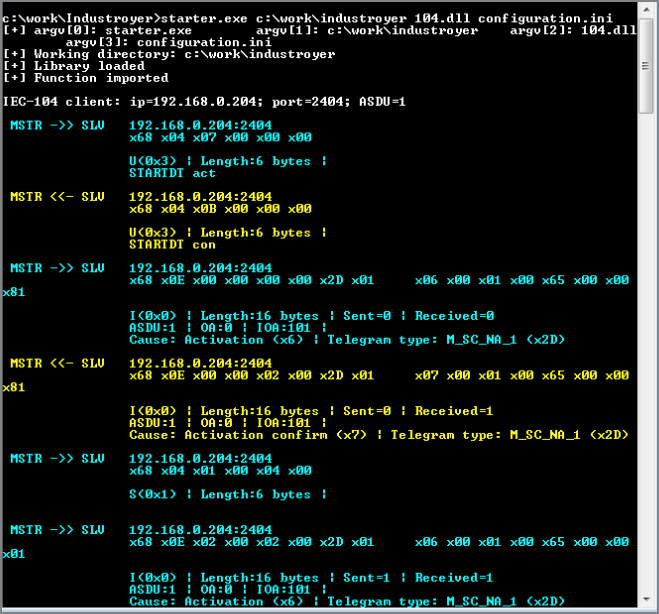
Industroyer can communicate with devices such as PLCs (programmable logic controllers), IEDs (Intelligent Electronic Devices) and RTUs (Remote Terminal Units) via the IEC 60870-5-104 protocol. The malware uses protocol commands to change the state of Information Object Addresses (IOAs) in the attacked devices.
KICS for Networks detects these commands through its Command Control module and informs the operator about the attempt to disrupt a technological process. The main sign of the attack in this case is frequent switching attempts on every IOA.
