Kaspersky Lab announces the discovery of a new cyber-espionage campaign code-named ‘Machete’.
Kaspersky Lab announces the discovery of a new cyber-espionage campaign code-named ‘Machete’. This campaign has been targeting high profile victims, including government, military, law enforcement agencies and embassies for at least four years. The primary field of operation is Latin America: most of the victims appear to be located in Venezuela, Ecuador and Colombia; other affected countries include Russia, Peru, Cuba, and Spain. The objective of the attackers is to hijack sensitive information from the compromised organizations – so far this threat actor has managed to successfully steal gigabytes of confidential data.
“Despite the simplicity of the tools used in this campaign, the results show it was very effective. It looks like threat actors in Latin America are adopting techniques of APT campaigns seen around the world. We expect local cyber-espionage campaigns to reach increased levels of technological sophistication, and it is likely that new APT campaigns will be similar, from a technical point of view, to the top players worldwide. The best advice here is to think about security globally and stop thinking Latin American countries are free of those threats”, said Dmitry Bestuzhev, Head of Kaspersky Lab’s Global Research and Analysis Team, Latin America.
All indications are that the Machete started in 2010 and was updated with renewed infrastructure in 2012. The attackers used social engineering techniques to distribute the malware. In some cases, they used spear-phishing messages combined with web-based infections spread through specially-prepared fake blogs. At the moment, there are no indications of exploits using zero-day vulnerabilities. All the technical artifacts found in this campaign (like cyber-espionage tools and client side code) have rather low technical sophistication in comparison with other targeted campaigns. Despite this simplicity, Kaspersky Lab experts identified 778 victims around the globe.
Based on the evidence uncovered during Kaspersky Lab’s investigation, experts concluded that the attackers of the campaign appear to be Spanish speaking, and have roots somewhere in Latin America. Also, the targets were mostly Latin America countries. When targets outside of the region were found, there was sometimes a link to Latin America. For instance, in Russia the target appeared to be the embassy of one of the Latin America countries.
The cyber-espionage tool found on infected computers is capable of performing various functions and operations, such as copying files to a remote server or a special USB device if inserted, hijacking clipboard content, key logging, computer microphone audio capturing, taking screenshots, getting geolocation data, and taking photos with the web camera on the infected computers.
The campaign has an unusual technical feature: the use of Python language code compiled into Windows executable files. This does not have any advantage for the attackers except ease of coding. The tools show no signs of multi-platform support as the code is heavily Windows-oriented. However, security experts have discovered several clues that suggest the attackers have prepared parallel infrastructures for OSX and Unix victims as well. In addition to Windows components, signs of a mobile component for Android was also discovered.
Kaspersky Lab products identify and protect against this targeted attack.
To learn more about Machete, please read the blog post available at Securelist.com.
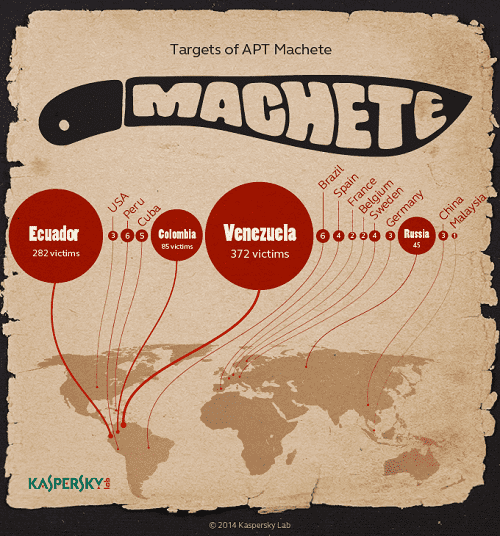
Targets of APT Machete