Let's see how it works. First, the adversary has to launch Industroyer IEC 104:
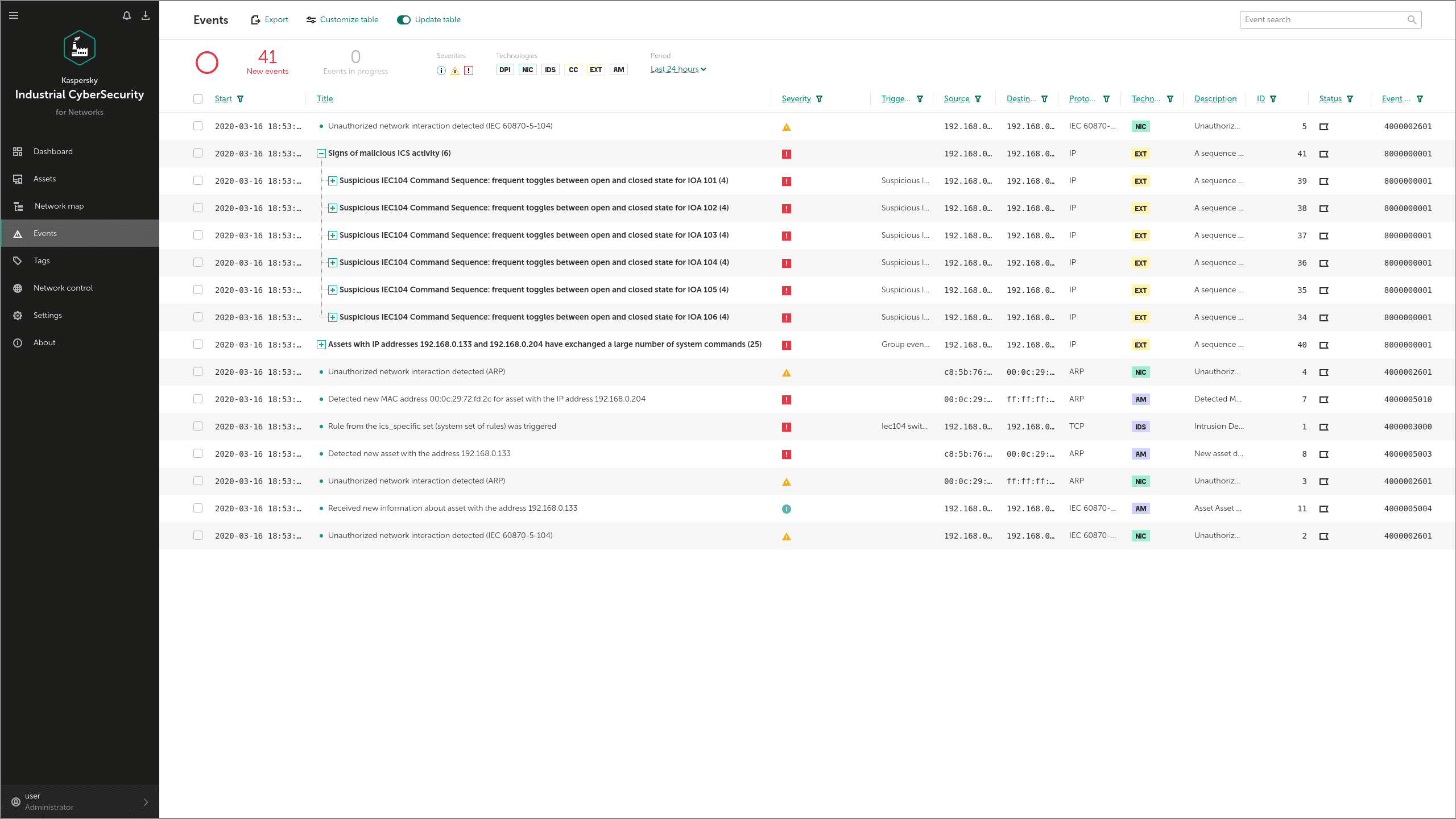
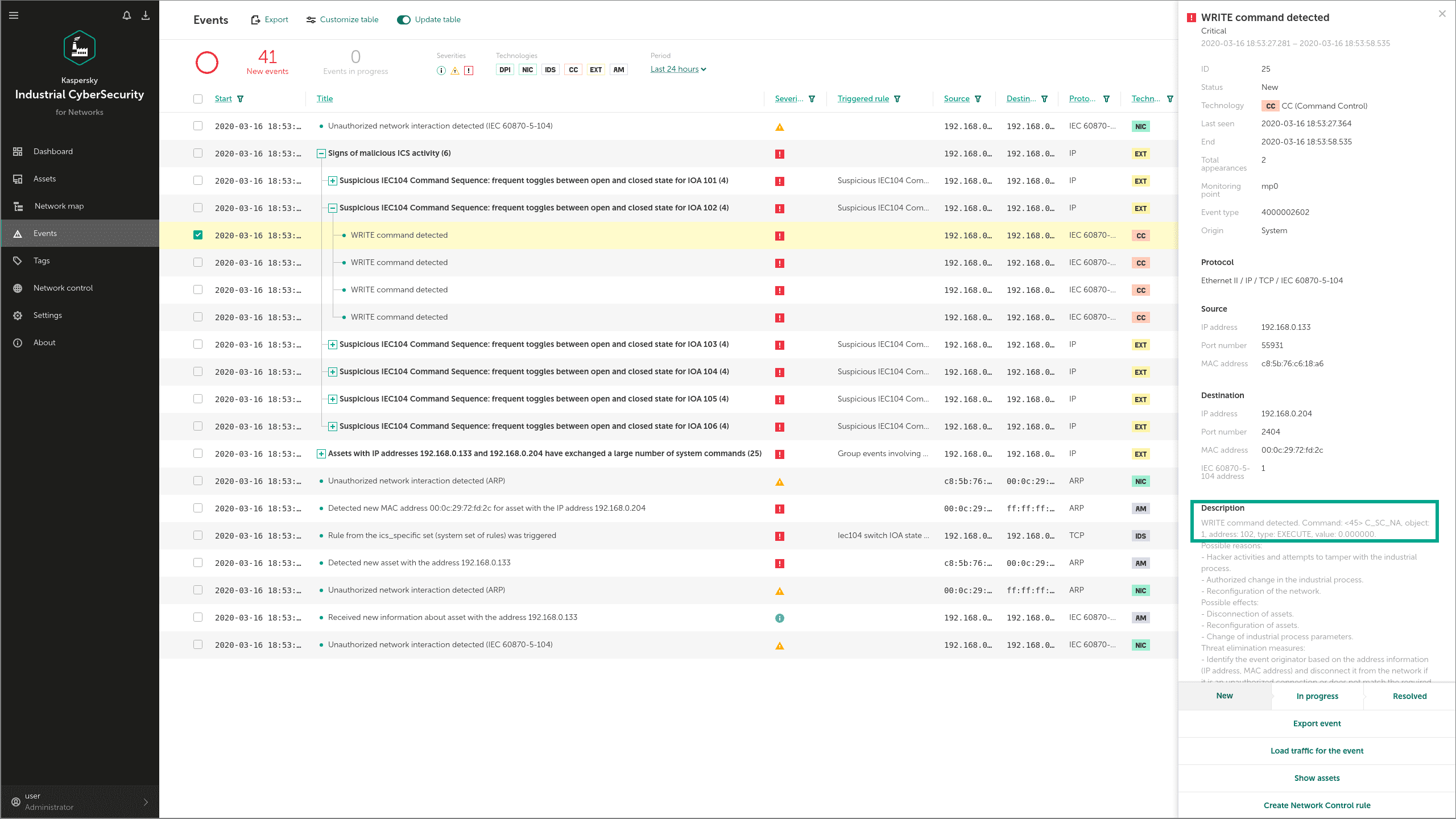
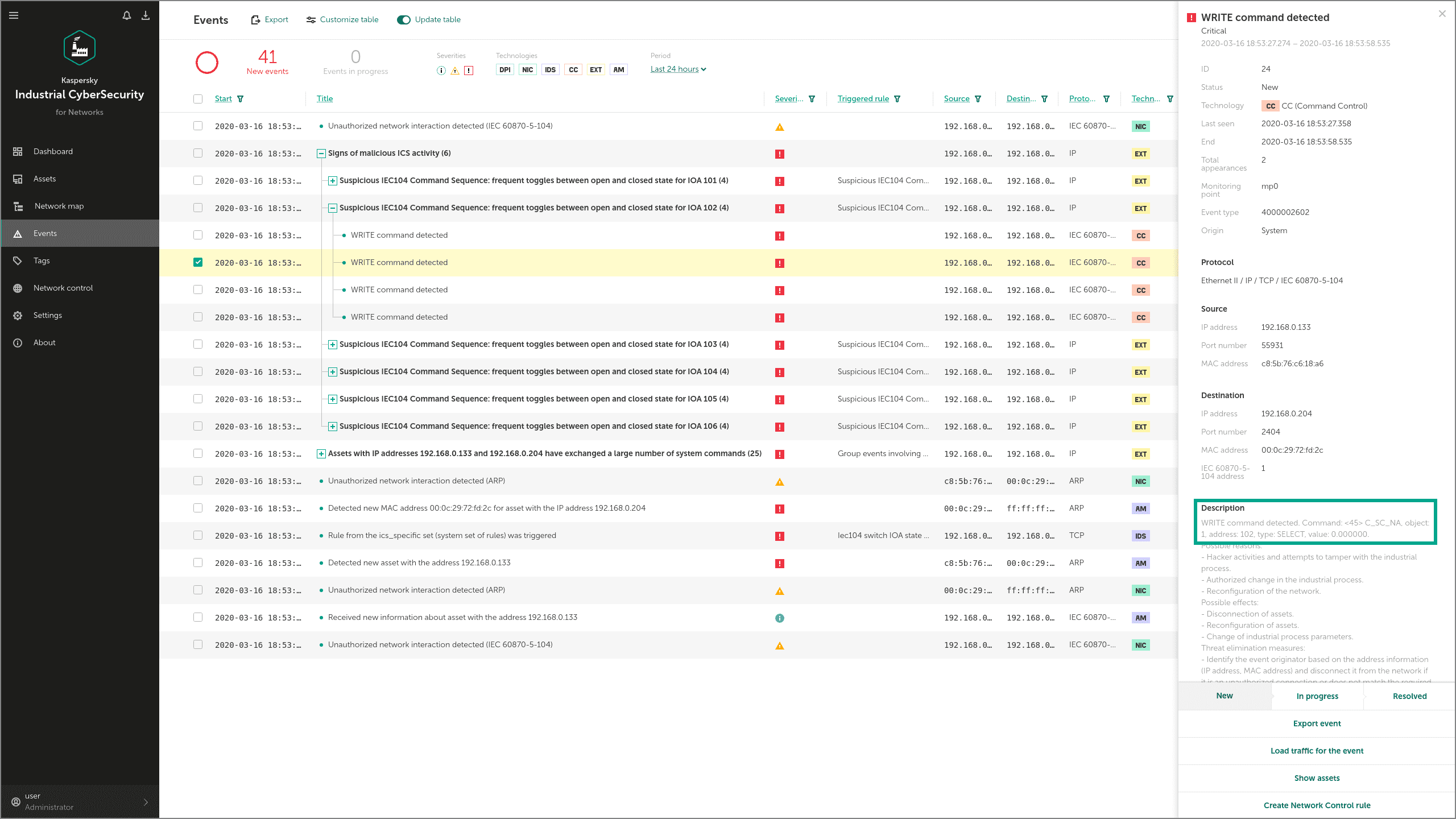
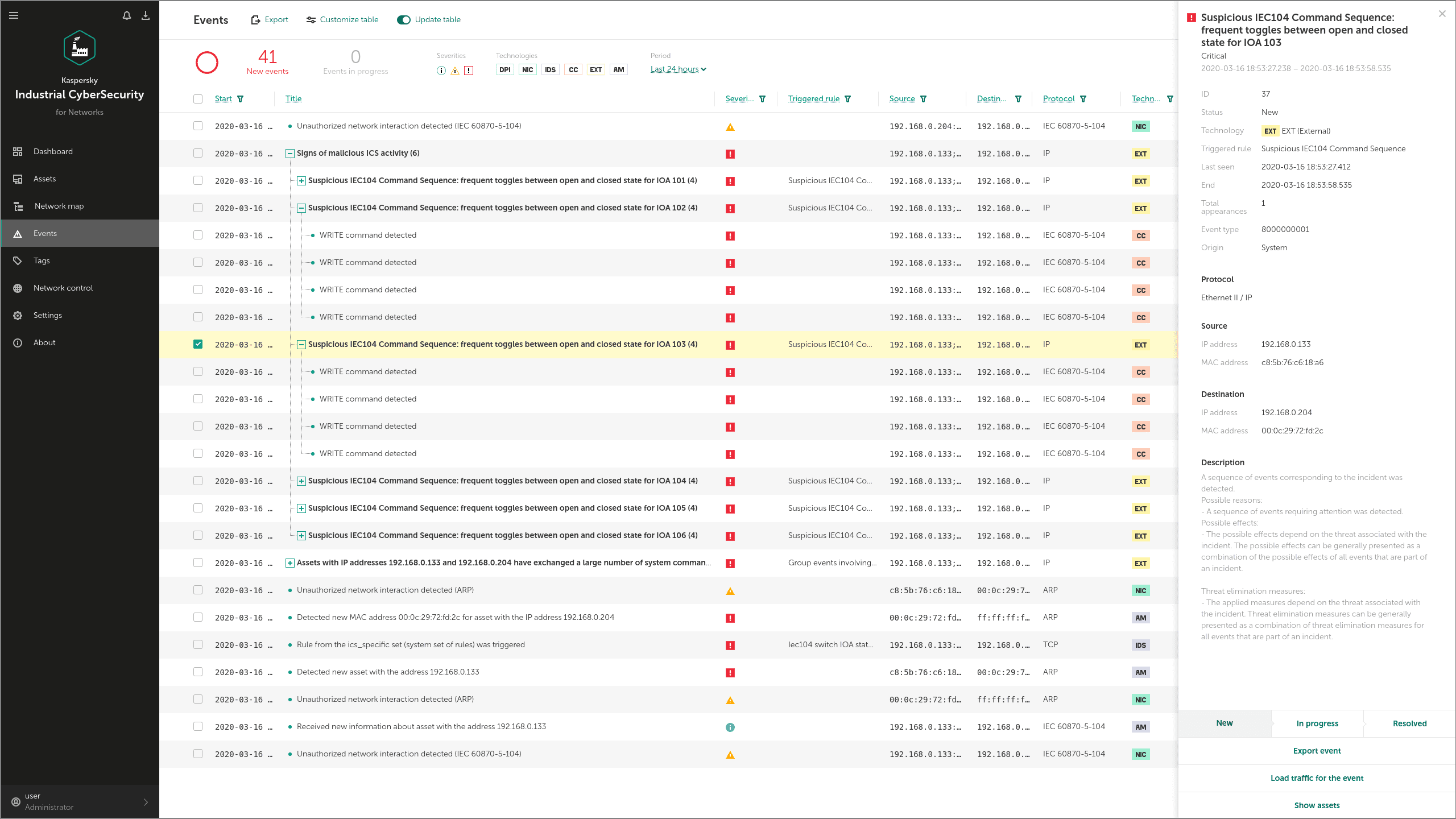
Technique: Brute Force I/O (T806)
In Industroyer, this technique is applied in the same way as for Unauthorized Command Messages above. The Industroyer IEC 104 module looks for valid IOAs and switches their state. Detection is as for Unauthorized Command Messages above.
Technique: Service Stop (T881)
Industroyer has the ability to stop and start services on hosts. KICS for Nodes detects such attempts with its Log Inspection module:
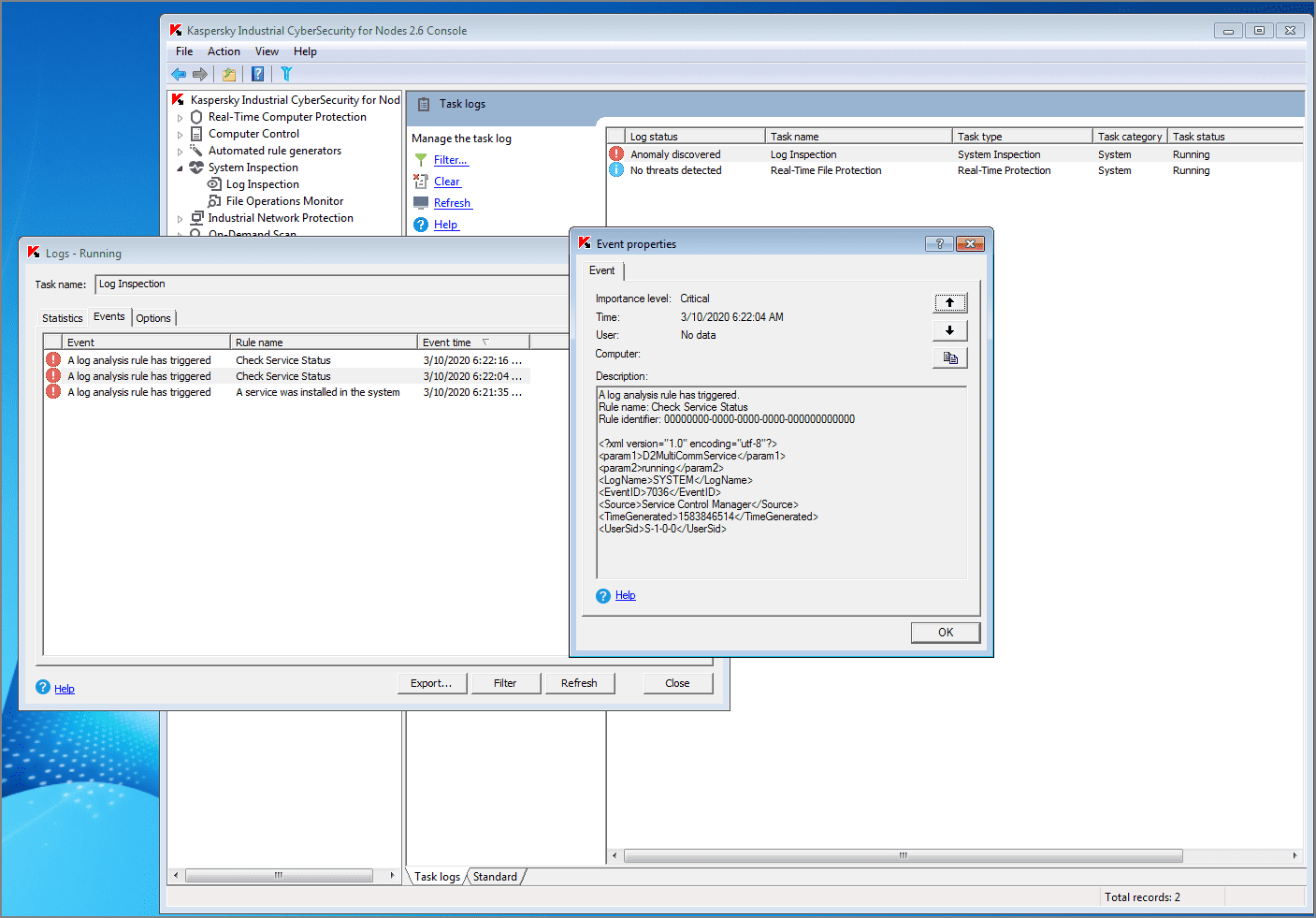
Tactic: Impact
The techniques in this group are used to disrupt, compromise, destroy, and manipulate the integrity and availability of control system processes, devices and data. These attack methods are composite - they include techniques already listed in other tactic groups. For Industroyer specifically, MITRE ATT&CK for ICS names these Impact Techniques:
- Loss of Control (T827). The detection of relevant events by KICS is shown above in the Data Destruction section.
- Loss of View (T829). These detections are also demonstrated in the Data Destruction section.
- Manipulation of Control (T831). Relevant events are detected the same way as Unauthorized Command Message techniques above.
- Manipulation of View (T832). Detection is shown in the Сontrol Device Identification section above.
- Loss of Safety (T880). Detection is shown in the Denial of Service section above.
- Denial of Control (T813). Detection is shown in the Block Serial COM section above.
- Denial of View (T815). Detection is shown in the Block Serial COM section above.
Conclusion
Industroyer is an advanced multi-functional tool for ICS attacks, with a very wide range of capabilities to impact the targeted system. It includes modules for data collection, persistence, masquerading, and the manipulation of different devices controlling critical technological processes. This malware works via different industrial protocols, and, in addition to Ethernet-networked systems, it can attack devices connected via serial ports. Detection of all stages of the Industroyer attack imposes serious demands on ICS security systems.
That's why the MITRE ICS ATT&CK layout for Industroyer provides a great opportunity to evaluate the true capabilities of your ICS security solution. Our tests show that the KICS line of products (KICS for Networks and KICS for Nodes) could successfully defeat Industroyer.
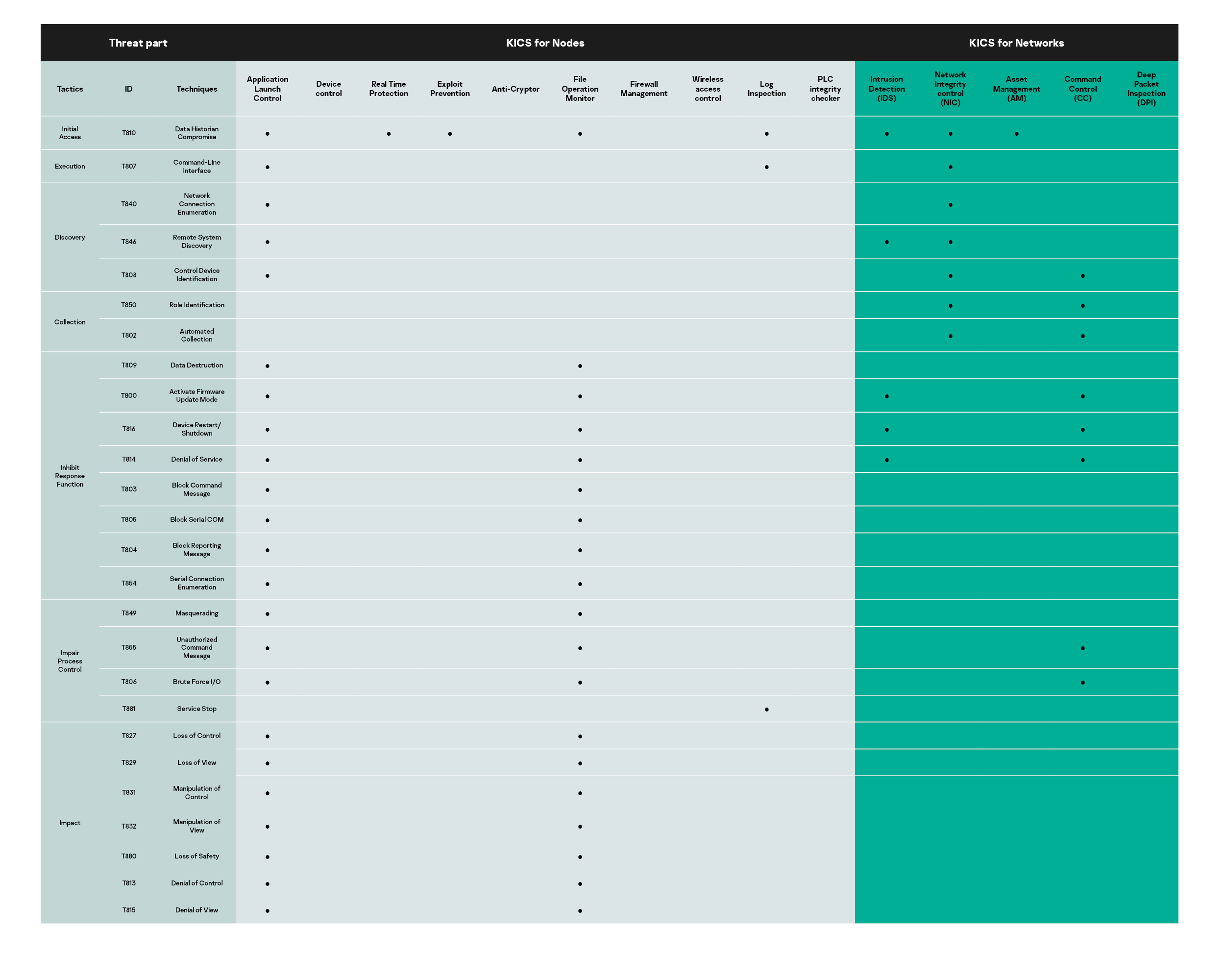
Overall coverage of Industroyer techniques by detection/prevention modules of KICS for Networks and KICS for Nodes is shown in the table below: